Secret Manuals Show the Spyware Sold to Despots and Cops Worldwide
WHISTLEBLOWING - SURVEILLANCE, 3 Nov 2014
Cora Currier and Morgan Marquis-Boire – The Intercept
When Apple and Google unveiled new encryption schemes last month, law enforcement officials complained that they wouldn’t be able to unlock evidence on criminals’ digital devices. What they didn’t say is that there are already methods to bypass encryption, thanks to off-the-shelf digital implants readily available to the smallest national agencies and the largest city police forces — easy-to-use software that takes over and monitors digital devices in real time, according to documents obtained by The Intercept.
We’re publishing in full, for the first time, manuals explaining the prominent commercial implant software “Remote Control System,” manufactured by the Italian company Hacking Team. Despite FBI director James Comey’s dire warnings about the impact of widespread data scrambling — “criminals and terrorists would like nothing more,” he declared — Hacking Team explicitly promises on its website that its software can “defeat encryption.”
The manuals describe Hacking Team’s software for government technicians and analysts, showing how it can activate cameras, exfiltrate emails, record Skype calls, log typing, and collect passwords on targeted devices. They also catalog a range of pre-bottled techniques for infecting those devices using wifi networks, USB sticks, streaming video, and email attachments to deliver viral installers. With a few clicks of a mouse, even a lightly trained technician can build a software agent that can infect and monitor a device, then upload captured data at unobtrusive times using a stealthy network of proxy servers, all without leaving a trace. That, at least, is what Hacking Team’s manuals claim as the company tries to distinguish its offerings in the global marketplace for government hacking software.
Hacking Team’s efforts include a visible push into the U.S. Though Remote Control System is sold around the world — suspected clients include small governments in dozens of countries, from Ethiopia to Kazakhstan to Saudi Arabia to Mexico to Oman — the company keeps one of its three listed worldwide offices in Annapolis, Maryland, on the edge of the federal intelligence and law-enforcement cluster around the nation’s capital; has sent representatives to American homeland security trade shows and conferences, where it has led training seminars like “Cyber Intelligence Solutions to Data Encryption” for police; and has even taken an investment from a firm headed by America’s former ambassador to Italy. The United States is also, according to two separate research teams, far and away Hacking Team’s top nexus for servers, hosting upwards of 100 such systems, roughly a fifth of all its servers globally.
The company has made at least some sales to American entities, according to comments its outspoken co-founder and CEO David Vincenzetti made in l’Espresso in 2011. “We sell Remote Control System to institutions in more than 40 countries on five continents,” he told the Italian newsmagazine. “All of Europe, but also the Middle East, Asia, United States of America.” In the English-language press, where Hacking Team has been more circumspect about its client list, Vincenzetti’s l’Espresso comments about selling implants to U.S. institutions seem to have fallen through the cracks. Asked about them, Hacking Team spokesman Eric Rabe told The Intercept, “we do not identify either our clients or their locations.”
Whatever the extent of its U.S. sales, Hacking Team’s manuals deserve an audience in America and beyond. This summer, researchers at the Citizen Lab at the University of Toronto’s Munk School of Global Affairs, including the co-author of this piece, published excerpts of the manuals and technical descriptions of Hacking Team’s capabilities. Publishing the manuals in their entirety here will give the public a better understanding of the sophistication of these relatively low-cost and increasingly prevalent surveillance tools. That sort of understanding is particularly important at a time when digital monitoring has spread from large federal agencies to local police departments and as more national governments gain the once-rarified ability to deploy digital implants across borders. Turnkey solutions like RCS effectively multiply the online threats faced by activists, dissidents, lawyers, businessmen, journalists, and any number of other computer users.
A Niche for Commercial Spyware
Within the U.S., there’s relatively little information on the prevalence of law enforcement hacking. The FBI only rarely discloses its use in criminal cases. Chris Soghoian, principal technologist with the American Civil Liberties Union’s Project on Speech, Privacy and Technology, who has closely tracked the FBI’s use of malware, says that agents use vague language when getting judges’ permission to hack devices. “This is a really, really, invasive tool,” Soghoian says. “If the courts don’t know what they’re authorizing, they’re not a good check on its use. If we as a society want malware to be used by the state, we ought to have a public debate.”
What is clear is that large nations with well-funded intelligence establishments have long been capable of the kind of surveillance Hacking Team offers. In 2001, it was first reported that the FBI had developed malware known as Magic Lantern, which could take over a computer and log its users’ keystrokes, as a way around encryption. Soghoian says it’s likely that the bureau and American intelligence agencies get more customized spying solutions from contractors other than Hacking Team. Countries such as China and Russia probably develop their spyware in-house.
Hacking Team and the German firm FinFisher have taken over another niche, as the most prominent purveyors of user-friendly, off-the-shelf spyware for less moneyed customers, says Ben Wagner, director of the Center for Internet and Human Rights at the European University Viadrina. A recent leak of FinFisher data showed customer service communications between the company and Bahrain, Pakistan, Estonia, and a regional police department in Australia, among other clients. The cost of a Hacking Team installation package, meanwhile, ranges from 200,000 to 1 million euros, Vincenzetti told l’Espresso in 2011. Pricey, but not out of reach.
“If those countries didn’t have access to Gamma [FinFisher’s former parent company] or Hacking Team, they probably wouldn’t be able to do this kind of surveillance,” says Wagner. “Those are the two that we know about who have really gone for this targeted surveillance market for smaller and midsize countries.”
Soghoian thinks that “to the extent that Hacking Team has sold in the U.S., it would be to less well-resourced federal agencies or bigger local police teams.”
Hacking Team has built up enough of a profile to become something of an icon in its home country. “Elegant and tan” Vincenzetti has been lauded as a poster-boy for modernizing the Italian economy and is touted to stateside investors at events like “Italy Meets the USA.” Among those promoting Hacking Team is Innogest, an Italian venture capital firm headed by the former U.S. ambassador to Italy Ronald Spogli. The company is in Innogest’s own portfolio.
Despite the acclaim, Hacking Team — and its competitor FinFisher — have drawn the ire of human rights and privacy activists. “We have not that many companies doing nasty things for not that much money on a global scale, but with huge human rights effects,” Wagner said.
Companies like Hacking Team refer to their products as “lawful intercept” technology. They need at least the pretense of dealing with legitimate actors because the legality of surveillance software depends on the behavior of its users. That’s all that fundamentally separates their software from tools for crime or repression. But evaluating that legitimacy becomes tougher as prices fall and customers proliferate.
Hacking Team offers the assurance that its users are all government institutions. Spyware is perfectly legal in law enforcement or intelligence investigations “if used with the proper legal authorization in whatever jurisdiction they’re in,” according to Nate Cardozo, staff attorney at the Electronic Frontier Foundation. Hacking Team’s “customer policy” also claims that it will not sell to countries listed on international “blacklists” or that it believes “facilitate gross human rights abuses.” The company won’t disclose what it means by blacklists, how its review process works, or which, if any, customers have been dumped. Hacking Team’s spokesman refused to provide details beyond what is on the company’s website.
There’s evidence the company is not being particularly selective about to whom it sells. Of 21 suspected Hacking Team users tracked down by Citizen Lab, nine had been given the lowest possible ranking, “authoritarian,” in The Economist’s 2012 Democracy Index, and four of those were singled out for particularly egregious abuses — torture, beatings and rapes in detention, lethal violence against protestors — by Human Rights Watch.
Its competitors face similar criticism. Activists in Bahrain and Ethiopia have found FinFisher spyware on their computers. (FinFisher did not respond to an emailed request for comment.)
The U.S. government has shown an interest in policing the improper use of packaged malware. The Justice Department just recently brought its first case against a spyware developer, arresting a Pakistani man who marketed StealthGenie, an app that does some of the same things as Hacking Team’s RCS – monitoring all phone calls, messages, emails, texts and more without the owner’s knowledge — except for individuals rather than governments. Announcing the charges against StealthGenie’s maker, an assistant attorney general called the spyware “reprehensible…expressly designed for use by stalkers and domestic abusers who want to know every detail of a victim’s personal life.”
How It Works
Key to the spread of software like Hacking Team RCS is that it’s designed to be simple for non-experts to use.
In a brochure, Hacking Team boasts, “You cannot stop your targets from moving. How can you keep chasing them? What you need is a way to bypass encryption, collect relevant data out of any device, and keep monitoring your targets wherever they are, even outside your monitoring domain. Remote Control System does exactly that.”
Hacking Team manuals, dated September 2013, provide step-by-step instructions for technicians, administrators, and analysts on how to infect a device and set up spying.
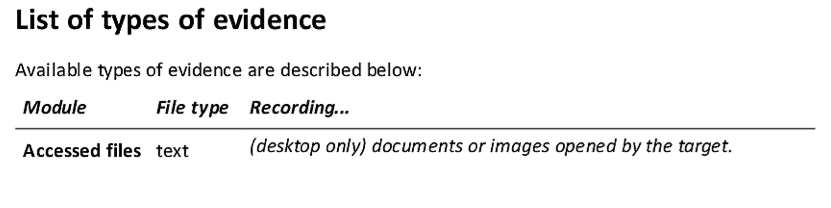
The software can be installed physically, via a USB stick, if the authorities have direct access to the computer (imagine a police stop or an airport search.)
Or, the infection can happen remotely. It could take the familiar form of a phishing attack or email scam – as a group of Moroccan reporters found out in 2012. A document promising them a secret scoop (it was titled “scandale,” in French) turned out to be a decoy for Hacking Team software. An Emirati blogger fell victim to the same trick. The implant can also be melded with legitimate, useful software that the victim is prompted to download.
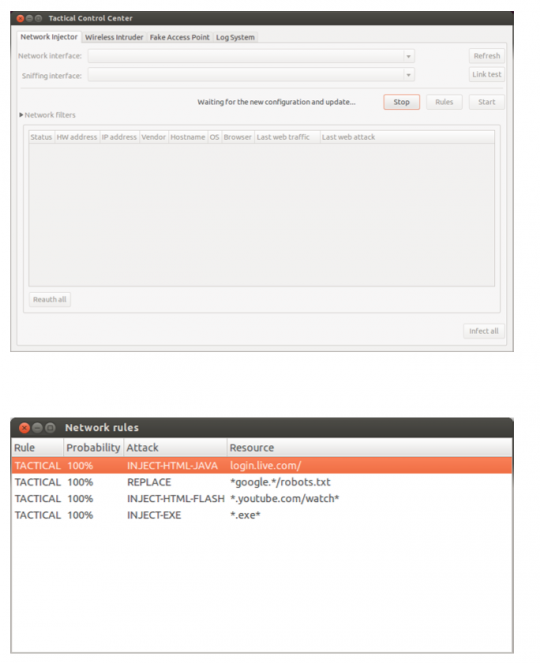
As The Intercept has previously reported, Hacking Team also installs its bugs via “network injectors” – physical devices housed with internet service providers, that allow them to intercept ordinary web traffic, like streaming video, and replace it with infectious code. (After we reported that YouTube and Microsoft Live were exploitable in this way, both companies moved to fix the vulnerabilities.)
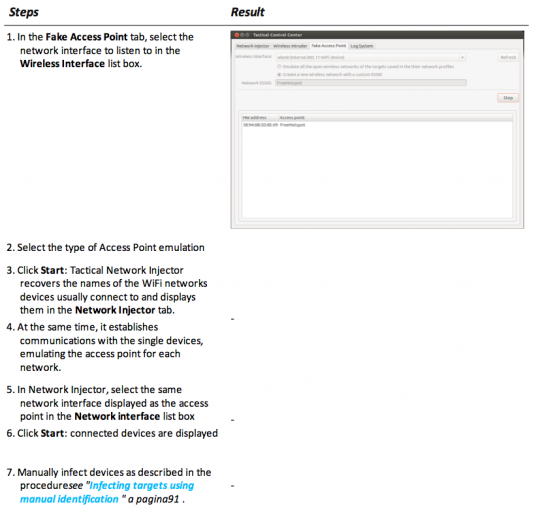
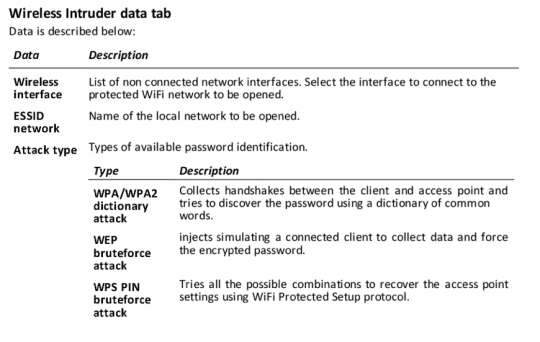
Then there are covert network injections. The spyware installer might lay in wait in a hotel, or a Starbucks, and gain access to your computer by “emulating an access point” – in other words, pretending to be a free wifi hotspot to which the victim connected previously. The manual also describes how the software can deploy password-busting tools to break into closed wifi networks.
The Hacking Team manuals recommend that customers buy a code signing certificate from Verisign (now Symantec), Thawte, or GoDaddy– companies that offer a stamp of assurance that signals to operating systems and anti-virus scanners that the software is legitimate. Getting what Symantec calls its “digital shrinkwrap” added to Hacking Team software makes it less likely to be detected. (Symantec declined to comment on how it handles malware in issuing certificates. GoDaddy and Thawte did not respond.)
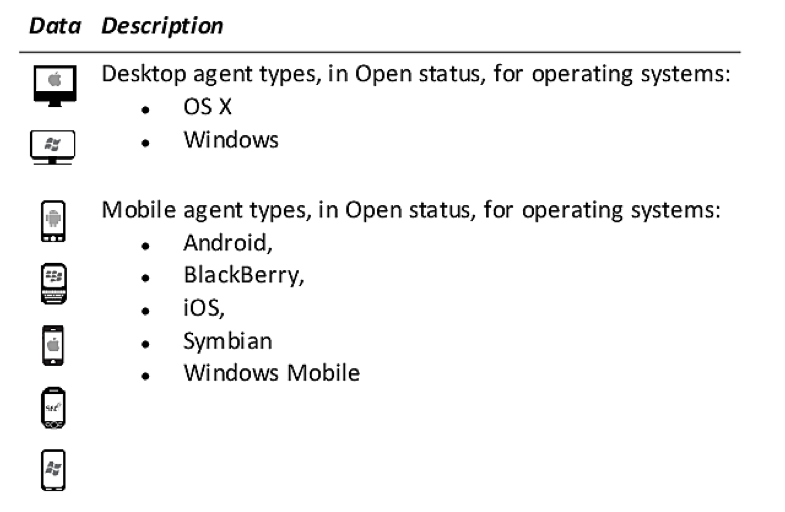
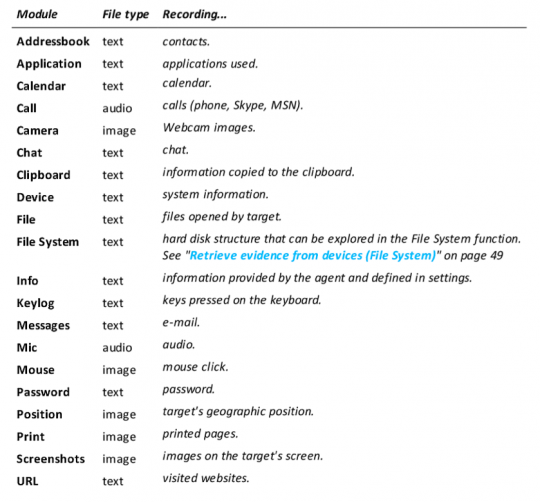
Via one of those methods, the “agent” — ie., the bug — is implanted on any of these devices:
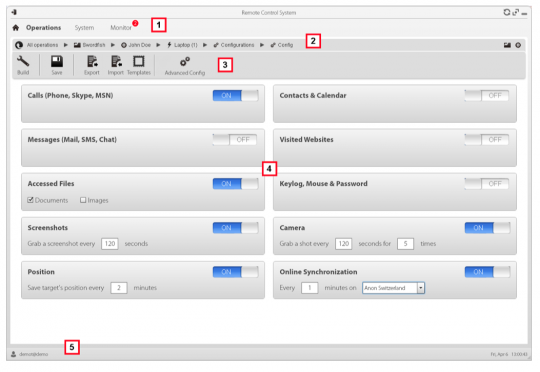
And set up to start recording:
The “analyst” can then explore and take virtually anything from the target’s phone or computer, at least according to the manual.
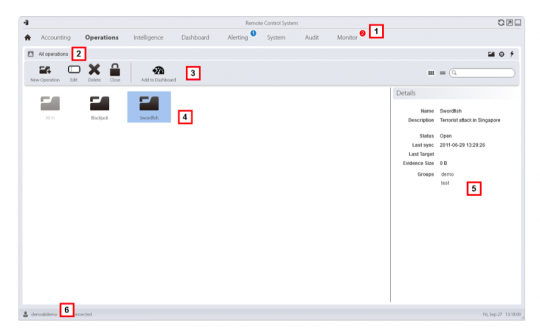
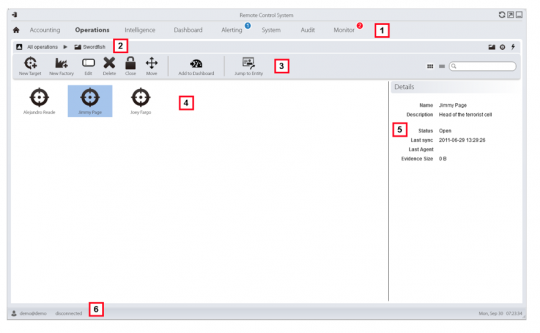
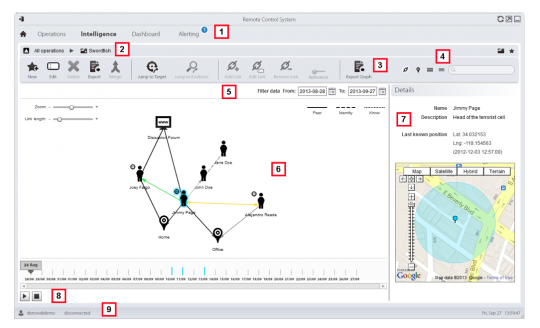
Here our analyst selects an investigation – code-named “Swordfish,” and described as a “Terrorist Attack in Singapore.”
Opening that up, he sees the targets in swordfish – “Alejandro Reade,” “Joey Fargo,” and “Jimmy Page” – “head of the terrorist cell.”
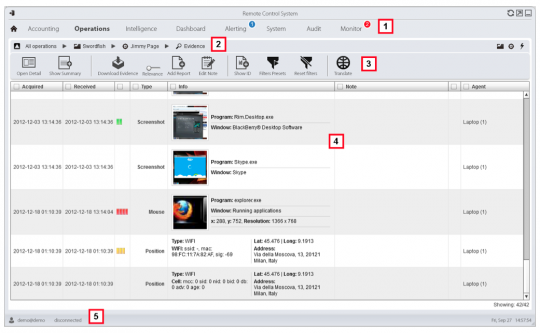
Here’s what he’s looking at on Jimmy’s computer: his desktop, Skype account, Firefox browsing. All of that can be exported from the bugged device to the spy’s computer, undetected.
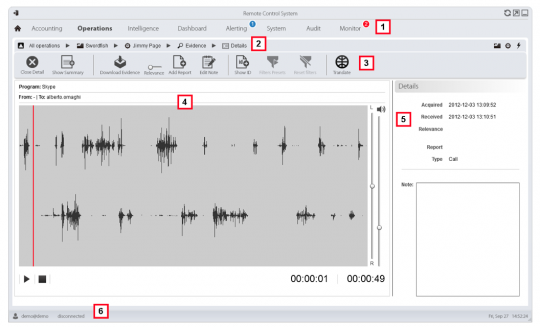
But before he sends everything off to his higher-ups, he can have a listen, to decide if it’s relevant:
And can even translate it:
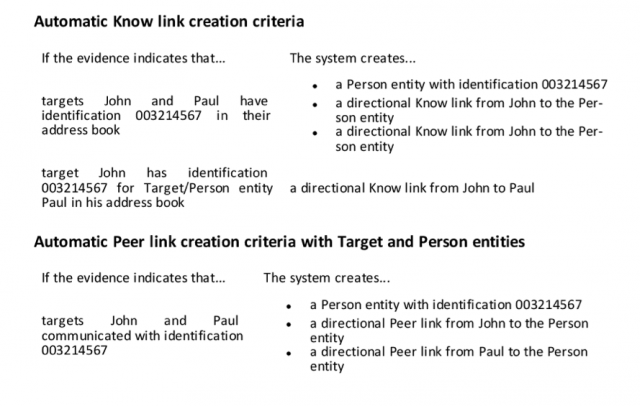
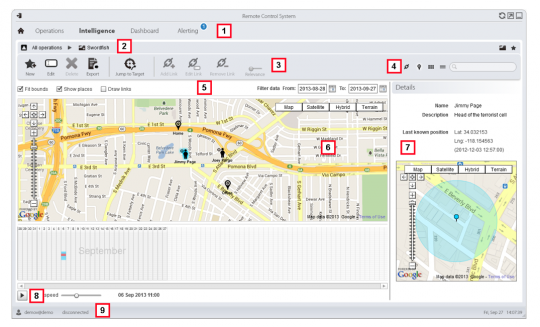
Once he’s got all that, he maps out the various people and places tied to his target.
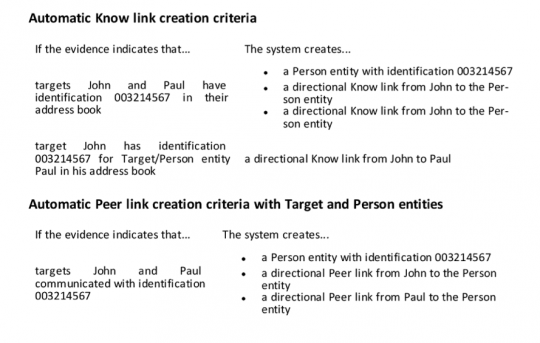
Entities are automatically linked by the software based on their contacts – either as a “know,” a “peer,” or an “identity” (ie., two addresses associated with the same person.)
Here are Jimmy and his friends in an industrial lot in Los Angeles:
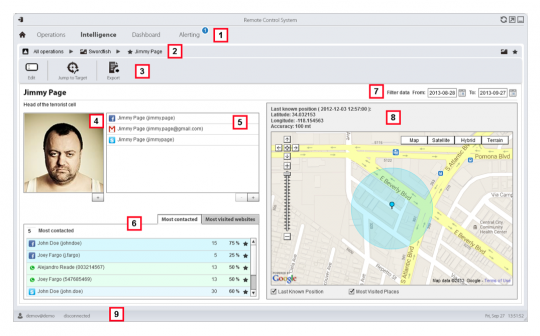
And here’s the man himself, with all his vital stats. Web sites and physical locations get similar profiles. That photo, the manual notes, will default to the “first image captured by the webcam.”
For more on how this all works, see Citizen Lab’s report, and explore the full set of documents below.
Manuals
Hacking Team RCS 9 Analyst’s Guide (PDF)
Hacking Team RCS 9 Administrator’s Guide (PDF)
Hacking Team RCS 9 Technician’s Guide (PDF)
Hacking Team RCS 9 System Administrator’s Guide (PDF)
Hacking Team RCS Invisibility Report (PDF)
Hacking Team RCS 9.0 Changelog (PDF)
Hacking Team RCS 9.1 Changelog (PDF)
_________________________________
Top Photo: Pablo Blazquez Dominguez/Getty Images; Vincenzetti: Google+
Email the authors: cora.currier@theintercept.com, morgan@firstlook.org
Go to Original – firstlook.org
DISCLAIMER: The statements, views and opinions expressed in pieces republished here are solely those of the authors and do not necessarily represent those of TMS. In accordance with title 17 U.S.C. section 107, this material is distributed without profit to those who have expressed a prior interest in receiving the included information for research and educational purposes. TMS has no affiliation whatsoever with the originator of this article nor is TMS endorsed or sponsored by the originator. “GO TO ORIGINAL” links are provided as a convenience to our readers and allow for verification of authenticity. However, as originating pages are often updated by their originating host sites, the versions posted may not match the versions our readers view when clicking the “GO TO ORIGINAL” links. This site contains copyrighted material the use of which has not always been specifically authorized by the copyright owner. We are making such material available in our efforts to advance understanding of environmental, political, human rights, economic, democracy, scientific, and social justice issues, etc. We believe this constitutes a ‘fair use’ of any such copyrighted material as provided for in section 107 of the US Copyright Law. In accordance with Title 17 U.S.C. Section 107, the material on this site is distributed without profit to those who have expressed a prior interest in receiving the included information for research and educational purposes. For more information go to: http://www.law.cornell.edu/uscode/17/107.shtml. If you wish to use copyrighted material from this site for purposes of your own that go beyond ‘fair use’, you must obtain permission from the copyright owner.
Read more
Click here to go to the current weekly digest or pick another article:
WHISTLEBLOWING - SURVEILLANCE: