Drones, IBM, And the Big Data of Death
SPECIAL FEATURE, 26 Oct 2015
23 Oct 2015 – Last week The Intercept published a package of stories on the U.S. drone program, drawing on a cache of secret government documents leaked by an intelligence community whistleblower. The available evidence suggests that one of the documents, a study titled “ISR Support to Small Footprint CT Operations — Somalia/Yemen,” was produced for the Defense Department in 2013 by consultants from IBM. If you look at just one classified PowerPoint presentation this year, I recommend you make it this one.
Like a good poem, the ISR study has multiple meanings, and rewards careful attention and repeated reading. On its surface, it’s simply an analysis by the Defense Department’s Intelligence, Surveillance, and Reconnaissance (ISR) Task Force of the “performance and requirements” of the U.S. military’s counterterrorism kill/capture operations, including drone strikes, in Somalia and Yemen. However, it’s also what a former senior special operations officer characterized as a “bitch brief” — that is, a study designed to be a weapon in a bureaucratic turf war with the CIA to win the Pentagon more money and a bigger mandate. The study was also presumably an opportunity for IBM to demonstrate that it can produce snappy “analysis” tailored to the desires of its Defense Department clients, as well as for current Defense employees to network with a potential future employer.
But the presentation’s most compelling meaning is much deeper: It’s a rare, peculiar cultural artifact that opens a window into the deep guts of the military-industrial complex, where the technologies of assassination and corporate sales converge, all described in language as dead as the target of an ISR platform kinetic engagement.
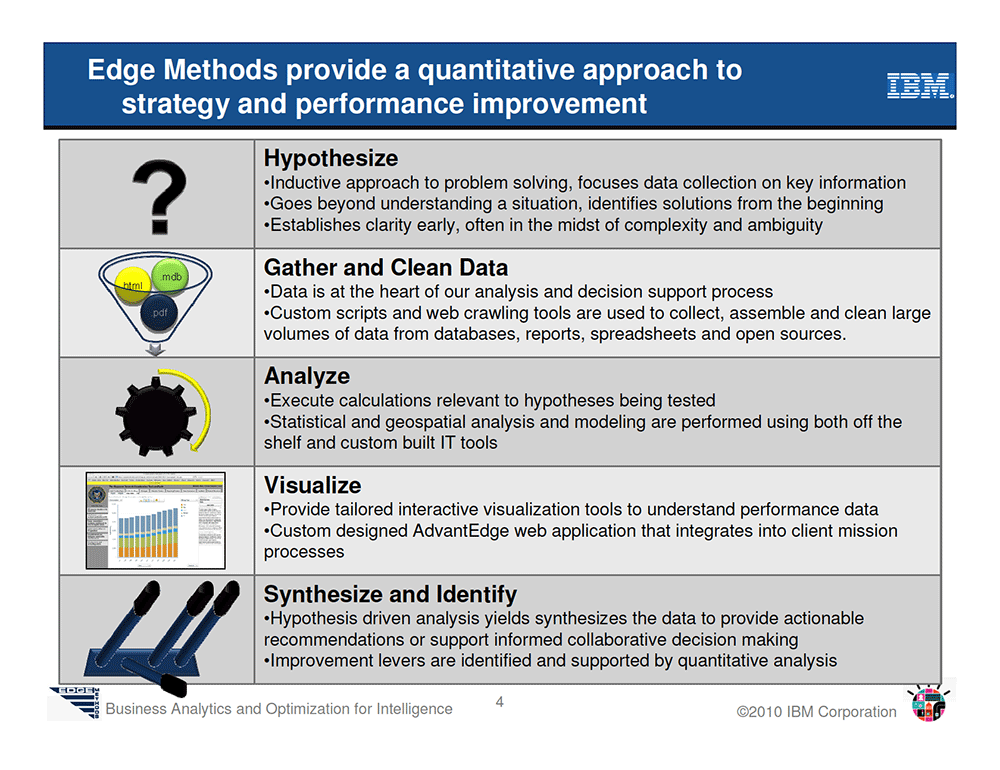
Edge Methods
In 2010, IBM employees delivered a talk at IBM’s Analytics Solution Center in Washington, D.C., titled “An Introduction to Edge Methods: Business Analytics and Optimization for Intelligence.” The audience was “the Defense and Intelligence communities,” and IBM’s goal was to explain to them how the company could help them with “managing large volumes of data” to derive “invaluable” insights. Among its already-existing governmental customers, IBM explained, was the ISR Task Force.
Although buried in reams of corporate management gobbledygook (IBM, it turns out, is “Mission Focused” and “Performance Driven”), the talk’s key theme was that IBM was offering prospective new government clients its “expertise in integrating business and technology services” using its “commercial consulting methods.” That is, IBM was bringing what it had learned from managing Big Data for corporate America to the military and intelligence worlds.
Keep that in mind as you examine the secret ISR study, and you’ll see that the Pentagon’s drone program uses data analytics in almost precisely the same way IBM encourages corporations to use it to track customers. The only significant difference comes at the very end of the drone process, when the customer is killed.
For instance, according to the ISR study, the drone program seeks to “find,” “fix,” and “finish” its “high-value individuals.” Meanwhile, in IBM’s description of Big Data for the private sector, there are precisely equivalent goals: to “acquire,” “retain,” and “personalize” a corporation’s “high-value customers.”
The drone infrastructure uses Big Data to “build target packages” about its high-value individuals, while corporations can “build profiles of the most profitable current customers.” Drones attempt “to maintain 24/7 persistent stare,” just as corporations need “to get a 360 view of the customer.”
The successful “finish” stage of a drone strike is termed a “jackpot,” while for businesses the “personalization” stage is where it all comes together, “converting insights into relevance to deliver targeted messages.” High-value customers receive an emailed coupon informing them that they haven’t bought new socks in nine months, whereas for high-value individuals the targeted message takes the form of a Hellfire missile.
Likewise, the language of the drone study mimics corporate Big Data’s uncanny lack of affect. In both cases, highly trained technicians discuss how to make the system work more efficiently, with no room for unprofessional emotions. After examining the drone study, Pentagon Papers whistleblower Daniel Ellsberg noted its “reliance on abstract euphemisms for methods of mass murder, acronyms, and bloodless jargon to assure you were communicating with people who were cleared, in the know, and dependent for their income and advancement on uncritical devotion to the objective.”
Bloodless is exactly the right word: The ISR study is bloodless both metaphorically and literally. Whether the U.S. drone war is right or wrong, wise or mind-numbingly stupid, it’s like half of history’s science fiction novels come to life simultaneously — billions of dollars, thousands of people, and hundreds of years of physics and chemistry all combined to deliver 18 pounds of explosives to one tiny target. Yet the study’s language has less zest than the wiring diagram for an air conditioner.
There is also no actual blood in the presentation. The high-value individuals marked for death barely possess human names; instead they are objectified with code names such as Objective Peckham or Objective Rhodes or Objective Canton. They are not shredded by shrapnel into scraps of wet, red flesh, but rather experience a “kinetic engagement” or “finishing action.” And while the drone program attempts to monitor them with unblinking HD video, there is no suggestion they ever had any existence beyond that of a target. Nor is there any sign of the American human beings who make the drone program run on a day-to-day level — just FSs, MFWs, and JWICS, hundreds and hundreds of International Business Machines.
Finally, there’s the most important aspect of IBM’s identical Big Data approaches to death and customer service: Both are extremely powerful systems that have escaped any kind of human, democratic control. As Ellsberg puts it, the drone study is “unintelligible to anyone who might ask, ‘to what end is all this?’ or ‘do we have the right to be doing this?’ or ‘is this making us more secure, in the mid- to long-term, or on balance less so?’ or ‘is this creating more people who hate us — including the families of EKIAs (unintended victims) — and wish to harm us, than it is eliminating?’”
Surprisingly, after his retirement, Gen. Stanley McChrystal made a similar point: “Although to the United States, a drone strike seems to have very little risk and very little pain, at the receiving end, it feels like war. … If we were to use our technological capabilities carelessly … we should not be upset when someone responds with their equivalent, which is a suicide bomb in Central Park, because that’s what they can respond with.”
There Are No Nations
As a resident of New York City, I feel this viscerally. I don’t mean that figuratively; I feel it in my viscera, right underneath my stomach. If you would like to feel it too, try walking down West 45th Street in Times Square, past the offices of MTV. In 2010 Faisal Shahzad parked his Nissan SUV there, near Broadway — about 15 blocks south of McChrystal’s hypothetical Central Park terrorism — in an attempt to set off a non-hypothetical car bomb. Shahzad later specified that he was retaliating for, among other things, “the drone strikes in Somalia and Yemen” — i.e., the subject of the classified ISR study.
But Big Data will never be used to examine these questions, even with figures as significant as McChrystal asking them, just as Apple will never hire IBM to help it determine whether the world finally has enough iPhones. As IBM says, one of the “basic structural components” of Big Data is to “increase profitability.” And if the 14 years since 2001 have proven anything, it’s that the drive to “increase profitability” is at the core of all significant decisions by the people who run the United States. The drone war could generate bombings in 100 U.S. cities, accidentally obliterate 100 weddings in Yemen, or cause the few countries still standing in the Middle East to dissolve, and the killing would continue. If the drone war somehow became unprofitable for large corporations, however, it would be over that afternoon.
You may know the famous scene from the 1976 movie Network in which the chairman of Communications Corporation of America explains to Howard Beale that “there are no nations, there are no peoples … there is no America, there is no democracy.” But you likely don’t remember which corporation came first when he describes what actually does exist: “There is only IBM and ITT and AT&T and DuPont, Dow, Union Carbide, and Exxon. Those are the nations of the world today.” IBM received over $1.34 billion in federal contracts in fiscal year 2014, an increase of $108 million over FY 2013.
(A Pentagon spokesperson declined to comment or answer questions about IBM’s role in producing the ISR study, saying “the report you reference is an internal classified document. As a matter of policy we don’t comment on the details of classified reports.” IBM did not respond to a request for comment.)
_____________________________
Read the complete Drone Papers.
Contact the author: Jon Schwarz – jon.schwarz@theintercept.com
Go to Original – theintercept.com
DISCLAIMER: The statements, views and opinions expressed in pieces republished here are solely those of the authors and do not necessarily represent those of TMS. In accordance with title 17 U.S.C. section 107, this material is distributed without profit to those who have expressed a prior interest in receiving the included information for research and educational purposes. TMS has no affiliation whatsoever with the originator of this article nor is TMS endorsed or sponsored by the originator. “GO TO ORIGINAL” links are provided as a convenience to our readers and allow for verification of authenticity. However, as originating pages are often updated by their originating host sites, the versions posted may not match the versions our readers view when clicking the “GO TO ORIGINAL” links. This site contains copyrighted material the use of which has not always been specifically authorized by the copyright owner. We are making such material available in our efforts to advance understanding of environmental, political, human rights, economic, democracy, scientific, and social justice issues, etc. We believe this constitutes a ‘fair use’ of any such copyrighted material as provided for in section 107 of the US Copyright Law. In accordance with Title 17 U.S.C. Section 107, the material on this site is distributed without profit to those who have expressed a prior interest in receiving the included information for research and educational purposes. For more information go to: http://www.law.cornell.edu/uscode/17/107.shtml. If you wish to use copyrighted material from this site for purposes of your own that go beyond ‘fair use’, you must obtain permission from the copyright owner.