Our SecureDrop System for Leaks Now Uses HTTPS
WHISTLEBLOWING - SURVEILLANCE, 13 Apr 2015
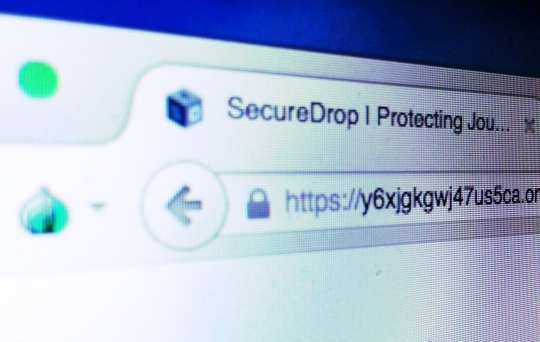 8 Apr 2015 – We’re happy to announce that sources can now access our SecureDrop document-submission website using HTTPS. Although SecureDrop connections were already encrypted previously, our new setup provides leakers with additional assurance that they are connecting with the authentic Intercept SecureDrop and not an impostor.
8 Apr 2015 – We’re happy to announce that sources can now access our SecureDrop document-submission website using HTTPS. Although SecureDrop connections were already encrypted previously, our new setup provides leakers with additional assurance that they are connecting with the authentic Intercept SecureDrop and not an impostor.
You can visit our SecureDrop server by pointing the Tor Browser here: https://y6xjgkgwj47us5ca.onion/
SecureDrop runs as a “hidden service” within the anonymous web network Tor. A hidden service is a special kind of server that is only accessible through Tor and has a domain name ending in .onion (Tor was originally called The Onion Router because it works by creating layers upon layers of encryption to hide users’ IP addresses).
The Intercept’s SecureDrop installation is only the third Tor hidden service to receive a browser-trusted HTTPS certificate, following Facebook and the Bitcoin website Blockchain.info. HTTPS provides two things: Confidentiality — data shared between web browsers and HTTPS websites is encrypted — and authentication — web browsers can verify that they’re visiting the website the user thinks they’re visiting. Authentication helps prevent man-in-the-middle attacks, which occur when an attacker entices someone to open an encrypted connection to the attacker’s server by impersonating the real server.
Even without HTTPS, the connection between Tor Browser and our SecureDrop hidden service was already encrypted. Adding HTTPS provides a second redundant layer of encryption, and it also adds authentication. So if a source finds herself visiting a SecureDrop website that looks like it belongs to The Intercept, she can inspect our SSL certificate to confirm that it actually belongs to us and isn’t a honeypot posing as our SecureDrop website — or at least confirm that this is the case according to DigiCert, the certificate authority that issued our SSL certificate.
The future of combining HTTPS and the .onion top-level domain is uncertain because .onion is not an officially recognized top-level domain. But the gears are in motion to get .onion recognized as a “Special-Use Domain Name.” We won’t know for sure if we get to keep our SSL certificate until the Internet Engineering Steering Group agrees on whether or not to make .onion a standard, a decision slated to be made in October.
Until then, our sources can enjoy this extra layer of protection when they communicate with us through SecureDrop.
_______________________
Email the author: micah.lee@theintercept.com
Go to Original – firstlook.org
DISCLAIMER: The statements, views and opinions expressed in pieces republished here are solely those of the authors and do not necessarily represent those of TMS. In accordance with title 17 U.S.C. section 107, this material is distributed without profit to those who have expressed a prior interest in receiving the included information for research and educational purposes. TMS has no affiliation whatsoever with the originator of this article nor is TMS endorsed or sponsored by the originator. “GO TO ORIGINAL” links are provided as a convenience to our readers and allow for verification of authenticity. However, as originating pages are often updated by their originating host sites, the versions posted may not match the versions our readers view when clicking the “GO TO ORIGINAL” links. This site contains copyrighted material the use of which has not always been specifically authorized by the copyright owner. We are making such material available in our efforts to advance understanding of environmental, political, human rights, economic, democracy, scientific, and social justice issues, etc. We believe this constitutes a ‘fair use’ of any such copyrighted material as provided for in section 107 of the US Copyright Law. In accordance with Title 17 U.S.C. Section 107, the material on this site is distributed without profit to those who have expressed a prior interest in receiving the included information for research and educational purposes. For more information go to: http://www.law.cornell.edu/uscode/17/107.shtml. If you wish to use copyrighted material from this site for purposes of your own that go beyond ‘fair use’, you must obtain permission from the copyright owner.
Read more
Click here to go to the current weekly digest or pick another article:
WHISTLEBLOWING - SURVEILLANCE: