The Hunter –> He Was a Hacker for the NSA and He Was Willing to Talk. I Was Willing to Listen.
WHISTLEBLOWING - SURVEILLANCE, 4 Jul 2016
28 Jun 2016 –The message arrived at night and consisted of three words: “Good evening sir!”
The sender was a hacker who had written a series of provocative memos at the National Security Agency. His secret memos had explained — with an earthy use of slang and emojis that was unusual for an operative of the largest eavesdropping organization in the world — how the NSA breaks into the digital accounts of people who manage computer networks, and how it tries to unmask people who use Tor to browse the web anonymously. Outlining some of the NSA’s most sensitive activities, the memos were leaked by Edward Snowden, and I had written about a few of them for The Intercept.
There is no Miss Manners for exchanging pleasantries with a man the government has trained to be the digital equivalent of a Navy SEAL. Though I had initiated the contact, I was wary of how he might respond. The hacker had publicly expressed a visceral dislike for Snowden and had accused The Intercept of jeopardizing lives by publishing classified information. One of his memos outlined the ways the NSA reroutes (or “shapes”) the internet traffic of entire countries, and another memo was titled “I Hunt Sysadmins.” I felt sure he could hack anyone’s computer, including mine.
Good evening sir!
The only NSA workers the agency has permitted me to talk with are the ones in its public affairs office who tell me I cannot talk with anyone else. Thanks to the documents leaked by Snowden, however, I have been able to write about a few characters at the NSA.
There was, for instance, a novelist-turned-linguist who penned an ethics column for the NSA’s in-house newsletter, and there was a mid-level manager who wrote an often zany advice column called “Ask Zelda!” But their classified writings, while revealing, could not tell me everything I wanted to know about the mindset of the men and women who spy on the world for the U.S. government.
I got lucky with the hacker, because he recently left the agency for the cybersecurity industry; it would be his choice to talk, not the NSA’s. Fortunately, speaking out is his second nature. While working for the NSA, he had publicly written about his religious beliefs, and he was active on social media. So I replied to his greeting and we began an exchange of cordial messages. He agreed to a video chat that turned into a three-hour discussion sprawling from the ethics of surveillance to the downsides of home improvements and the difficulty of securing your laptop. “I suppose why I talk is partially a personal compulsion to not necessarily reconcile two sides or different viewpoints but to just try to be honest about the way things are,” he told me. “Does that make sense?”
The hacker was at his home, wearing a dark hoodie that bore the name of one of his favorite heavy metal bands, Lamb of God. I agreed not to use his name in my story, so I’ll just refer to him as the Lamb. I could see a dime-store bubble-gum machine behind him, a cat-scratching tree, and attractive wood beams in the ceiling. But his home was not a tranquil place. Workmen were doing renovations, so the noise of a buzz saw and hammering intruded, his wife called him on the phone, and I could hear the sound of barking. “Sorry, my cats are taunting my dog,” he said, and later the animal in question, a black-and-white pit bull, jumped onto his lap and licked his face.
The Lamb wore a T-shirt under his hoodie and florid tattoos on his arms and smiled when I said, mostly in jest, that his unruly black beard made him look like a member of the Taliban, though without a turban. He looked very hacker, not very government.
When most of us think of hackers, we probably don’t think of government hackers. It might even seem odd that hackers would want to work for the NSA — and that the NSA would want to employ them. But the NSA employs legions of hackers, as do other agencies, including the FBI, CIA, DEA, DHS, and Department of Defense. Additionally, there are large numbers of hackers in the corporate world, working for military contractors like Booz Allen, SAIC, and Palantir. The reason is elegantly simple: You cannot hack the world without hackers.
In popular shows and movies such as “Mr. Robot” and “The Matrix,” hackers tend to be presented as unshaven geeks loosely connected to collectives like Anonymous, or to Romanian crime syndicates that steal credit cards by the millions, or they are teenagers who don’t realize their online mischief will get them into a boatload of trouble when Mom finds out.
