For US$ 20M, These Israeli Hackers Will Spy on Any Phone on the Planet
WHISTLEBLOWING - SURVEILLANCE, 6 Jun 2016
![]() 31 May 2016 – With just a few million dollars and a phone number, you can snoop on any call or text that phone makes – no matter where you are or where the device is located.
31 May 2016 – With just a few million dollars and a phone number, you can snoop on any call or text that phone makes – no matter where you are or where the device is located.
That’s the bold claim of Israel’s Ability Inc, which offers its set of bleeding-edge spy tools to governments the world over. And it’s plotting to flog its kit to American cops in the coming months.
Unlimited spying
Ability’s most startling product, from both technical and price perspectives, is the Unlimited Interception System (ULIN). Launched in November last year, it can cost as much as $20 million, depending on how many targets the customer wants to surveil. All a ULIN customer requires is the target’s phone number or the IMSI (International Mobile Subscriber Identity), the unique identifier for an individual mobile device. Got those? Then boom – you can spy on a target’s location, calls and texts.
This capability is far more advanced than that of IMSI-catchers (widely known as StingRays), currently used by police departments in the United States. IMSI-catchers can help acquire a target’s IMSI number, as well as snoop on mobiles, but only if the target is within range.
ULIN has no such geographic limitation. A quarterly update document posted only on May 2, spells out the tech’s power: “ULIN enables interception of voice calls, SMS messages and call-related information of GSM/UMTS/LTE phones, without the need to be close to the intercepted phone and without the consent of mobile network operators [emphasis by FORBES] and requires only the mobile device’s phone number or IMSI. Customers can use ULIN to intercept calls, and gather other information, from anywhere in the world.”

Anatoly Hurgin, CEO and co-founder of Ability, provider of cutting-edge surveillance technology. He gave FORBES a rare interview about a tool that exploits weaknesses in global telecoms infrastructure. Image from Anatoly Hurgin’s Google+ account.
Ability’s service – it is the sole licensee from an unknown third party – exploits a weakness resident in SS7, the Signalling System No. 7. A core part of the world’s shared networking infrastructure, SS7 helps route calls between different carriers and switching centers. Service providers often use SS7 to support communications in areas where the customer’s normal network isn’t available, such as when the user is abroad. For instance, when a Verizon user is holidaying in Spain, local carriers will use SS7 to “speak” with the customer’s operator to determine who provides its service.
Hackers, however, use weaknesses in the SS7 network for a number of nefarious purposes. For instance, to forward calls heading to voicemail to their own devices. They can do this because wireless networks do not have the necessary safeguards to block these attacks. Concerns around SS7 have led House Democrat Ted Lieu to demand a Congressional investigation and the Federal Communications Commission has launched its own probe.
Previously, government contractors selling SS7 exploitation tools had to work with wireless service providers to access the SS7 network. These tools, according to a Washington Post report in 2014, were only able to detect users’ locations, not intercept communication. Ability, however, can do much more.
According to documents seen by FORBES, one of which was leaked by an anonymous source (published below and on Document Cloud), Ability’s ULIN service allows it to locate targets and snoop on calls and texts – without any assistance from the cellular networks. According to whitehat hacker Drew Porter from security consultancy Red Mesa, this is technically feasible, and could be done in two ways: by hacking the SS7 network or by leasing a system from a carrier that has the ability to “talk” to large parts of the network.
Porter noted the first option is “preferred because you really don’t need any carrier cooperation.” The second would require some kind of contract, which would be “less ideal,” he added, as it may allow interested parties to trace the interception back to the true spy or surveillance vendor. Ability could also have built its own infrastructure that can send messages across the network.
Regardless of how Ability is able to spy on mobiles over SS7, it has its hands on a powerful product. Direct hacks on mobile devices typically require the use of malware and exploitation of software vulnerabilities – themselves a costly commodity – and run the risk of detection. Accessing a mobile device through SS7, however, can provide access to much of the same information with little danger of detection by the target.
“Having access to SS7 is really a golden key of surveillance, I’m not surprised [Ability] capitalized on it,” said Claudio Guarnieri, a security and human rights advocate who this week helped launch a map of attacks on journalists and activists, as well as the surveillance vendors facilitating global spying. He plans to add Ability to the map this week.
Karsten Nohl, a German whitehat hacker from Security Research Labs who has frequently highlighted security shortcomings in SS7, said the intercept capabilities that SS7 provides “are probably the most powerful currently available.”
For privacy activists, this is a real concern. “Our devices, services and national and international communications infrastructure should be safe and not betray us in this manner,” said Privacy International technologist Dr. Richard Tynan. “This is particularly concerning as most countries’ laws discriminate against foreigners and provide a lower standard of protection when it comes to surveillance. Any country that purchases or makes surveillance equipment must be aware that their citizens are also vulnerable to the very same kit used by someone else; yet they seem to choose their offensive capabilities over our safety time and time again without any apparent mandate from the public for doing so.”
SS7 exploit services have created anxieties around a lack of oversight over their use. Until last year, cops in the United States used Stingrays without warrants. Following complaints from civil rights bodies, the Department of Justice mandated warrants, but the invasive tool had already been deployed and the damage done.
The same could happen with tools like ULIN, warned Nathan Wessler, staff attorney at the American Civil Liberties Union. “This system means that law enforcement will have the ability to conduct wiretaps and location tracking without anybody scrutinising what they’re doing, and nobody may have the opportunity to push back and demand appropriate legal process,” Wessler told FORBES.
While U.S. law enforcement officers are able to get phone records from carriers with the right warrant, the Ability service means they don’t need to get such permission, he added. “There is a significance to cutting the phone companies out of that transaction, because it makes it trivially easy to totally bypass the legal protections that are required under the U.S. Constitution and federal law.”
Meet the CEO
American cops may soon be paying big bucks for Ability’s tech. The Israeli company is planning a significant expansion in America this year and is currently looking for a partner to help it sell to U.S. law enforcement, says Ability’s CEO, Anatoly Hurgin, who I spoke with as he was driving to his office in Tel Aviv on Thursday morning and later that afternoon from his company HQ.
“You cannot just ignore such a huge market. It’s about half of the world market for our kind of technology,” he said. An SEC filing detailing Ability’s merger with Cambridge Capital Acquisition Corporation, which helped the Israeli company go public, indicates the market is indeed blowing up; the U.S. lawful intercept industry worth $3.8 billion in 2015 is expected to hit $6.3 billion in 2020. That same document valued Ability at $225 million, though it’s current market cap is down at $71.1M.
Hurgin’s tools may allow for easy snooping on others, but he told me he cares about his own privacy. There’s very little public information about him. His LinkedIn profile reveals nothing beyond his position at Ability. His Google+ and Skype avatars show a thin man, grey hair, sunglasses. Hurgin says he started Ability with its equally enigmatic Russian co-founder Alexander Aurovsky after a long stint in the Israeli Defense Forces, but he won’t tell me what division. He says it wasn’t the noted Unit 8200 or Shin Bet. “I started as an electronic engineer,” is all he says.
Though predictably guarded, he did let slip some more details about ULIN. He says the tool can sell for anywhere between $5 million and $20 million, as confirmed in the quarterly update. The price depends on where a suspect is based and how many targets a customer wants to snoop on. Those targets can be based anywhere in the world, he says, indicating widespread access to the SS7 network. He declined to tell me how the firm accesses the SS7 network without going through operators, only noting Ability uses “every possible way.”
“ULIN, being combined with other cyber solutions, will open a new era in data interception. What you can do today with Wi-Fi interception systems from distance less than 100m, you will be able to do without distance limitation at all,” he added over a Skype message sent after our conversation.
Despite the bold claims, Ability’s tool may not be as “unlimited” as advertised. Kohl notes that some operators have already deployed firewalls that prevent SS7 attacks. Many more will do so this year, he claimed, noting he is helping a handful of unnamed operators set up those firewalls. “SS7 firewalls block messages types that are clearly abusive and also some other possibly abusive messages from strange senders. A few firewall rules go a long way to solve 90 per cent of the SS7 security issue.”
Is Hurgin concerned about his pricey product becoming obsolete? “This concern does exist. But talking about [fixing the networks] and doing something are different things.”
And while $20 million might seem like a high price, Porter believes it’s more than reasonable. “I have not seen a system with a more polished user interface as theirs,” he added, after reviewing the ULIN manual obtained by FORBES. “At $20 million, to locate and intercept almost anyone’s cell phone seems like good deal to me.”
Ability shares tank
Thanks to all that expensive surveillance gadgetry, Hurgin’s company, founded in 1994, has posted some positive financials. This month, it claimed revenue growth of 143 per cent from 2014 to 2015, with overall revenue hitting $52.2 million. Overall net income was $14.8 million, compared to $3.1 million in 2014. It benefited from a $6.1 million deal with an unnamed intelligence agency in Asia made sometime in 2015. Other recent customers include a prison authority in Latin America and an intelligence agency in a Nato member country.
But this month, the company suddenly found itself under threat of legal action from its own investors. Having started trading publicly on the Nasdaq in December, Ability had a steady start, but in May shares started tanking. Though Hurgin put a positive spin on profits, they masked a glaring issue: Ability had been compelled to restate its results for 2015, 2014, 2013 and 2012 as it had failed to report money owed to an unnamed third-party vendor across two of those years and had improperly reported allocation and timing of revenue.
On May 2, the day it announced those errors, the price of Ability’s common stock fell 33 per cent to close at $4.90 per share. It continued to fall through the month, hitting a low of $2.70 on May 24.
As a result of the aberrations, two law firms last week opened class action lawsuits on behalf of investors, alleging Ability had violated the Securities Exchange Act by overstating its income and had weak internal controls for its financial reporting. Ability has brought in a contractor to bolster those controls.
Hurgin isn’t exactly concerned. “Not at all. What really matters is business itself. Results, numbers, sales, orders, revenue, income,” he said. “[Lawsuits come] automatically to any company after the restatement. Never mind.”
Scary new Ability?
How better to get the company back on track than with even more powerful spy kit? Further updates to the Ability’s product will allow cops and intel agents to harvest multimedia texts, according to the ULIN manual. That document indicates ULIN already allows for live wiretapping and the ability to listen to calls in real-time through a web browser. The tool can even grab the location of whoever the target is interacting with.
“The agent can ask the system to get the location of the other party involved in the call or SMS,” the document read. “All the intercepted calls and SMSs can be located on a map displayed to the agents who can access that information.”
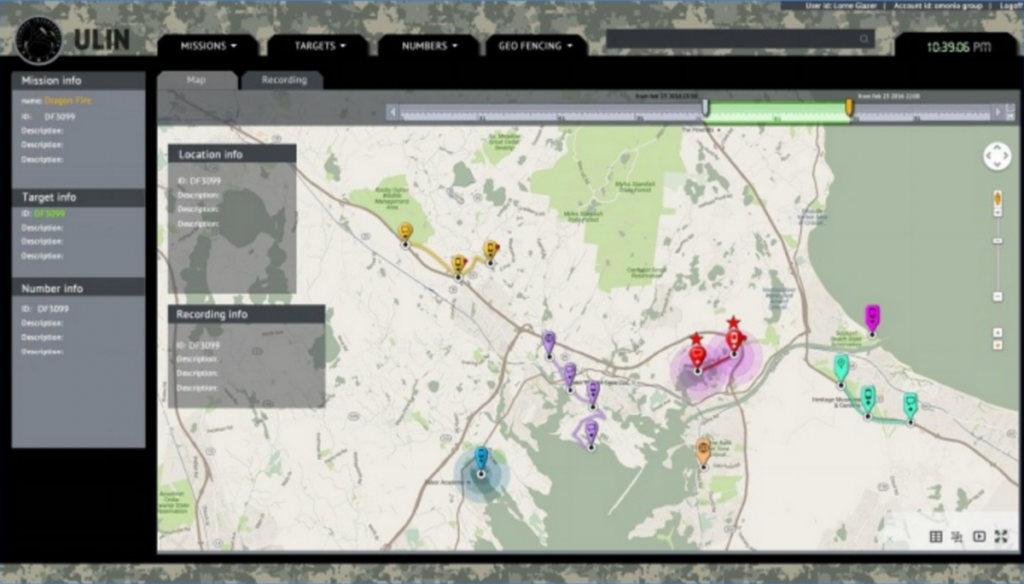
Ability’s ULIN surveillance tool can map targets for intel agents and cops, with a simple user interface.
By September, Hurgin believes ULIN will be able to intercept internet traffic, including web and app use. He can’t promise, however, it will be able to hoover up encrypted data.
ULIN is a young product, and may not be in wide use. According to May’s results document, Ability has sold only one ULIN product at the low end of its price scale, but has “received inquiries from a number of existing and potential customers.” It will treat that first customer, who will not be doing cross-border exploitation but focusing on targets within their own country, as a beta test. Hurgin tells me the firm has customers in Europe, Asia and Latin America. Did that include the UK? “Let’s say we’re in touch.”
Israeli surveillance world domination
Israeli surveillance companies, most built by alumni of the country’s various intelligence agencies, make up a huge chunk of the so-called “lawful interception” market. Often they work in partnerships to provide even more powerful surveillance systems. Leaks from Italian police-grade spyware dealer Hacking Team, now available on Wikileaks, revealed a host of Israeli companies looking for police-grade malware partners, including Ability, Nice Systems, now the owner of Elbit Systems’ cyber division, and Verint (previously linked with American surveillance operations). Network surveillance vendors like those four typically locate and offer a path into a person’s mobile, whilst Hacking Team and its competitors create the malware that provides complete, permanent, remote access to the device, including those critical encrypted communications.
One of HackingTeam’s more significant rivals, a highly-secretive Israeli company called NSO, is a partner of Ability, said Hurgin. He revealed NSO, and other unnamed government spyware creators, ride on Ability’s network exploits (though not via SS7) to deliver their spyware onto devices. NSO co-founder Omri Lavie has repeatedly declined interviews with me over the last year. His business is believed to have spyware that can work on iPhones and Androids, amongst other phones. “I think it’s one of the best companies in this field,” Hurgin said.
Ability isn’t the only company to target SS7 so aggressively. Indeed, Ability didn’t actually design the ULIN product, nor does it own the technology, but licenses it from an unnamed third-party. The company is investing research and development for the system, and is the only one deploying the tool on its own infrastructure, but it has relied on another firm for the core system. That other firm is only described in SEC filings as “a newly established corporation with a short operating history and is still unknown in the industry.”
And last year, it was revealed that Circles Bulgaria and two other Israeli companies, Rayzone and CleverSig, were selling SS7 exploit packages, though there was little detail on what exactly they offered or for how much.
It’s clear, though, that at least one company is happy to expose the security of the telecoms backbone for significant profit. And the surveillance is only getting more invasive. As with any technology, where one crosses the Rubicon, others will follow, regardless of the potential degradation of people’s privacy.
Hurgin, meanwhile, says governments need the technology to counter the rising threat of terrorism. “It is a war.”
ULIN Product Description – Ability by Thomas Fox-Brewster
______________________________________
Thomas Fox-Brewster – I cover crime, privacy and security in digital and physical forms.
DISCLAIMER: The statements, views and opinions expressed in pieces republished here are solely those of the authors and do not necessarily represent those of TMS. In accordance with title 17 U.S.C. section 107, this material is distributed without profit to those who have expressed a prior interest in receiving the included information for research and educational purposes. TMS has no affiliation whatsoever with the originator of this article nor is TMS endorsed or sponsored by the originator. “GO TO ORIGINAL” links are provided as a convenience to our readers and allow for verification of authenticity. However, as originating pages are often updated by their originating host sites, the versions posted may not match the versions our readers view when clicking the “GO TO ORIGINAL” links. This site contains copyrighted material the use of which has not always been specifically authorized by the copyright owner. We are making such material available in our efforts to advance understanding of environmental, political, human rights, economic, democracy, scientific, and social justice issues, etc. We believe this constitutes a ‘fair use’ of any such copyrighted material as provided for in section 107 of the US Copyright Law. In accordance with Title 17 U.S.C. Section 107, the material on this site is distributed without profit to those who have expressed a prior interest in receiving the included information for research and educational purposes. For more information go to: http://www.law.cornell.edu/uscode/17/107.shtml. If you wish to use copyrighted material from this site for purposes of your own that go beyond ‘fair use’, you must obtain permission from the copyright owner.
Read more
Click here to go to the current weekly digest or pick another article:
WHISTLEBLOWING - SURVEILLANCE: