Leaked Files: German Spy Company Helped Bahrain Hack Arab Spring Protesters
WHISTLEBLOWING - SURVEILLANCE, 11 Aug 2014
Cora Currier and Morgan Marquis-Boire – The Intercept
7 Aug 2014 – A notorious surveillance technology company that helps governments around the world spy on their citizens sold software to Bahrain during that country’s brutal response to the Arab Spring movement, according to leaked internal documents posted this week on the internet.
The documents show that FinFisher, a German surveillance company, helped Bahrain install spyware on 77 computers, including those belonging to human rights lawyers and a now-jailed opposition leader, between 2010 and 2012—a period that includes Bahrain’s crackdown on pro-democracy protesters. FinFisher’s software gives remote spies total access to compromised computers. Some of the computers that were spied on appear to have been located in the United States and United Kingdom, according to a report from Bahrain Watch.
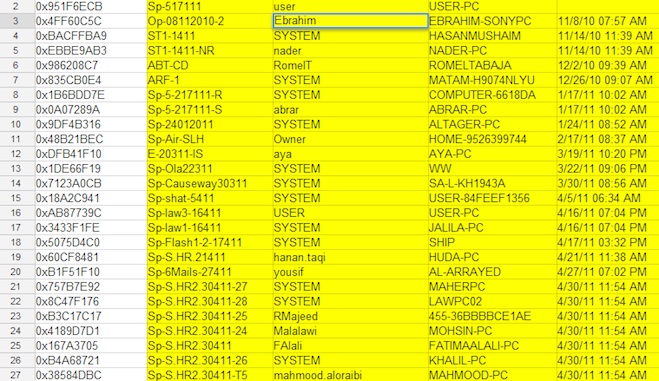
A screengrab from leaked FinFisher data appears to show surveillance targets of the Bahraini government.
Earlier this week, an anonymous hacker released 40 gigabytes of what appears to be internal data from FinFisher on Twitter and Reddit, including messages between people who appear to be Bahraini government officials and FinFisher customer service representatives.
In those messages, Bahraini software administrators complained to FinFisher that they were “losing targets daily” due to faults in its software. In one message employing the language of a frustrated consumer, a spy appeared to complain that he or she had to keep re-infecting a targeted computer, risking detection: “[W]e cant stay bugging and infecting the target every time since it is very sensitive. and we don’t want the target to reach to know that someone is infecting his PC or spying on him” one message reads.
On its website, FinFisher says it sells surveillance technology “exclusively to government law enforcement and intelligence agencies.” The company has previously denied reports that it sold spyware to Bahrain, claiming that examples researchers identified could have come from stolen or demonstration copies. The new documents, showing sustained correspondence between individuals in Bahrain and customer service, undercut that claim. FinFisher did not respond to requests for comment.
“[W]e have 30 target licenses, we are now using them all in which we have already 30 targets,” says one message, dated November 2, 2011. On December 8th, the Bahrainis asked for an update on a previous issue: “Please investigate urgently and let us know the solution. As we are in a big lose of data now.”
FinFisher belonged to the U.K.-based Gamma Group during the time period the leaked documents cover (it was spun off last year.) Researchers from Citizen Lab at the University of Toronto’s Munk School of Global Affairs–including a co-author of this post— first publicly identified the the FinFisher software in July 2012. At the time, members of the advocacy group Bahrain Watch in Washington, D.C., and London had been targeted via email by what appeared to be malware. The researchers analyzed the suspicious software and discovered that it was the FinSpy “lawful intercept” software developed by FinFisher. Additional research linked the use of this product to 36 countries worldwide.
The most recent leak includes logs from Bahraini software administrators of the installations they’d performed, which contained usernames and IP addresses, allowing Bahrain Watch researchers to identify some of the computers that had been targeted. Among them were Bahraini lawyers, U.K.-based activists and writers, and Hassan Mushaima, an opposition leader who is currently serving life in prison. He was sentenced in June 2011, months after the logs show spyware installed in his computer.
Another targeted computer belonged to Mohamed Altajer, a prominent human rights lawyer who was blackmailed in 2011 with a video of him and his wife having sex. The video arrived via CD at his office on January 24, 2011, bearing instructions that he stop defending activists or the tape would be made public. On that same day, the leaked logs show, spyware was installed on his computer, suggesting that government officials used the blackmail gambit to install FinSpy.
The video eventually became public in 2012, after Altajer participated in a UN human rights conference. “The 24th of January, 2011, was the most devastating day of my life,” said Altajer, reached in Bahrain.
“I’m happy that this is exposed,” he said. “The regime should understand that it is not so wise and clever to keep penetrating into people’s lives. These dirty people who videotaped me while I am naked, now they are naked, now they are exposed before the world.”
There’s little regulation preventing companies like FinFisher from selling surveillance software to countries like Bahrain. And the secretive nature of the industry means that companies “have been allowed to operate with impunity, selling intrusive surveillance equipment to states where there is no public scrutiny of surveillance or clear laws regulating its use,” said Eric King, deputy director of Privacy International. The U.K.-based group has asked the British government to investigate the Ethiopian government’s use of FinFisher’s tools to surveil a political refugee. And an Ethiopian-American is attempting to sue the Ethiopian government in U.S. federal court for using FinSpy against him.
“We should be putting international attention on these companies,” said Ali Abdulemam, a human rights activist and member of Bahrain Watch. “Gamma is always claiming that their product is for human trafficking or drug trafficking, but its being used against human rights by countries like Bahrain.”
In 2011, Bloomberg reported that Nokia Siemens was selling spy gear to Bahrain, and Bahraini interrogators were known at the time to show activists transcripts of their private text messages and phone conversations during torture sessions. The U.S. also continued arms sales to Bahrain during that period.
“As far as I am aware,” said Salman Aljalahma, the Bahraini government’s media attaché in Washington, “the Government of Bahrain does not use FinFisher.” He added “this is a matter of national security and confidential intelligence that the public, nor I, is privy to.”
When shown the customer service correspondence and surveillance logs, Aljalahma said that “all evidence collated by the accusers still shows no link to the Bahraini Government.”
Go to Original – firstlook.org
DISCLAIMER: The statements, views and opinions expressed in pieces republished here are solely those of the authors and do not necessarily represent those of TMS. In accordance with title 17 U.S.C. section 107, this material is distributed without profit to those who have expressed a prior interest in receiving the included information for research and educational purposes. TMS has no affiliation whatsoever with the originator of this article nor is TMS endorsed or sponsored by the originator. “GO TO ORIGINAL” links are provided as a convenience to our readers and allow for verification of authenticity. However, as originating pages are often updated by their originating host sites, the versions posted may not match the versions our readers view when clicking the “GO TO ORIGINAL” links. This site contains copyrighted material the use of which has not always been specifically authorized by the copyright owner. We are making such material available in our efforts to advance understanding of environmental, political, human rights, economic, democracy, scientific, and social justice issues, etc. We believe this constitutes a ‘fair use’ of any such copyrighted material as provided for in section 107 of the US Copyright Law. In accordance with Title 17 U.S.C. Section 107, the material on this site is distributed without profit to those who have expressed a prior interest in receiving the included information for research and educational purposes. For more information go to: http://www.law.cornell.edu/uscode/17/107.shtml. If you wish to use copyrighted material from this site for purposes of your own that go beyond ‘fair use’, you must obtain permission from the copyright owner.
Read more
Click here to go to the current weekly digest or pick another article:
WHISTLEBLOWING - SURVEILLANCE:
