The Drone Papers – Find, Fix, Finish (4 of 8)
SPECIAL FEATURE, 19 Oct 2015
Jeremy Scahill – The Intercept
[The Intercept has obtained a cache of secret documents detailing the inner workings of the U.S. military’s assassination program in Afghanistan, Yemen, and Somalia. The documents, provided by a whistleblower, offer an unprecedented glimpse into Obama’s drone wars. The source said he decided to provide these documents to The Intercept because he believes the public has a right to understand the process by which people are placed on kill lists and ultimately assassinated on orders from the highest echelons of the U.S. government.]
- The Assassination Complex
- A Visual Glossary
- The Kill Chain
- Find, Fix, Finish
- Manhunting in the Hindu Kush
- Firing Blind
- The Life and Death of Objective Peckham
- Target Africa
- The Alphabet of Assassination (Glossary of Terms)
For the Pentagon, creating an architecture of assassination meant navigating a turf war with the CIA.
Soon after he was elected president, Barack Obama was strongly urged by Michael Hayden, the outgoing CIA director, and his new top counterterrorism adviser, John Brennan, to adopt the way of the scalpel — small footprint counterterrorism operations and drone strikes. In one briefing, Hayden bluntly told Obama that covert action was the only way to confront al Qaeda and other terrorist groups plotting attacks against the U.S.
15 Oct 2015 – The view among Obama’s inner circle was that Iraq and Afghanistan had served as useful laboratories for such tactics, but deploying them outside conventional war zones meant different legal and diplomatic considerations would apply. An all-star team of special operations commanders, war planners, and Pentagon officials pressed the new president to dramatically ramp up the shadow wars in Yemen and Somalia to fight the emerging threats in those countries. They called for sweeping away bureaucratic obstacles and streamlining lethal operations.
In short, a new global architecture of assassination was called for, and that meant navigating an increasingly tense turf war between the CIA and the Pentagon over these activities.
The CIA had long dominated the covert war in Pakistan, and in 2009 Obama expanded the agency’s drone resources there and in Afghanistan to regularly pound al Qaeda, the Pakistani Taliban, and other targets. The military, tasked with prosecuting the broader war in Afghanistan, was largely sidelined in the Pakistan theater, save for the occasional cross-border raid and the Air Force personnel who operated the CIA’s drones. But the Pentagon was not content to play a peripheral role in the global drone war, and aggressively positioned itself to lead the developing drone campaigns in Yemen and Somalia.
In September 2009, then-Centcom Commander Gen. David Petraeus issued a Joint Unconventional Warfare Task Force Execute Order that would lay the groundwork for military forces to conduct expanded clandestine actions in Yemen and other countries. It allowed for U.S. special operations forces to enter friendly and unfriendly countries “to build networks that could ‘penetrate, disrupt, defeat or destroy’ al Qaeda and other militant groups, as well as to ‘prepare the environment’ for future attacks by American or local military forces.”
At the same time, al Qaeda in the Arabian Peninsula and al Shabaab both began to escalate their rhetoric — and, in AQAP’s case, to plot terror attacks on U.S. soil. After the failed Christmas Day “underwear” bomb plot over Detroit, the Obama administration responded by greenlighting special operations commanders’ plans for direct action.
In December 2009, the Obama administration signed off on its first covert airstrike in Yemen — a cruise missile attack that killed more than 40 people, most of them women and children. After that strike, as with the CIA’s program in Pakistan, drones would fuel the Joint Special Operations Command’s high-value targeting campaign in the region.
When Obama took office, there had been only one U.S. drone strike in Yemen — in November 2002. By 2012, there was a drone strike reported in Yemen every six days. As of August 2015, more than 490 people had been killed in drone strikes in Yemen alone.
“The drone campaign right now really is only about killing. When you hear the phrase ‘capture/kill,’ capture is actually a misnomer. In the drone strategy that we have, ‘capture’ is a lower case ‘c.’ We don’t capture people anymore,” Lt. Gen. Michael Flynn, former head of the Defense Intelligence Agency, told The Intercept. “Our entire Middle East policy seems to be based on firing drones. That’s what this administration decided to do in its counterterrorism campaign. They’re enamored by the ability of special operations and the CIA to find a guy in the middle of the desert in some shitty little village and drop a bomb on his head and kill him.”
**
The tip of the spear in the Obama administration’s escalated wars in East Africa and the Arabian Peninsula was a special operations task force known as TF 48-4, according to secret documents provided to The Intercept. In response to a series of detailed questions, a Defense Department spokesperson said, “We don’t comment on the details of classified reports.”
The task force’s primary command center was at the former French Army outpost at Camp Lemonnier in Djibouti, a small African nation nestled between Ethiopia, Eritrea, Somalia, and the Gulf of Aden. With its strategic location, Lemonnier served as the hub for launching actions from military facilities scattered across the region. The task force also utilized a maritime drone platform and a surveillance apparatus positioned in the Arabian Sea, used for intercepting data. TF 48-4 had sites in Nairobi and Sanaa and a drone base in Arba Minch, Ethiopia. A small base in Manda Bay, Kenya — a stone’s throw from Somalia — housed special operations commandos and manned aircraft.
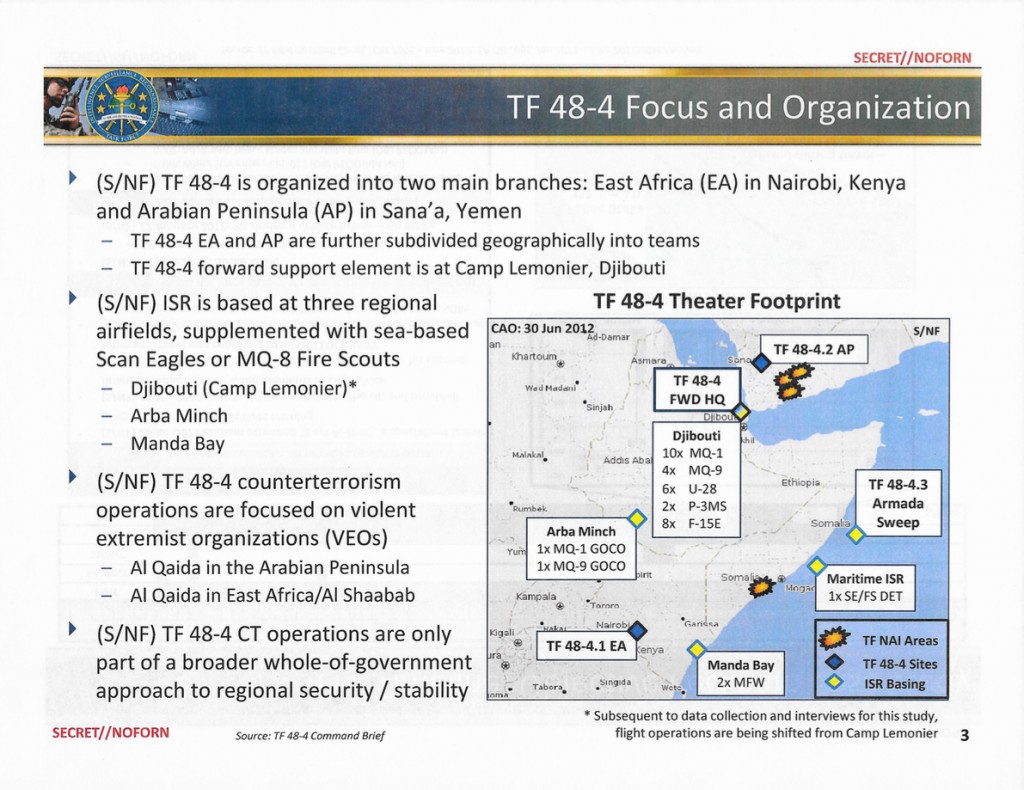
A slide from a classified Pentagon study outlines the air and naval assets of the secret task force charged with hunting down, killing, and capturing high-value individuals in Somalia and Yemen.
The task force’s operations, aimed at hunting down and killing or capturing members of AQAP and al Shabaab, were largely conducted with drones and fixed-wing aircraft. On occasion, small teams of special operators mounted ground operations inside Somalia and Yemen, or interdicted ships, snatching suspected terrorists. But drones were the administration’s preferred weapon.
“It is the politically advantageous thing to do — low cost, no U.S. casualties, gives the appearance of toughness,” said Adm. Dennis Blair, Obama’s former director of national intelligence, explaining how the administration viewed its policy at the time. “It plays well domestically, and it is unpopular only in other countries. Any damage it does to the national interest only shows up over the long term.”
As Yemen’s status began to rise to the top of U.S. counterterrorism priorities, the long-simmering turf war between the Pentagon and the CIA flared up. In 2011, the CIA began using a newly constructed drone base in Saudi Arabia, giving it easier access to targets in Yemen than the military’s bases in East Africa. There were parallel, and competing, target lists and infighting over who should run the drone war in Yemen. At times, this drama played out on the pages of the New York Times and the Washington Post — with leaks coming from both sides in an effort to influence policy. The CIA’s backers in Congress argued that the agency showed more “patience and discretion” in its drone strikes, while some prominent military advocates portrayed the agency as ill-equipped to conduct military-style operations and less accountable to Congress.
At the peak of this bureaucratic civil war, in 2012, an influential and well-funded Defense Department entity, the Intelligence, Surveillance, and Reconnaissance Task Force, began preparing a classified brief on challenges faced by special operations forces conducting counterterrorism operations in East Africa and the Arabian Peninsula, such as those operating under TF 48-4. The ISR Task Force fell under the control of Michael Vickers, a powerful veteran of CIA paramilitary operations. Obama had promoted Vickers in 2010 to undersecretary of defense for intelligence, and as the Pentagon’s top intelligence official he exerted great influence over matters of covert operations.
The task force had been established in 2008 to study the intelligence and surveillance needs of war fighters in Afghanistan and Iraq. By 2012, it had evolved into a multibillion-dollar advocacy wing pushing for the purchase of new surveillance technologies to support the military’s black ops forces in waging unconventional wars.
The purpose of the ISR study, in outlining the challenges faced by special operations units tasked with disrupting and destroying terrorist networks, was to press for more tools and to collect data that would guide future operations.
The Intercept obtained two versions of the study, both titled “ISR Support to Small Footprint CT Operations — Somalia/Yemen.” One slide deck, a detailed report, was distributed in February 2013, and another, an executive summary, was circulated in May 2013, the month President Obama gave the first major address of his presidency on drones and targeted killings. The timing of the reports is interesting, because it was during this period that the Obama administration began to publicly advance the idea of handing control of the drone program to the military.
“The United States has taken lethal, targeted action against al Qaeda and its associated forces, including with remotely piloted aircraft commonly referred to as drones,” Obama said in front of a military audience. “As was true in previous armed conflicts, this new technology raises profound questions — about who is targeted, and why; about civilian casualties, and the risk of creating new enemies; about the legality of such strikes under U.S. and international law; about accountability and morality.” Drone strikes, he asserted, are “effective” and legal.
Obama did not mention TF 48-4 in his speech, but it was the actions of the special operations task force — and those of the CIA’s parallel program — that he was discussing.
During the period covered in the ISR study — January 2011 through June 2012 — three U.S. citizens were killed in drone strikes in Yemen. Only one, the radical preacher Anwar al Awlaki, was labeled the intended target of the strike. The U.S. claimed it did not intend to kill Samir Khan, who was traveling with Awlaki when a Hellfire hit their vehicle. The third — and most controversial — killing of a U.S. citizen was that of Awlaki’s son, 16-year-old Abdulrahman Awlaki. He was killed two weeks after his father, while having dinner with his cousin and some friends. Immediately after the strike, anonymous U.S. officials asserted that the younger Awlaki was connected to al Qaeda and was 21 years old. After the family produced his birth certificate, the U.S. changed its position, with an anonymous official calling the killing of the teenager an “outrageous mistake.”
A former senior official in the Obama administration, who worked on the high-value targeting program and asked not to be identified because he was discussing classified material, told me in 2013 that after the Abdulrahman strike, the president was “surprised and upset and wanted an explanation.” “We had no idea the kid was there,” the official said. The White House did not officially acknowledge the strikes until nearly two years later. “We killed three U.S. citizens in a very short period,” he told me. “Two of them weren’t even targets: Samir Khan and Abdulrahman Awlaki. That doesn’t look good. It’s embarrassing.”
The former senior official said that John Brennan, President Obama’s top counterterrorism adviser, “suspected that the kid had been killed intentionally and ordered a review. I don’t know what happened with the review.” When asked about the review, a spokesperson for the National Security Council told me, “We cannot discuss the sensitive details of specific operations.”
Lt. Gen. Flynn, who since leaving the DIA has become an outspoken critic of the Obama administration, charges that the White House relies heavily on drone strikes for reasons of expediency, rather than effectiveness. “We’ve tended to say, drop another bomb via a drone and put out a headline that ‘we killed Abu Bag of Doughnuts’ and it makes us all feel good for 24 hours,” Flynn said. “And you know what? It doesn’t matter. It just made them a martyr, it just created a new reason to fight us even harder.”

Lt. Gen. Michael Flynn, former head of the Defense Intelligence Agency, was an architect of JSOC’s find, fix, finish doctrine.
Photo: Michael Reynolds/EPA/Landov
Glenn Carle, a former senior CIA officer, disputes Flynn’s characterization of the Obama administration’s motive in its widespread use of drones. “I would be skeptical the government would ever make that formal decision to act that way,” Carle, who spent more than two decades in the CIA’s clandestine services, told The Intercept. “Obama is always attacked by the right as being soft on defense and not able to make the tough decisions. That’s all garbage. The Obama administration has been quite ruthless in its pursuit of terrorists. If there are people who we, in our best efforts, assess to be trying to kill us, we can make their life as short as possible. And we do it.”
TF 48-4, according to the documents, did in fact have an impressive cache of firepower in Djibouti to kill or capture people approved for the kill list by the president. According to one slide, as of 2012 the base at Camp Lemonnier housed more than a dozen armed drones and additional surveillance aircraft. Its arsenal also included eight manned F-15E warplanes, which can carry so-called bunker busters — 5,000-pound laser-guided bombs.
The ISR Task Force recommended providing special operations forces with more and better drones and an enhanced mandate to capture and interrogate suspects “via host-nation partners.”
Outsourcing U.S. kill/capture operations to local forces, which occurred frequently throughout the Bush administration’s time in office, regularly led to human rights abuses, torture, and extrajudicial killings. “I’m very hesitant on backing foreign militaries or paramilitary forces or militias,” said Clinton Watts, a former FBI special agent who worked on counterterrorism and later served as an executive officer of the Combating Terrorism Center at West Point. “I’ve seen that up close before and you’re backing rape and pillage campaigns through the countryside, usually. You can’t control them and you don’t have transparency over what they do and it blows up in your face the same way that a bad drone strike does.”
The ISR Task Force asserted that an increase in the number of capture operations could be achieved by using U.S. “advisors” to build partnerships with local forces and by conducting “advance force operations.” AFOs are used by the U.S. military to discreetly plant tracking devices, conduct surveillance, and physically access places inhabited by potential targets, often in “denied areas” where the U.S. is not yet at war. Forces deployed in AFOs may also conduct clandestine “direct actions,” including kill/capture operations.
During the Bush administration, AFOs served as a primary vehicle for justifying the clandestine deployment of U.S. special operators across the world to engage in “operational preparation” of a future battlespace. Those activities expanded as the Bush administration adopted the view that, post 9/11, “the entire world is the ‘battlespace.’”
A July 2015 U.S. government contract solicitation for training Pacific Command personnel who conduct AFOs envisioned a course that would focus on tactics “that directly or indirectly support technical surveillance operations in non-permissive environments.” Among them: breaking and bypassing a slew of locks, both physical and digital; cloning hotel room key cards; picking advanced car lock systems; and learning “physical restraint escape techniques.” The solicitation stated that operatives need such courses to “remain proficient in this highly refined skill set.”
***
The tone of the ISR study at times gives the impression that special operations forces were effectively prisoners of resource shortages and a legal bureaucracy that interfered with the military’s ability to kill or capture terrorists with the frequency, efficiency, and urgency demanded by policymakers.
Those sentiments were echoed by Lt. Gen. Flynn, who served for years as the chief intelligence officer for JSOC. “You cannot conduct counterinsurgency, counterterrorism, or counter-guerrilla operations without having effective interrogation operations,” Flynn said in an interview. “If the president says, ‘Defeat this enemy,’ but you say you need resources that you never get, you just can’t defeat the enemy. Without the ability to capture or interrogate, your effectiveness when conducting counterterrorism operations can be cut in half, if not even lower than that, and that’s the challenge that we face.”
Carle, the former senior CIA officer, said the ISR study is part of the “classic” turf war. “If you get the budget,” he said, “then you control the decisions and everybody thinks that whatever toys they control are the toys that need to be used and therefore you need more of them.” The Pentagon wants “to expand their influence,” he added, “because then you don’t have obstreperous and disheveled civilian CIA guys who clink glasses in salons telling you how to do things. They don’t want that. That’s a classic turf institutional tension.”
The study, which utilizes corporate language to describe lethal operations as though they were a product in need of refining and upgrading, includes analyses from IBM, which has boasted that its work for the Pentagon “integrates commercial consulting methods with tacit knowledge of the mission, delivering work products and advice that improve operations and creates [sic] new capabilities.”
The study compared the tempo and methods of conventional operations in which U.S. personnel were on the ground in large numbers — as in Iraq and Afghanistan — to the shadow wars in Yemen and Somalia, where there was a scant and sporadic U.S. military presence. Unlike in Iraq and Afghanistan, where special operations units were given carte blanche to engage in a systematic kill/capture program, in Somalia and Yemen they were required to operate under more stringent rules and guidelines. “When compared to previous operations,” the study asserted, “the amount of time required to action objectives is literally orders of magnitude higher.”
The CIA has operated in Pakistan with looser requirements for obtaining the president’s direct approval before launching strikes; the president also waived the requirement that a CIA target present an “imminent” threat.
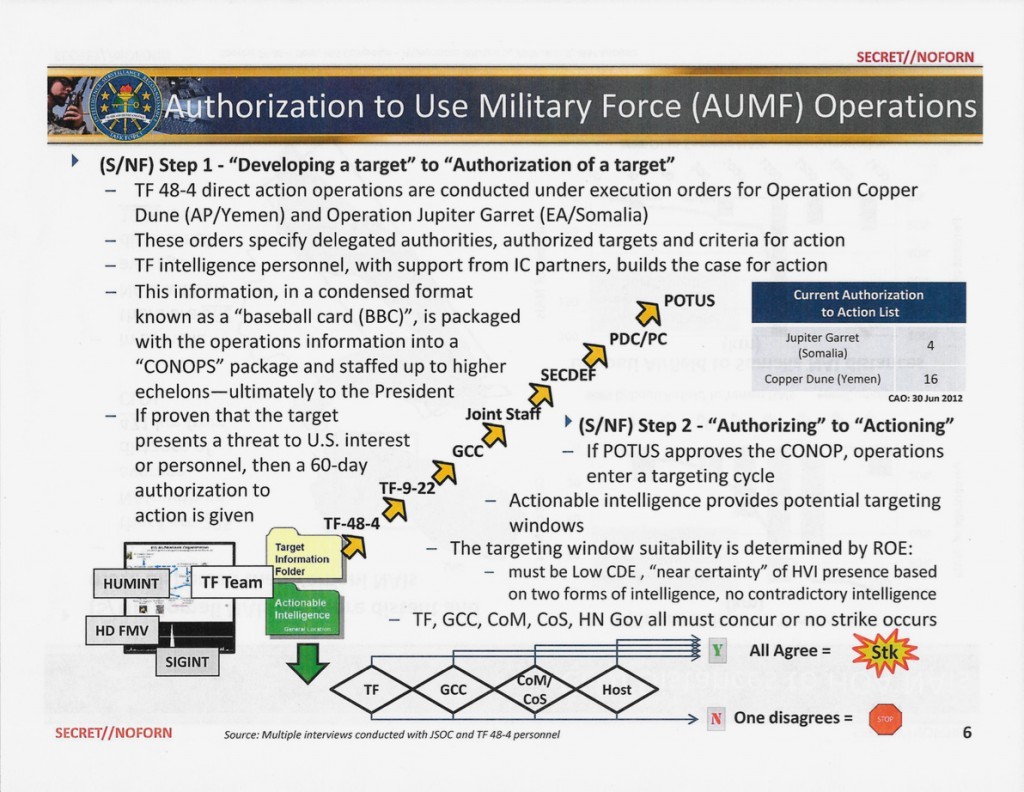
A slide from a May 2013 Pentagon presentation shows the chain of command for ordering drone strikes and other operations carried out by JSOC in Yemen and Somalia.
GCC = Geographic Combatant Command; SECDEF = Secretary of Defense; PDC/PC = Principals’ Deputies Committee/Principals Committee; CoM = Chief of Mission; CoS = Chief of Station
One slide outlined the bureaucracy involved in authorizing the military to conduct high-value strikes, a process that in some cases took years. “Relatively few high-level terrorists meet criteria for targeting under the provisions,” the study said, and the “near certainty” standard for positively identifying a target and requirements of “low” collateral damage “reduces targeting opportunities.” The study lamented the technical difficulties in achieving positive identification of a targeted person and guaranteeing minimal collateral damage, particularly when insufficient numbers of drones and full motion video platforms caused “blinking” in the surveillance apparatus.
One former senior special operations officer, who asked not to be identified because he was discussing classified materials, told The Intercept that the ISR study was best understood as a “bitch brief.” The message, he said, was, “We can’t do what you’re asking us to do because you are not giving us the resources to get it done.”
As the Obama era draws to a close, the internal debate over control of the drone program continues, with some reports suggesting the establishment of a “dual command” structure for the CIA and the military. For now, it seems that the military is getting much of what it agitated for in the ISR study. In August, the Wall Street Journal reported that the military plans to “sharply expand the number of U.S. drone flights over the next four years, giving military commanders access to more intelligence and greater firepower to keep up with a sprouting number of global hot spots.” The paper reported that drone flights would increase by 50 percent by 2019, adding: “While expanding surveillance, the Pentagon plan also grows the capacity for lethal airstrikes.”
_______________________________
Contact the author Jeremy Scahill: jeremy.scahill@theintercept.com
Go to Original – theintercept.com
DISCLAIMER: The statements, views and opinions expressed in pieces republished here are solely those of the authors and do not necessarily represent those of TMS. In accordance with title 17 U.S.C. section 107, this material is distributed without profit to those who have expressed a prior interest in receiving the included information for research and educational purposes. TMS has no affiliation whatsoever with the originator of this article nor is TMS endorsed or sponsored by the originator. “GO TO ORIGINAL” links are provided as a convenience to our readers and allow for verification of authenticity. However, as originating pages are often updated by their originating host sites, the versions posted may not match the versions our readers view when clicking the “GO TO ORIGINAL” links. This site contains copyrighted material the use of which has not always been specifically authorized by the copyright owner. We are making such material available in our efforts to advance understanding of environmental, political, human rights, economic, democracy, scientific, and social justice issues, etc. We believe this constitutes a ‘fair use’ of any such copyrighted material as provided for in section 107 of the US Copyright Law. In accordance with Title 17 U.S.C. Section 107, the material on this site is distributed without profit to those who have expressed a prior interest in receiving the included information for research and educational purposes. For more information go to: http://www.law.cornell.edu/uscode/17/107.shtml. If you wish to use copyrighted material from this site for purposes of your own that go beyond ‘fair use’, you must obtain permission from the copyright owner.