The stereotypes differ in many ways but share a trait: They are transgressive anti-authoritarians with low regard for social norms and laws. You would not expect these people to work for The Man, but they do, in droves. If you could poll every hacker in the U.S. and ask whether they practice their trade in dark basements or on official payrolls, a large number would likely admit to having pension plans. Who knows, it could be the majority.
This may qualify as one of the quietest triumphs for the U.S. government since 9/11: It has co-opted the skills and ideals of a group of outsiders whose anti-establishment tilt was expressed two decades ago by Matt Damon during a famous scene in Good Will Hunting. Damon, playing a math genius being recruited by the NSA, launches into a scathing riff about the agency serving the interests of government and corporate evil rather than ordinary people. Sure, he could break a code for the NSA and reveal the location of a rebel group in North Africa or the Middle East, but the result would be a U.S. bombing attack in which “1,500 people that I never met, never had a problem with, get killed.” He turns down the offer.
In recent years, two developments have helped make hacking for the government a lot more attractive than hacking for yourself. First, the Department of Justice has cracked down on freelance hacking, whether it be altruistic or malignant. If the DOJ doesn’t like the way you hack, you are going to jail. Meanwhile, hackers have been warmly invited to deploy their transgressive impulses in service to the homeland, because the NSA and other federal agencies have turned themselves into licensed hives of breaking into other people’s computers. For many, it’s a techno sandbox of irresistible delights, according to Gabriella Coleman, a professor at McGill University who studies hackers. “The NSA is a very exciting place for hackers because you have unlimited resources, you have some of the best talent in the world, whether it’s cryptographers or mathematicians or hackers,” she said. “It is just too intellectually exciting not to go there.”
Revealingly, one of the documents leaked by Snowden and published by The Intercept last year was a classified interview with a top NSA hacker (not the Lamb) who exulted that his job was awesome because “we do things that you can’t do anywhere else in the country … at least not legally. We are gainfully employed to hack computers owned by al-Qa’ida!” Asked about the kind of people he works with at the NSA, he replied, “Hackers, geeks, nerds … There’s an annual event for hackers in Las Vegas called DEF CON, and many of us attend. When there, we feel as though we are among our bretheren! [sic] We all have a similar mindset of wanting to tear things apart, to dig in, to see how things work.”
In 2012, Gen. Keith Alexander, the NSA director at the time, even attended DEF CON wearing blue jeans and a black T-shirt that bore the logo of the Electronic Frontier Foundation, an anti-surveillance organization that is beloved by hackers and other good citizens of the world. To coincide with Alexander’s visit, the NSA had created a special webpage to recruit the hackers at DEF CON. “If you have a few, shall we say, indiscretions in your past, don’t be alarmed,” the webpage stated. “You shouldn’t automatically assume you won’t be hired.” Alexander’s personal pitch was even more direct: “In this room right here is the talent we need.”
If you are willing to become a patriot hacker, Uncle Sam wants you.
As a teenager, the Lamb was a devout Christian who attended church two or three times a week, yet he also participated in online forums for Satanists and atheists. He wanted to learn what others believed and why they believed it, and he wanted to hear their responses to questions he raised. If his beliefs could not withstand challenges from opposing ones, they might not be worth keeping.
“As a Christian, I believe the Bible, and one of the things it says is if you seek the truth, you should find it,” he told me. “If I started to come across facts that contradicted what I believed and contradicted the way that I thought about things, I had to be open to confronting them and determining how I would integrate them into my life and my thought system.”
Before he became a hacker, the Lamb had the restless spirit of one. After high school, he attended a Christian university for a year but dropped out and joined the military as a linguist. He was assigned to the NSA, and although he told me his computer skills were modest at the time, he was intrigued by the mysteries inside the machines. “I started doing some basic computer training, like ‘Oh, here’s how computers talk to each other and network’ and that sort of stuff,” he said. “I enjoyed that far more than trying to maintain a language that I rarely used.”
He devoured books on computers and experimented on his own time, using an application called Wireshark to see how network data was moving to and from his own computer. He picked up a bit of programming knowledge, and he asked agency veterans for tips. As he wrote in one of his memos, “If you want to learn crazy new things … why not walk around NSA, find people in offices that do things you find interesting, and talk to them about how they do what they do.”
Like Snowden, he did not need a formal education to succeed. Snowden, after all, dropped out of high school and mastered computers through self-education. As an NSA contractor, he rose to a position that gave him access to broad swaths of the agency’s networks. While Snowden was a systems administrator, the Lamb became an expert in network analysis and was well-versed in the crucial trick of shaping traffic from one place to another — for instance, sending it from an ISP in a foreign country to an NSA server.
The Lamb’s work was important, but his memos are remarkably irreverent, even cocky. I’ve read a fair number of NSA documents, and not one contains as much hacker and internet lingo as his; he used words like “skillz” and “internetz” and “ZOMG!” and phrases like “pwn the network” and “Dude! Map all the networks!!!” Some of what he wrote is just cheerily impudent, like the opening line of one memo: “Happy Friday my esteemed and valued intelligence Community colleagues!” Another memo began, “Welcome back, comrade!”
While poking gentle fun at the government hackers he worked with, the Lamb dismissed the amateur hackers on the outside. He identified himself and his highly trained colleagues at the NSA as a breed apart — a superior breed, much in the way that soldiers look down on weekend paintballers. Perhaps this shouldn’t be altogether surprising, because arrogance is one of the unfortunate hallmarks of the male-dominated hacker culture. At the NSA, this hubris can perhaps serve as an ethical lubricant that eases the task of hacking other people: They are not as special as you are, they do not have the magical powers you possess, they are targets first and humans second.
As the Lamb wrote in one of his memos, “When I first went to Blackhat/Defcon, it was with the wide-eyed anticipation of ‘I’m going to go listen to all of the talks that I can, soak up all of the information possible, and become a supar-1337-haxxor.’ What a let-down of an experience that was. You find the most interesting topics and briefings, wait in lines to get a seat, and find yourself straining your ears to listen to someone that has basically nothing new to say. Most of the talks get hyped up exponentially past any amount of substance they actually provide.”
Then I asked the Lamb where he was in the hierarchy of hackers at the NSA, he just smiled and said, “I got to the point where more people would ask me questions than I asked other people questions.” He would not delve into the classified specifics of his job — he despises Snowden for leaking classified information — but I knew a lot through his memos.
Although network analysis, the Lamb’s area of expertise, is interesting from a technical perspective, he was one step removed from the most challenging and menacing type of government hacking — executing finely tuned attacks that infiltrate individual computers. Nonetheless, he offered this characterization of his NSA work: “They were just ridiculously cool projects that I’ll never forget.” One of the quandaries of technology is that “cool” does not necessarily mean “ethical.” Surveillance tools that are regarded as breakthroughs can be used to spy on innocent people as well as terrorists. This is a key part of the debate on the NSA, the concern that its formidable powers are being used, or can be used, to undermine privacy, freedom, and democracy.
The Lamb’s memos on cool ways to hunt sysadmins triggered a strong reaction when I wrote about them in 2014 with my colleague Ryan Gallagher. The memos explained how the NSA tracks down the email and Facebook accounts of systems administrators who oversee computer networks. After plundering their accounts, the NSA can impersonate the admins to get into their computer networks and pilfer the data flowing through them. As the Lamb wrote, “sys admins generally are not my end target. My end target is the extremist/terrorist or government official that happens to be using the network … who better to target than the person that already has the ‘keys to the kingdom’?”
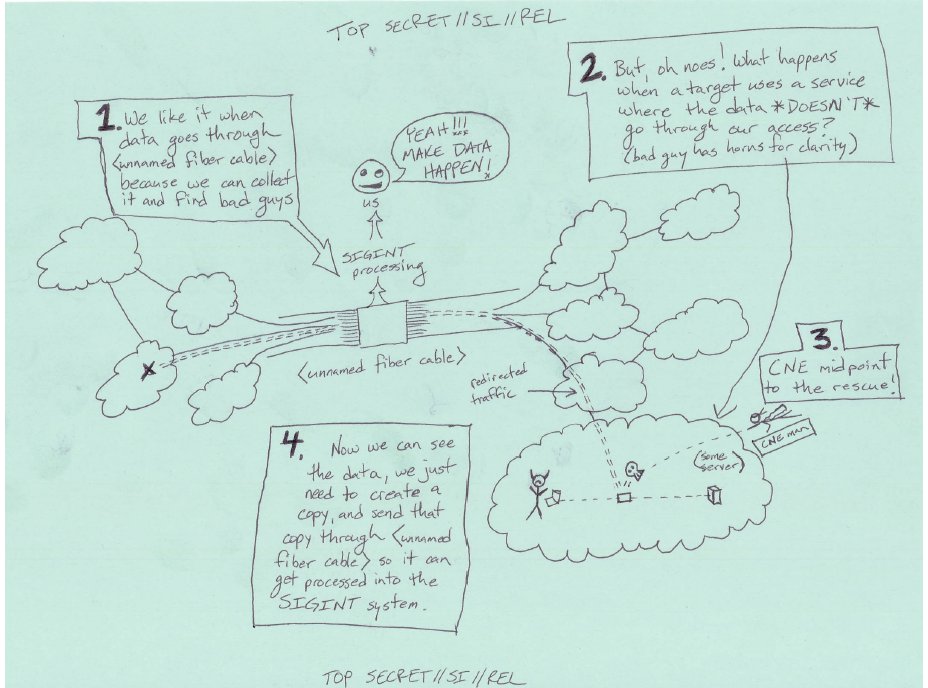
Another of his NSA memos, “Network Shaping 101,” used Yemen as a theoretical case study for secretly redirecting the entirety of a country’s internet traffic to NSA servers. The presentation, consisting of a PowerPoint slideshow, was offbeat at times, with a reference to throwing confetti in the air when a hack worked and jokey lines like, “The following section could also be renamed the ‘I’m pulling my hair out in the fetal position while screaming “Why didn’t it work?!”’ section.” The Lamb also scribbled a hand-drawn diagram about network shaping that included a smiley face in the middle next to the phrase, “YEAH!!! MAKE DATA HAPPEN!” The diagram and slideshow were both classified as top secret.
His memos are boastful, even cackling. At the end of one of the sysadmin memos, the Lamb wrote, “Current mood: scheming,” and at the end of another, “Current mood: devious.” He also listed “juche-licious” as one of his moods, ironically referring to the official ideology of North Korea. Another memo he wrote, “Tracking Targets Through Proxies & Anonymizers,” impishly noted that the use of identity-obscuring tools like Tor “generally makes for sad analysts” in the intelligence community; this was followed by a sad face emoji. The tone of his classified writing was consistent with some of his social media posts — the Lamb’s attitude, in public as well as in private, was often outspoken and brash.
What if the shoe was on the other foot, however? When I wrote about the sysadmin memos in 2014, I wondered how their author would feel if someone used the same devious rationale to hack his computer and his life. Nearly two years later, I had the chance to find out.
“If I turn the tables on you,” I asked the Lamb, “and say, OK, you’re a target for all kinds of people for all kinds of reasons. How do you feel about being a target and that kind of justification being used to justify getting all of your credentials and the keys to your kingdom?”
The Lamb smiled. “There is no real safe, sacred ground on the internet,” he replied. “Whatever you do on the internet is an attack surface of some sort and is just something that you live with. Any time that I do something on the internet, yeah, that is on the back of my mind. Anyone from a script kiddie to some random hacker to some other foreign intelligence service, each with their different capabilities — what could they be doing to me?”
He seemed to be putting the blame for NSA attacks on the victims — if they were too dimwitted to protect themselves from hunters like him, it was their fault. “People don’t want to think about being targets on the internet, in spite of the fact that at this point in the game, everybody is,” he added. “Every country spies.”
He was dead serious, no smiles any longer. “As much as we’d like to say we will all beat our swords into plowshares and become a peaceful people, it’s not going to happen,” he continued. “Intelligence agencies around the world are being asked questions by their governments, and government officials don’t want to hear, ‘That’s hard to solve.’ They just say, ‘Can you solve this and can you get me the intel I’m asking for?’ Which is nation agnostic, whether that’s the NSA, the FSB, the PLA or whoever.”
The Lamb’s political ideology evoked the cold-blooded realpolitik of Henry Kissinger. There is the idyllic digital world we would like to live in, there is the dog-eat-dog digital world we actually live in — and the Lamb, as I understood it, was intensely focused on winning in the latter.
“You know, the situation is what it is,” he said. “There are protocols that were designed years ago before anybody had any care about security, because when they were developed, nobody was foreseeing that they would be taken advantage of. … A lot of people on the internet seem to approach the problem [with the attitude of] ‘I’m just going to walk naked outside of my house and hope that nobody looks at me.’ From a security perspective, is that a good way to go about thinking? No, horrible … There are good ways to be more secure on the internet. But do most people use Tor? No. Do most people use Signal? No. Do most people use insecure things that most people can hack? Yes. Is that a bash against the intelligence community that people use stuff that’s easily exploitable? That’s a hard argument for me to make.”
But it wasn’t a hard argument for me to make, so I tried. Back in the 1990s, in the early days of the web, the uses and hopes for the internet were thought to be joyous and non-commercial. The web would let us talk to one another and would decentralize power and revolutionize the world in good ways. Those were the years when the Lamb spent hours and hours in chatrooms with Satanists and atheists — just the sort of connect-us-to-each-other activity that made everyone so excited about the future. At the time, few people thought the internet would become, as Bruce Schneier describes it, a surveillance platform. So I asked whether the Lamb felt conflicted, as Snowden did, working for an organization that turned the web further and further away from its original potential as a global platform for speaking and thinking freely.
He responded by noting that he is, by nature, a defiant type and attracted to hard problems. That’s how, without a lot of formal instruction, he became an NSA hacker — he was curious about how computers worked and he wanted to figure them out. “Technically challenging things are just inherently interesting to me,” he said. “If you tell me, ‘This can’t be done,’ I’m going to try and find a way to do it.”
I mentioned that lots of people, including Snowden, are now working on the problem of how to make the internet more secure, yet he seemed to do the opposite at the NSA by trying to find ways to track and identify people who use Tor and other anonymizers. Would he consider working on the other side of things? He wouldn’t rule it out, he said, but dismally suggested the game was over as far as having a liberating and safe internet, because our laptops and smartphones will betray us no matter what we do with them.
“There’s the old adage that the only secure computer is one that is turned off, buried in a box ten feet underground, and never turned on,” he said. “From a user perspective, someone trying to find holes by day and then just live on the internet by night, there’s the expectation [that] if somebody wants to have access to your computer bad enough, they’re going to get it. Whether that’s an intelligence agency or a cybercrimes syndicate, whoever that is, it’s probably going to happen.”
The Lamb was comfortable with the side he joined in the surveillance wars, and this sets him apart from the most common stereotypes of the men and women who devote their lives to spying on others.
Spies who do nothing but eavesdrop, slipping into computers and conversations without a trace, have a reputation in popular culture of being troubled in ways that conventional spies are not. Think of Gene Hackman in The Conversation, or Ulrich Mühe in The Lives of Others — these surveillers are haunted, as it seems they should be. Conventional spies are seen as journeying into hostile lands and committing heroic or devious acts; they are men and women of action, not thought. But the people who watch, listen, or hack are not as distracted by danger or adrenaline. They mostly labor in tranquility, in temperature-controlled offices without windows, risking bodily harm no worse than carpal tunnel syndrome, and they have an abundance of time to think about the lurking that is their occupation and the people on whom they practice it.
I have a bias against the watchers, I suppose. I have been concerned about the bureaucracies of surveillance since the 1980s, when I was a student in the Soviet Union and felt like hunted prey. The telephone in the dreary lobby of my dormitory on the banks of the Neva River in Leningrad (now St. Petersburg) was assumed to be bugged, and if the KGB’s devices weren’t working, the dezhurnaya who sat nearby was sure to be listening. This was my anti-surveillance Rosebud, I guess. When I visited Russian friends, I stayed silent as I walked in their ill-lit stairwells, so that the accent of my Russian would not give away the fact a foreigner was visiting them. The walls had ears. This was one of the great contrasts between the Soviet Union and America, where I could speak to my friends without worrying about the government listening.
The Soviet Union is long gone, but in 2016 we live under the specter of far more surveillance than anything the KGB could have dreamed of with its rudimentary bugs and fearful informers. Not just government surveillance — law enforcement can easily obtain our phone and internet records with a warrant from the nearly always compliant courts — but corporate surveillance, too. It’s not just Google and Facebook that might know more details about our lives and friends than the KGB could have imagined in its most feverish dreams of information dominance, but even Zipcar and Amazon.
There are precautions one can take, and I did that with the Lamb. When we had our video chat, I used a computer that had been wiped clean of everything except its operating system and essential applications. Afterward, it was wiped clean again. My concern was that the Lamb might use the session to obtain data from or about the computer I was using; there are a lot of things he might have tried, if he was in a scheming mood. At the end of our three hours together, I mentioned to him that I had taken these precautions—and he approved.
“That’s fair,” he said. “I’m glad you have that appreciation. … From a perspective of a journalist who has access to classified information, it would be remiss to think you’re not a target of foreign intelligence services.”
He was telling me the U.S. government should be the least of my worries. He was trying to help me.
Documents published with this article:
- Tracking Targets Through Proxies & Anonymizers
- Network Shaping 101
- Shaping Diagram
- I Hunt Sys Admins (first published in 2014)
_______________________________________
Related:
 What Happens When a Failed Writer Becomes a Loyal Spy?
What Happens When a Failed Writer Becomes a Loyal Spy?
 The NSA Has An Advice Columnist. Seriously.
The NSA Has An Advice Columnist. Seriously.
 Inside the NSA’s Secret Efforts to Hunt and Hack System Administrators
Inside the NSA’s Secret Efforts to Hunt and Hack System Administrators
Peter Maass – ✉peter.maass@theintercept.com
Go to Original – theintercept.com
DISCLAIMER: The statements, views and opinions expressed in pieces republished here are solely those of the authors and do not necessarily represent those of TMS. In accordance with title 17 U.S.C. section 107, this material is distributed without profit to those who have expressed a prior interest in receiving the included information for research and educational purposes. TMS has no affiliation whatsoever with the originator of this article nor is TMS endorsed or sponsored by the originator. “GO TO ORIGINAL” links are provided as a convenience to our readers and allow for verification of authenticity. However, as originating pages are often updated by their originating host sites, the versions posted may not match the versions our readers view when clicking the “GO TO ORIGINAL” links. This site contains copyrighted material the use of which has not always been specifically authorized by the copyright owner. We are making such material available in our efforts to advance understanding of environmental, political, human rights, economic, democracy, scientific, and social justice issues, etc. We believe this constitutes a ‘fair use’ of any such copyrighted material as provided for in section 107 of the US Copyright Law. In accordance with Title 17 U.S.C. Section 107, the material on this site is distributed without profit to those who have expressed a prior interest in receiving the included information for research and educational purposes. For more information go to: http://www.law.cornell.edu/uscode/17/107.shtml. If you wish to use copyrighted material from this site for purposes of your own that go beyond ‘fair use’, you must obtain permission from the copyright owner.
Read more
Click here to go to the current weekly digest or pick another article:
WHISTLEBLOWING - SURVEILLANCE: