NSA’s Secret Toolbox: Unit Offers Spy Gadgets for Every Need
WHISTLEBLOWING - SURVEILLANCE, 6 Jan 2014
Der Spiegel – TRANSCEND Media Service
The NSA has a secret unit that produces special equipment ranging from spyware for computers and cell phones to listening posts and USB sticks that work as bugging devices. Here are some excerpts from the intelligence agency’s own catalog.
Interactive Graphic: The NSA’s Spy Catalog
Editor’s note: This is a sidebar to our main feature story on the NSA’s Tailored Access Operations unit. You can read the main text here .
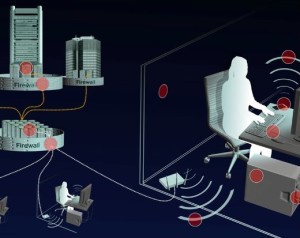
When agents with the NSA’s Tailored Access Operations (TAO) division want to infiltrate a network or a computer, they turn to their technical experts. This particular unit of the United States intelligence service is known internally as ANT. The acronym presumably stands for Advanced Network Technology, because that’s what the division produces — tools for penetrating network equipment and monitoring mobile phones and computers. ANT’s products help TAO agents infiltrate networks and divert or even modify data wherever the NSA’s usual methods won’t suffice. You can read more about the TAO division, its strengths and tricks in a SPIEGEL feature that was published in English on Sunday.
SPIEGEL has obtained an internal NSA catalog describing ANT’s various products, along with their prices. A rigged monitor cable, for example, which allows “TAO personnel to see what is displayed on the targeted monitor,” goes for $30 (€22). An “active GSM base station” that makes it possible to mimic the cell phone tower of a target network and thus monitor mobile phones, is available for $40,000. Computer bugging devices disguised as normal USB plugs, capable of sending and receiving data undetected via radio link, are available in packs of 50, for over $1 million.
Intelligence agencies, incidentally, are not the only ones using these types of devices. The same kind of modified USB plug played a role, for example, in a recent high-tech drug-smuggling case uncovered at the port of Antwerp, Belgium.
Spying on Allies
It has become clear that the ANT arsenal isn’t used exclusively to track suspected terrorists. GSM base stations, for example, make it possible to monitor mobile phones, such as that of German Chancellor Angela Merkel. Radar systems such as the one known as “DROPMIRE” have also been used to spy on allies, for example EU representatives in Washington. And the hardware “implants” found in the ANT catalog evidently have been used, for example, to tap encrypted faxes.
NSA malware has also been used against international telecommunications companies, such as partially state-owned Belgian company Belgacom and mobile phone billing service provider MACH. One internal NSA document dating from 2004 describes a spyware program called “VALIDATOR” by saying that it provides “unique backdoor access to personal computers of targets of national interest, including but not limited to terrorist targets.”
In the graphic in this article, you can browse nearly 50 pages from the ANT catalog, sorted by where these devices would potentially be used and purged of the names and email addresses of agents. There are “implants,” as the NSA calls them, for computers, servers, routers and hardware firewalls. There is special equipment for covertly viewing everything displayed on a targeted individual’s monitor. And there are bugging devices that can conduct surveillance without sending out any measurable radio signal — their signals are instead picked up using radar waves. Many of these items are designed for subverting the technical infrastructure of telecommunications companies to exploit them, undetected, for the NSA’s purposes, or for tapping into company networks.
Spyware for mobile phones was even on offer in the 2008 version of the catalog. A Trojan for gaining total access to iPhones, which were still new at the time, was still in development, though its specifications are listed in the catalog.
‘Implants’ for Cisco, Juniper, Dell, Huawei and HP
The catalog is not up to date. Many of the software solutions on offer date from 2008, some apply to server systems or mobile phone models no longer on the market, and it is very likely that the portions SPIEGEL has seen are far from complete. And yet this version still provides considerable insight both into the tools the NSA has had at its disposal for years and into the agency’s boundless ambitions. It is safe to assume that ANT’s hackers are constantly improving their arsenal. Indeed, the catalog makes frequent mention of other systems that will be “pursued for a future release.”
The NSA has also targeted products made by well-known American manufacturers and found ways to break into professional-grade routers and hardware firewalls, such as those used by Internet and mobile phone operators. ANT offers malware and hardware for use on computers made by Cisco, Dell, Juniper, Hewlett-Packard and Chinese company Huawei.
There is no information in the documents seen by SPIEGEL to suggest that the companies whose products are mentioned in the catalog provided any support to the NSA or even had any knowledge of the intelligence solutions. “Cisco does not work with any government to modify our equipment, nor to implement any so-called security ‘back doors’ in our products,” the company said in a statement. The company has also since commented on SPIEGEL’s intitial reporting on a Cisco blog. “We are deeply concerned with anything that may impact the integrity of our products or our customers’ networks and continue to seek additional information,” the company wrote.
A representative of Hewlett-Packard wrote that the company was not aware of any of the information presented in the report and that it did “not believe any of it to be true.” Contacted by SPIEGEL reporters, officials at Juniper Networks and Huawei also said they had no knowledge of any such modifications. Meanwhile, Dell officials said the company “respects and complies with the laws of all countries in which it operates.”
TAO’s implants, in place around the world, have played a significant role in the NSA’s ability to establish a global covert network consisting partly of the agency’s own hardware, but also of other computers subverted to serve its purposes.
Photo Gallery: NSA’s TAO Unit Introduces Itself
Intercepting Packages and Manipulating Computers
ANT’s developers often seek to place their malicious code in BIOS, software located directly on a computer’s motherboard that is the first thing to load when the computer is turned on. Even if the hard drive is wiped and a new operating system installed, ANT’s malware continues to function, making it possible to later add other spyware back onto the computer.
Along with the BIOS software of computers and servers, the NSA’s hackers also attack firmware on computer hard drives, essentially the software that makes the hardware work. The ANT catalog includes, for example, spyware capable of embedding itself unnoticed into hard drives manufactured by Western Digital, Seagate and Samsung. The first two of these are American companies.
Many of these digital tools are “remotely installable,” meaning they can be put in place over the Internet. Others, however, require direct intervention, known in NSA jargon as “interdiction.” This means that brand new products being delivered by mail are secretly intercepted, and hardware or software implants installed on them. The package is forwarded to its intended destination only after this has been done.
Windows Error Messages Potential Sources of Information
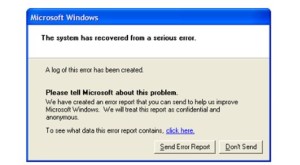
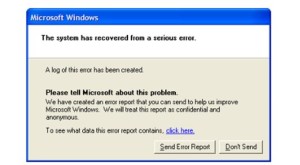
One example of the creativity with which the TAO spies approach their work can be seen in a hacking method that exploits frequent errors on Microsoft Windows. Every user of the operating system is familiar with the window that pops up on screen when an internal problem is detected, asking the user to report the error to Microsoft with a click of the mouse. The window promises this communication will be “confidential and anonymous.”
For TAO specialists, these crash reports either were or continue to be a welcome source of potential information. When TAO selects a computer somewhere in the world as a target and enters its unique identifiers (an IP address, for example) into the corresponding database, intelligence agents are then automatically notified any time the operating system of that computer crashes and its user receives the prompt to report the problem to Microsoft.
The automated crash reports are a “neat way” to gain “passive access” to a targeted machine, the presentation continues. Passive access means that, initially, only data the computer sends out into the Internet is captured and saved, but the computer itself is not yet manipulated. Still, even this passive access to error messages provides valuable insights into problems with a targeted person’s computer and, thus, information on security holes that might be exploitable for planting malware or spyware on the unwitting victim’s computer.
Although the method appears to have little importance in practical terms, the NSA’s agents still seem to enjoy it because it allows them to have a bit of a laugh at the expense of the Seattle-based software giant. In one internal graphic, they replaced the text of Microsoft’s original error message with one of their own reading, “This information may be intercepted by a foreign sigint system to gather detailed information and better exploit your machine.” (“Sigint” stands for “signals intelligence.”)
In response to a query from SPIEGEL, NSA officials issued a statement saying, “Tailored Access Operations is a unique national asset that is on the front lines of enabling NSA to defend the nation and its allies.” The statement added that TAO’s “work is centered on computer network exploitation in support of foreign intelligence collection.” The officials said they would not discuss specific allegations regarding TAO’s mission.
One trail also leads to Germany. According to a document dating from 2010 that lists the “Lead TAO Liaisons” domestically and abroad as well as names, email addresses and the number for their “Secure Phone,” a liaison office is located near Frankfurt — the European Security Operations Center (ESOC) at the so-called “Dagger Complex” at a US military compound in the Griesheim suburb of Darmstadt.
______________________
Jacob Appelbaum, Judith Horchert, Ole Reissmann, Marcel Rosenbach, Jörg Schindler and Christian Stöcker. With additional reporting by Andy Müller-Maguhn.
DISCLAIMER: The statements, views and opinions expressed in pieces republished here are solely those of the authors and do not necessarily represent those of TMS. In accordance with title 17 U.S.C. section 107, this material is distributed without profit to those who have expressed a prior interest in receiving the included information for research and educational purposes. TMS has no affiliation whatsoever with the originator of this article nor is TMS endorsed or sponsored by the originator. “GO TO ORIGINAL” links are provided as a convenience to our readers and allow for verification of authenticity. However, as originating pages are often updated by their originating host sites, the versions posted may not match the versions our readers view when clicking the “GO TO ORIGINAL” links. This site contains copyrighted material the use of which has not always been specifically authorized by the copyright owner. We are making such material available in our efforts to advance understanding of environmental, political, human rights, economic, democracy, scientific, and social justice issues, etc. We believe this constitutes a ‘fair use’ of any such copyrighted material as provided for in section 107 of the US Copyright Law. In accordance with Title 17 U.S.C. Section 107, the material on this site is distributed without profit to those who have expressed a prior interest in receiving the included information for research and educational purposes. For more information go to: http://www.law.cornell.edu/uscode/17/107.shtml. If you wish to use copyrighted material from this site for purposes of your own that go beyond ‘fair use’, you must obtain permission from the copyright owner.
Read more
Click here to go to the current weekly digest or pick another article:
WHISTLEBLOWING - SURVEILLANCE: