Canada Casts Global Surveillance Dragnet Over File Downloads
WHISTLEBLOWING - SURVEILLANCE, 2 Feb 2015
Ryan Gallagher and Glenn Greenwald – The Intercept
28 Jan 2015 – Canada’s leading surveillance agency is monitoring millions of Internet users’ file downloads in a dragnet search to identify extremists, according to top-secret documents.
The covert operation, revealed Wednesday [28 Jan 2015] by CBC News in collaboration with The Intercept, taps into Internet cables and analyzes records of up to 15 million downloads daily from popular websites commonly used to share videos, photographs, music, and other files.
The revelations about the spying initiative, codenamed LEVITATION, are the first from the trove of files provided by National Security Agency whistleblower Edward Snowden to show that the Canadian government has launched its own globe-spanning Internet mass surveillance system.
According to the documents, the LEVITATION program can monitor downloads in several countries across Europe, the Middle East, North Africa, and North America. It is led by the Communications Security Establishment, or CSE, Canada’s equivalent of the NSA. (The Canadian agency was formerly known as “CSEC” until a recent name change.)
The latest disclosure sheds light on Canada’s broad existing surveillance capabilities at a time when the country’s government is pushing for a further expansion of security powers following attacks in Ottawa and Quebec last year.
Ron Deibert, director of University of Toronto-based Internet security think tank Citizen Lab, said LEVITATION illustrates the “giant X-ray machine over all our digital lives.”
“Every single thing that you do – in this case uploading/downloading files to these sites – that act is being archived, collected and analyzed,” Deibert said, after reviewing documents about the online spying operation for CBC News.
David Christopher, a spokesman for Vancouver-based open Internet advocacy group OpenMedia.ca, said the surveillance showed “robust action” was needed to rein in the Canadian agency’s operations.
“These revelations make clear that CSE engages in large-scale warrantless surveillance of our private online activities, despite repeated government assurances to the contrary,” Christopher told The Intercept.
The ostensible aim of the surveillance is to sift through vast amounts of data to identify people uploading or downloading content that could be connected to terrorism – such as bomb-making guides and hostage videos.
In the process, however, CSE combs through huge volumes of data showing uploads and downloads initiated by Internet users not suspected of any wrongdoing.
In a top-secret PowerPoint presentation, dated from mid-2012, an analyst from the agency jokes about how, while hunting for extremists, the LEVITATION system gets clogged with information on innocuous downloads of the musical TV series Glee.
CSE finds some 350 “interesting” downloads each month, the presentation notes, a number that amounts to less than 0.0001 per cent of the total collected data.
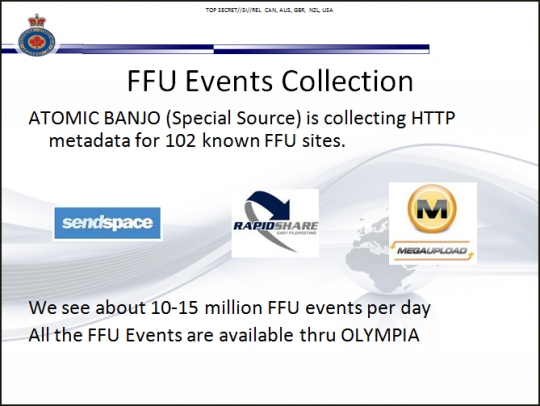
The agency stores details about downloads and uploads to and from 102 different popular file-sharing websites, according to the 2012 document, which describes the collected records as “free file upload,” or FFU, “events.” Only three of the websites are named: RapidShare, SendSpace, and the now defunct MegaUpload.
SendSpace said in a statement that “no organization has the ability/permission to trawl/search Sendspace for data,” adding that its policy is not to disclose user identities unless legally compelled. Representatives from RapidShare and MegaUpload had not responded to a request for comment at time of publication.
LEVITATION does not rely on cooperation from any of the file-sharing companies. A separate secret CSE operation codenamed ATOMIC BANJO obtains the data directly from internet cables that it has tapped into, and the agency then sifts out the unique IP address of each computer that downloaded files from the targeted websites.
The IP addresses are valuable pieces of information to CSE’s analysts, helping to identify people whose downloads have been flagged as suspicious. The analysts use the IP addresses as a kind of search term, entering them into other surveillance databases that they have access to, such as the vast repositories of intercepted Internet data shared with the Canadian agency by the NSA and its British counterpart Government Communications Headquarters.
If successful, the searches will return a list of results showing other websites visited by the people downloading the files – in some cases revealing associations with Facebook or Google accounts. In turn, these accounts may reveal the names and the locations of individual downloaders, opening the door for further surveillance of their activities.
Since the secret 2012 presentation about LEVITATION was authored, both RapidShare and SendSpace have toughened security by encrypting users’ connections to their websites, which may have thwarted CSE’s ability to target them for surveillance. But many other popular file-sharing sites have still not adopted encryption, meaning they remain vulnerable to the snooping.
As of mid-2012, CSE was maintaining a list of 2,200 particular download links that it regarded as connected to suspicious “documents of interest.” Anyone clicking on those links could have found themselves subject to extra scrutiny from the spies.
While LEVITATION is purportedly identifying potential terror threats, Canadian legal experts consulted by CBC News were concerned by the broad scope of the operation.
“The specific uses that they talk about in this [counter-terrorism] context may not be the problem, but it’s what else they can do,” said Tamir Israel, a lawyer with the University of Ottawa’s Canadian Internet Policy and Public Interest Clinic. Picking which downloads to monitor is essentially “completely at the discretion of CSE,” Israel added.
The file-sharing surveillance also raises questions about the number of Canadians whose downloading habits could have been swept up as part of LEVITATION’s dragnet.
By law, CSE isn’t allowed to target Canadians. In the LEVITATION presentation, however, two Canadian IP addresses that trace back to a web server in Montreal appear on a list of suspicious downloads found across the world. The same list includes downloads that CSE monitored in closely allied countries, including the United Kingdom, United States, Spain, Brazil, Germany and Portugal.
It is unclear from the document whether LEVITATION has ever prevented any terrorist attacks. The agency cites only two successes of the program in the 2012 presentation: the discovery of a hostage video through a previously unknown target, and an uploaded document that contained the hostage strategy of a terrorist organization. The hostage in the discovered video was ultimately killed, according to public reports.
A CSE spokesman told The Intercept and CBC News in a statement: “CSE is legally authorized to collect and analyze metadata, including from parts of the Internet routinely used by terrorists. Some of CSE`s metadata analysis activities are designed to identify foreign terrorists who use the Internet to conduct activities that threaten the security of Canada and Canadian citizens.
“CSE does not direct its activities at Canadians or anyone in Canada, and, in accordance with our legislation, has a range of measures in place to protect the privacy of Canadians incidentally encountered in the course of these foreign intelligence operations.”
The spokesman declined to comment on whether LEVITATION remained active, and would not provide examples of useful intelligence gleaned from the spying, or explain how long data swept up under the operation is retained.
Discussion of “operations, methods or capabilities,” the spokesman said, would breach the Security of Information Act, a Canadian law designed to protect state secrets.
Go to Original – firstlook.org
DISCLAIMER: The statements, views and opinions expressed in pieces republished here are solely those of the authors and do not necessarily represent those of TMS. In accordance with title 17 U.S.C. section 107, this material is distributed without profit to those who have expressed a prior interest in receiving the included information for research and educational purposes. TMS has no affiliation whatsoever with the originator of this article nor is TMS endorsed or sponsored by the originator. “GO TO ORIGINAL” links are provided as a convenience to our readers and allow for verification of authenticity. However, as originating pages are often updated by their originating host sites, the versions posted may not match the versions our readers view when clicking the “GO TO ORIGINAL” links. This site contains copyrighted material the use of which has not always been specifically authorized by the copyright owner. We are making such material available in our efforts to advance understanding of environmental, political, human rights, economic, democracy, scientific, and social justice issues, etc. We believe this constitutes a ‘fair use’ of any such copyrighted material as provided for in section 107 of the US Copyright Law. In accordance with Title 17 U.S.C. Section 107, the material on this site is distributed without profit to those who have expressed a prior interest in receiving the included information for research and educational purposes. For more information go to: http://www.law.cornell.edu/uscode/17/107.shtml. If you wish to use copyrighted material from this site for purposes of your own that go beyond ‘fair use’, you must obtain permission from the copyright owner.
Read more
Click here to go to the current weekly digest or pick another article:
WHISTLEBLOWING - SURVEILLANCE: