Edward Snowden’s New App Uses Your Smartphone to Physically Guard Your Laptop
TECHNOLOGY, 25 Dec 2017
22 Dec 2017 – Like many other journalists, activists, and software developers I know, I carry my laptop everywhere while I’m traveling. It contains sensitive information; messaging app conversations, email, password databases, encryption keys, unreleased work, web browsers logged into various accounts, and so on. My disk is encrypted, but all it takes to bypass this protection is for an attacker — a malicious hotel housekeeper, or “evil maid,” for example — to spend a few minutes physically tampering with it without my knowledge. If I come back and continue to use my compromised computer, the attacker could gain access to everything.
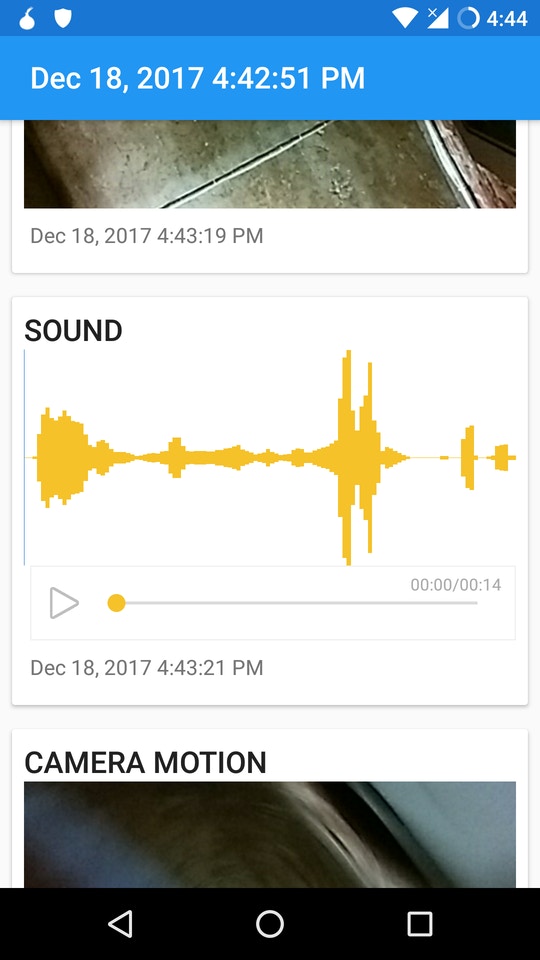
Edward Snowden and his friends have a solution. The NSA whistleblower and a team of collaborators have been working on a new open source Android app called Haven that you install on a spare smartphone, turning the device into a sort of sentry to watch over your laptop. Haven uses the smartphone’s many sensors — microphone, motion detector, light detector, and cameras — to monitor the room for changes, and it logs everything it notices. The first public beta version of Haven has officially been released; it’s available in the Play Store and on F-Droid, an open source app store for Android.
Snowden is helping to develop the software through a project he leads at the Freedom of the Press Foundation, which receives funding from The Intercept’s parent company. I sit on the FPF board with Snowden, am an FPF founder, and lent some help developing the app, including through nine months of testing. With that noted, I’ll be forthright about the product’s flaws below, and have solicited input for this article from people not involved in the project.
Also collaborating on Haven is the Guardian Project, a global collective of mobile security app developers.
Haven is an external solution to a problem computer makers traditionally attempted to handle from within their devices. Some laptops, for example, offer “secure boot” through a special tamper-resistant chip called a Trusted Platform Module, which tries to ensure that the computer’s bootloader code hasn’t been modified to be malicious. But there are various ways this could go wrong: there can be bugs in the code that does the verification, attackers could connive to get their code marked as trustworthy, or malicious code could be inserted after the bootloader. Some computer users have tried the low-tech solution of painting glitter nail polish on their laptop screws, creating a sort of seal that would be broken during a tampering attempt.
“Due to how current laptops, and probably most other computing devices, are made today, it is virtually impossible to systematically check later if the laptop has been compromised or not,” said Joanna Rutkowska, founder of the secure Qubes operating system, who invented the term “evil maid” in 2009 as part of her work as a security researcher.
httpv://www.youtube.com/watch?v=Fr0wEsISRUw
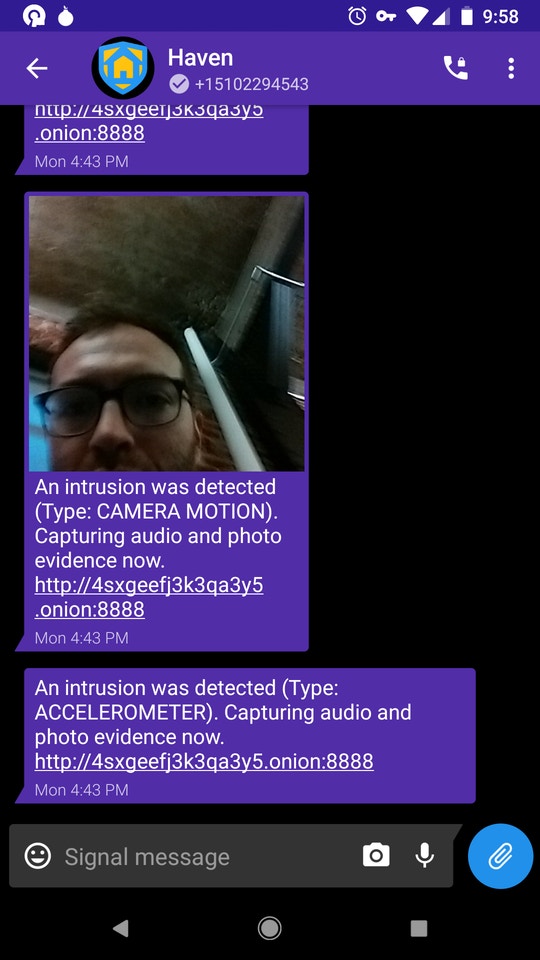
Here’s how Haven might work: You lock your laptop in a hotel safe — not a secure move on its own — and place your Haven phone on top of it. If someone opens the safe while you’re away, the phone’s light meter might detect a change in lighting, its microphone might hear the safe open (and even the attacker speak), its accelerometer might detect motion if the attacker moves the laptop, and its camera might even capture a snapshot of the attacker’s face. The Haven app will log all of this evidence locally on the Android device.
You can configure Haven to send you real-time encrypted alerts of what it detects to your other phone, the one you carry with you, when an intrusion is detected. You can choose to get encrypted Signal notifications, and you can also configure Haven to run a Tor onion service website (that is, a darknet site), and use Tor Browser on another device to connect in and view all of the alerts — all without giving anyone else access to these evidence logs unless you choose to share them. Haven also supports SMS text notifications, which can be intercepted but which might be more reliable in some situations.
Protecting my laptop against evil maid attacks is my primary use-case for Haven, but it isn’t the only reason people might be interested in using the app.”I can imagine this might be useful to victims of domestic abuse who are worried about their abusers spying on them in some way,” Eva Galperin, director of cybersecurity for Electronic Frontier Foundation, said. Galperin is familiar with the security challenges of evil maid attacks, but has not tested out Haven herself. “This might be useful for teenagers who are concerned about their parents, or who are concerned about nosy partners, or friends [spying on them]. Or if you’re in college and you’re worried about your roommate,” she added.
Galperin’s main concern about Haven is false positives. “If you’re concerned about people coming into the room and moving things, it doesn’t necessarily mean that they have ill intent. Or you could be setting things up on a hair trigger, and then you end up with a bunch of false positives and get paranoid for no reason,” she said. “Maybe the maid isn’t evil. Sometimes the maid is just a maid.”
Haven can also be used as a cheap home or office security system to detect break-ins or vandalism while you’re away, positioning the phone to send you photographs when someone walks within range. Or you can use it to monitor for wildlife in rural areas, or to capture evidence of human rights violations and disappearances.
Based on my experience testing Haven so far, here are some of the things to consider.
You definitely need a separate Android device to use Haven effectively, but you don’t actually need to pay for phone service for that device if you don’t want to. Without phone service, here are your options for using Haven:
- You could choose to not get notifications on your other phone at all, and instead just check the local Haven logs once you get back to the room you’re monitoring.
- You could connect to a wifi network (like the hotel’s network) on your Haven phone, and configure Haven to run a Tor onion service website directly on the phone. You can then use Tor Browser on a computer, Orfox on an Android phone, or Onion Browser on an iPhone to load this website to check for intrusion alerts. To do this, you need to install the Orbot app, which is Tor for Android, on your Haven phone as well.
- You could also connect to wifi and configure Haven to send you real-time Signal notifications as intrusion events happen. This is the most user friendly way of getting alerts. However, without phone service, it’s not trivial to set up because you’ll need to obtain an extra phone number to register a new Signal account with, like described in this article.
If you do pay for phone service for your Haven phone:
- If your phone plan includes mobile data, you don’t have to worry about wifi being available. In fact, I’d recommend disabling wifi and only using mobile data.
- You can use the Haven app to register a Signal account using your spare phone’s phone number, to send encrypted notifications to your normal phone via Signal.
- You can also choose to have Haven send SMS notifications to your normal phone on intrusion events, instead of using Signal.
If you’re going to be gone for a long period of time, you might need to keep your Haven phone plugged in so that it doesn’t run out of battery and power off. This means you can’t keep your laptop and Haven phone in a hotel safe for too long before the battery dies. But, considering hotel safes are not very secure, it’s not too different to just leave your laptop and Haven phone on the desk or bedside table, plugged in.
Another thing to consider is the the security of your Haven phone itself.
A clever attacker who knows that you’re using Haven could jam the wifi, mobile data, and SMS wireless frequencies, preventing Haven from sending you notifications. The attacker could then attempt to access the phone to delete the local evidence logs from the device as well.
For this reason, it’s important to lock down your Haven phone. Lock your phone with a strong passcode or password, and make sure your phone is encrypted. You can change your lockscreen and security settings from the Settings app. Also, install all updates for Android and for all of your apps, and turn off all radios that you aren’t using, like bluetooth and NFC. If you can, use mobile data and turn off wifi as well. This will reduce the attack surface of the phone, making it more difficult for an attacker to hack it once they’ve entered your room.
Rutkowska said she “absolutely” believes there is a need for technology like Haven, and suggested that the developers add “a hearbeat signal… for remote logging.” That would help warn users when the device loses a network connection, for example due to signal jamming. She also thinks most users will disable real-time notifications because “getting lots of Signal messages is annoying” — better to have a log that can be consulted later. To protect it from tampering, such a log could be cryptographically signed. It could also be pushed to a remote location, like a git version-control repository running on a distant server.
If an attacker can both jam your Haven phone’s radio signals and also hack into it to delete the evidence of intrusion, it’s possible for them to then still do an evil maid attack on your laptop without getting caught. However, Haven makes such an attack considerably more expensive, with less certainty of success, than if all they had to deal with was tampering with your laptop.
Another thing to keep in mind is that Haven can only monitor for intrusions if you actually use it. During my time testing it, more than once I positioned my Haven phone in the right place, made sure it was connected to wifi so I could get notifications, and plugged in so the battery wouldn’t die, but then forgot to actually activate the app. Several hours later when I returned to my room and found the Haven phone deactivated, I had no way of knowing if an intrusion occurred or not.
Finally, Haven is still in early development. There are still kinks that need to be worked out, plenty of bugs that need to be fixed, and plenty of features that would make it more useful and more reliable. There are false positives; once, I came back to find over 80 intrusion alerts, all of them the sounds of loud cars or sirens driving by my Manhattan hotel room. And sometimes, actual events don’t get logged when they should — I ran into issues where camera motion events weren’t getting triggered at all on my device, but that bug has been resolved for me now. It would be prudent to wait for the Haven app to mature before relying on it in high security situations.
But even now, it’s much better than leaving your laptop exposed to physical attacks without any monitoring while you’re heading out for drinks after a long day at a conference.
________________________________________________
Related: Encrypting Your Laptop Like You Mean It
 Micah Lee – micah.lee@theintercept.com
Micah Lee – micah.lee@theintercept.com
Go to Original – theintercept.com
DISCLAIMER: The statements, views and opinions expressed in pieces republished here are solely those of the authors and do not necessarily represent those of TMS. In accordance with title 17 U.S.C. section 107, this material is distributed without profit to those who have expressed a prior interest in receiving the included information for research and educational purposes. TMS has no affiliation whatsoever with the originator of this article nor is TMS endorsed or sponsored by the originator. “GO TO ORIGINAL” links are provided as a convenience to our readers and allow for verification of authenticity. However, as originating pages are often updated by their originating host sites, the versions posted may not match the versions our readers view when clicking the “GO TO ORIGINAL” links. This site contains copyrighted material the use of which has not always been specifically authorized by the copyright owner. We are making such material available in our efforts to advance understanding of environmental, political, human rights, economic, democracy, scientific, and social justice issues, etc. We believe this constitutes a ‘fair use’ of any such copyrighted material as provided for in section 107 of the US Copyright Law. In accordance with Title 17 U.S.C. Section 107, the material on this site is distributed without profit to those who have expressed a prior interest in receiving the included information for research and educational purposes. For more information go to: http://www.law.cornell.edu/uscode/17/107.shtml. If you wish to use copyrighted material from this site for purposes of your own that go beyond ‘fair use’, you must obtain permission from the copyright owner.