The Drone Papers – Firing Blind (6 of 8)
SPECIAL FEATURE, 26 Oct 2015
Cora Currier and Peter Maass – The Intercept
[The Intercept has obtained a cache of secret documents detailing the inner workings of the U.S. military’s assassination program in Afghanistan, Yemen, and Somalia. The documents, provided by a whistleblower, offer an unprecedented glimpse into Obama’s drone wars. The source said he decided to provide these documents to The Intercept because he believes the public has a right to understand the process by which people are placed on kill lists and ultimately assassinated on orders from the highest echelons of the U.S. government.]
Flawed Intelligence and the Limits of Drone Technology
- The Assassination Complex
- A Visual Glossary
- The Kill Chain
- Find, Fix, Finish
- Manhunting in the Hindu Kush
- Firing Blind
- The Life and Death of Objective Peckham
- Target Africa
- The Alphabet of Assassination (Glossary of Terms)
The Obama administration has portrayed drones as an effective and efficient weapon in the ongoing war with al Qaeda and other radical groups. Yet classified Pentagon documents obtained by The Intercept reveal that the U.S. military has faced “critical shortfalls” in the technology and intelligence it uses to find and kill suspected terrorists in Yemen and Somalia.
15 Oct 2015 – Those shortfalls stem from the remote geography of Yemen and Somalia and the limited American presence there. As a result, the U.S. military has been overly reliant on signals intelligence from computers and cellphones, and the quality of those intercepts has been limited by constraints on surveillance flights in the region.
The documents are part of a study by a Pentagon Task Force on Intelligence, Surveillance, and Reconnaissance. They provide details about how targets were tracked for lethal missions carried out by the Joint Special Operations Command, or JSOC, in Yemen and Somalia between January 2011 and summer 2012. When the study was circulated in 2013, the Obama administration was publicly floating the idea of moving the bulk of its drone program to the Pentagon from the CIA, and the military was eager to make the case for more bases, more drones, higher video quality, and better eavesdropping equipment.
Yet by identifying the challenges and limitations facing the military’s “find, fix, finish” operations in Somalia and Yemen — the cycle of gathering intelligence, locating, and attacking a target — the conclusions of the ISR study would seem to undermine the Obama administration’s claims of a precise and effective campaign, and lend support to critics who have questioned the quality of intelligence used in drone strikes.
The study made specific recommendations for improving operations in the Horn of Africa, but a Pentagon spokesperson, Cmdr. Linda Rojas, declined to explain what, if any, measures had been taken in response to the study’s findings, saying only that “as a matter of policy we don’t comment on the details of classified reports.”
The Tyranny of Distance
One of the most glaring problems identified in the ISR study was the U.S. military’s inability to carry out full-time surveillance of its targets in the Horn of Africa and Yemen. Behind this problem lies the “tyranny of distance” — a reference to the great lengths that aircraft must fly to their targets from the main U.S. air base in Djibouti, the small East African nation that borders Somalia and sits just across the Gulf of Aden from Yemen.
Surveillance flights are limited by fuel — and, in the case of manned aircraft, the endurance of pilots. In contrast with Iraq, where more than 80 percent of “finishing operations” were conducted within 150 kilometers of an air base, the study notes that “most objectives in Yemen are ~ 500 km away” from Djibouti and “Somalia can be over 1,000 km.” The result is that drones and planes can spend half their air time in transit, and not enough time conducting actual surveillance.
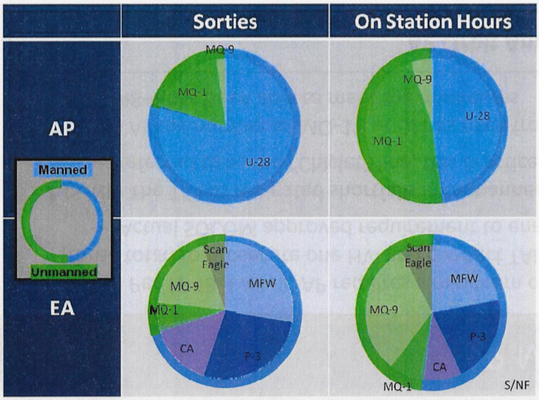
A Pentagon chart showing that as of June 2012 manned spy planes accounted for the majority of flights over Yemen, even though drones were more efficient, since they could spend more time over a target. Over Somalia, the military used a mix of manned and unmanned aircraft.
AP = Arabian Peninsula; EA = East Africa.
Compounding the tyranny of distance, the ISR study complained, was the fact that JSOC had too few drones in the region to meet the requirements mandated for carrying out a finishing operation. The military measures surveillance flights in orbits — meaning continuous, unbroken coverage of a target — and JSOC chronically failed to meet “minimum requirements” for orbits over Yemen, and in the case of Somalia had never met the minimum standards. On average, 15 flights a day, by multiple aircraft relieving or complementing one another, were needed to complete three orbits over Yemen.
The “sparse” available resources meant that aircraft had to “cover more potential leads — stretching coverage and leading to [surveillance] ‘blinks.’” Because multiple aircraft needed to be “massed” over one target before a strike, surveillance of other targets temporarily ceased, thus breaking the military’s ideal of a “persistent stare” or the “unblinking eye” of around-the-clock tracking.
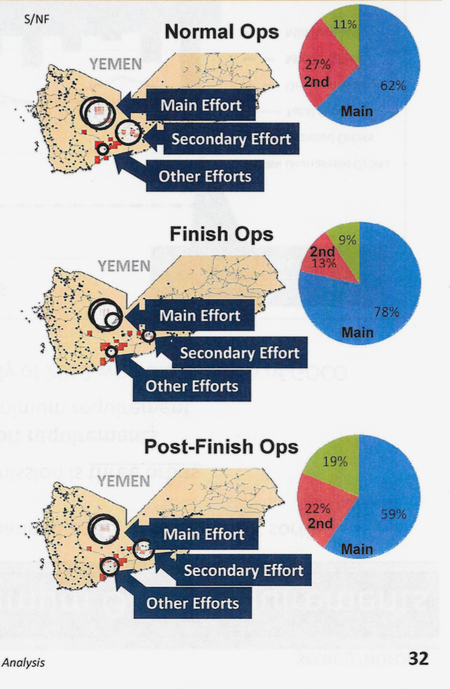
When the military was focused on a “finish” — meaning kill — operation, drones were taken off the surveillance of other targets.
JSOC relied on manned spy planes to fill the orbit gap over Yemen. In June 2012 there were six U-28 spy planes in operation in East Africa and the Arabian Peninsula, as well as several other types of manned aircraft. The U-28s in Djibouti were “referred to as the ‘Chiclet line,’” according to the ISR study, and “compounded Djiboutian air control issues” because of their frequent flights.
Only in the summer of 2012, with the addition of contractor-operated drones based in Ethiopia and Fire Scout unmanned helicopters, did Somalia have the minimum number of drones commanders wanted. The number of Predator drones stationed in Djibouti doubled over the course of the study, and in 2013, the fleet was moved from the main U.S. air base, Camp Lemonnier, to another Djibouti airstrip because of overcrowding and a string of crashes.
“Blinking” remained a concern, however, and the study recommended adding even more aircraft to the area of operations. Noting that political and developmental issues hampered the military’s ability to build new bases, it suggested expanding the use of aircraft launched from ships. JSOC already made use of Fire Scout helicopter drones and small Scan Eagle drones off the coast of Somalia, as well as “Armada Sweep,” which a 2011 document from the National Security Agency, provided by former contractor Edward Snowden, describes as a “ship-based collection system” for electronic communications data. (The NSA declined to comment on Armada Sweep.)
Lt. Gen. Michael Flynn, who was head of the Defense Intelligence Agency from July 2012 to August 2014, told The Intercept that the surveillance requirements he outlined for tracking al Qaeda while in office had never been met. “We end up spending money on other stupid things instead of actually the capabilities that we need,” he said. “This is not just about buying more drones, it’s a whole system that’s required.”
According to Micah Zenko, a senior fellow at the Council on Foreign Relations who has closely studied the drone war, resource constraints in Africa “mean less time for the persistent stare that counterterrorism analysts and commanders want, and got used to in the Afghanistan-Pakistan theater.”
Find, Fix, Finish
The find, fix, finish cycle is known in the military as FFF, or F3. But just as critical are two other letters: E and A, for “exploit and analyze,” referring to the use of materials collected on the ground and in detainee interrogations.
F3EA became doctrine in counterinsurgency campaigns in Iraq and Afghanistan in the mid-2000s. Gen. Stanley McChrystal wrote in his memoir that the simplicity of those “five words in a line … belied how profoundly it would drive our mission.” In 2008, Flynn, who worked closely with McChrystal before becoming head of the Defense Intelligence Agency, wrote that “Exploit-Analyze starts the cycle over again by providing leads, or start points, into the network that could be observed and tracked using airborne ISR.”
Deadly strikes thus truncate the find, fix, finish cycle without exploitation and analysis — precisely the components that were lacking in the drone campaign waged in East Africa and Yemen. That shortfall points to one of the contradictions at the heart of the drone program in general: Assassinations are intelligence dead ends.
The ISR study shows that after a “kill operation” there is typically nobody on the ground to collect written material or laptops in the target’s house, or the phone on his body, or capture suspects and ask questions. Yet collection of on-the-ground intelligence of that sort — referred to as DOMEX, for “document and media exploitation,” and TIR, for “tactical interrogation report” — is invaluable for identifying future targets.
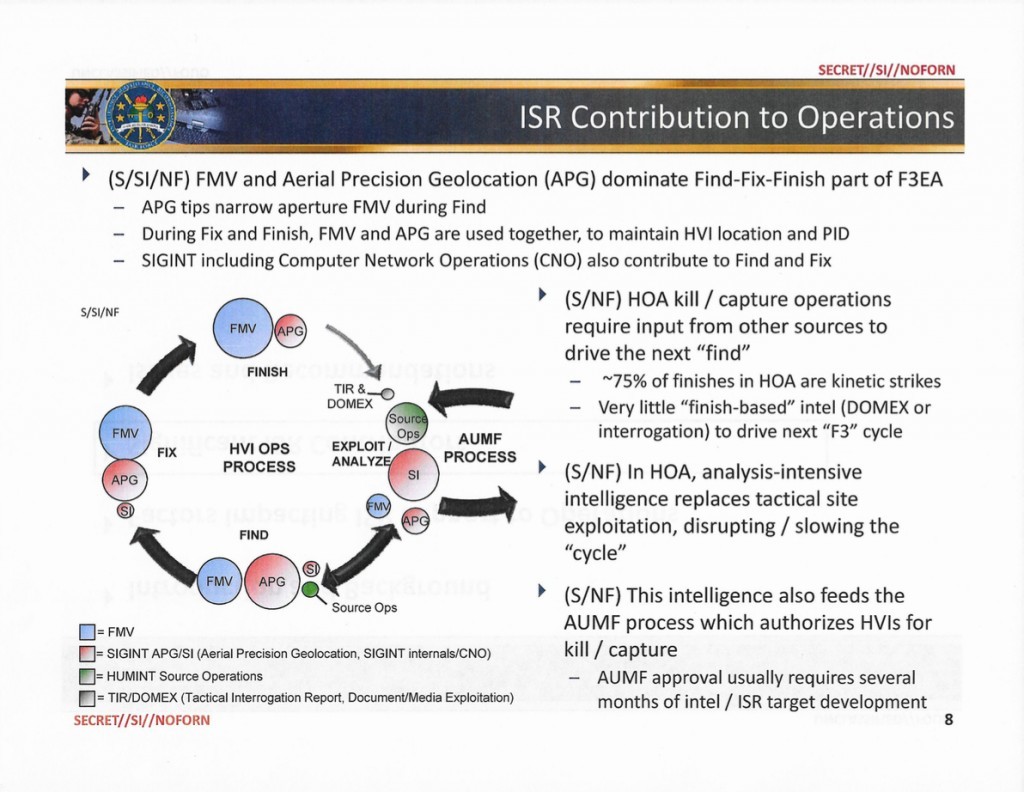
A slide from a Pentagon study notes that deadly strikes in Yemen and Somalia reduce the amount of intelligence for future operations.
AUMF = 2001 Authorization for Use of Military Force; FMV = Full Motion Video; F3EA = Find, Fix, Finish, Exploit, Analyze; HOA = Horn of Africa
Stating that 75 percent of operations in the region were strikes, and noting that “kill operations significantly reduce the intelligence available from detainees and captured material,” the study recommended an expansion of “capture finishes via host-nation partners for more ‘finish-derived’ intelligence.” One of the problems with that scenario, however, is that security forces in host nations like Yemen and Somalia are profoundly unreliable and have been linked to a wide variety of abuses, including the torture of prisoners.
A report last year by retired Gen. John Abizaid and former Defense Department official Rosa Brooks noted that the “enormous uncertainties” of drone warfare are “multiplied further when the United States relies on intelligence and other targeting information provided by a host nation government: How can we be sure we are not being drawn into a civil war or being used to target the domestic political enemies of the host state leadership?”
In 2011, for example, U.S. officials told the Wall Street Journal that they had killed a local governor because Yemeni officials didn’t tell them he was present at a gathering of al Qaeda figures. “We think we got played,” one official said. (The Yemeni government disputed the report.)
Despite such warnings, the drone program has relied heavily on intelligence from other countries. One slide describes signals intelligence, or SIGINT, as coming “often from foreign partners,” and another, titled “Alternatives to Exploit/Analyze,” states that “in the reduced access environment, national intelligence partners often have the best information and access.”
The military relies heavily on intelligence from electronic communications, much of it provided by foreign governments, but acknowledges that the information is “neither as timely nor as focused as tactical intelligence.”
One way to increase the reliability of host-nation intelligence is to be directly involved in its collection — but this can be risky for soldiers on the ground. The study called for “advance force operations,” including “small teams of special force advisors,” to work with foreign forces to capture combatants, interrogate them, and seize any written material or electronic devices they possess. According to public Special Operations guidelines, advance force operations “prepare for near-term” actions by planting tracking devices, conducting reconnaissance missions, and staging for attacks. The documents obtained by The Intercept did not specify an optimum number of advisors or where they should be based or how exactly they should be involved in capture or interrogation operations.
Although the study dates from 2013, current Special Operations Commander Joseph Votel echoed its findings in July 2015. Votel noted that his troops were working closely with African Union forces and the Somali government to battle al Shabaab. He added, “We get a lot more … when we actually capture somebody or we capture material than we do when we kill someone.”

A man walks past destroyed buildings in Zinjibar, capital of Abyan province in southern Yemen on Dec. 5, 2012.
Photo: Sami-al-Ansi/AFP/Getty Images
The Poverty of Signals Intelligence
With limited ability to conduct raids or seize materials from targeted individuals in Yemen and Somalia, JSOC relied overwhelmingly on monitoring electronic communications to discover and ultimately locate targets.
The documents state bluntly that SIGINT is an inferior form of intelligence. Yet signals accounted for more than half the intelligence collected on targets, with much of it coming from foreign partners. The rest originated with human intelligence, primarily obtained by the CIA. “These sources,” the study notes, “are neither as timely nor as focused as tactical intelligence” from interrogations or seized materials.
Making matters worse, the documents refer to “poor” and “limited” capabilities for collecting SIGINT, implying a double bind in which kill operations were reliant on sparse amounts of inferior intelligence.
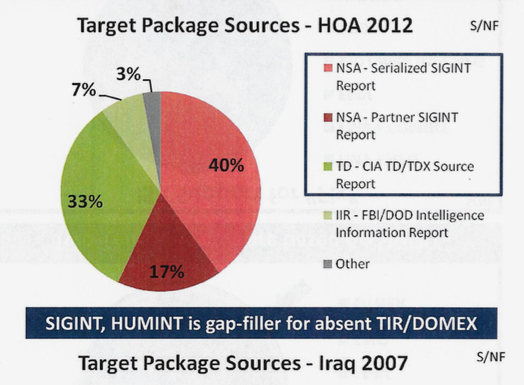
The disparity with other areas of operation was stark, as a chart contrasting cell data makes clear: In Afghanistan there were 8,900 cell data reports each month, versus 50 for Yemen and 160 for Somalia. Despite that, another chart shows SIGINT comprised more than half the data sources that went into developing targets in Somalia and Yemen in 2012.
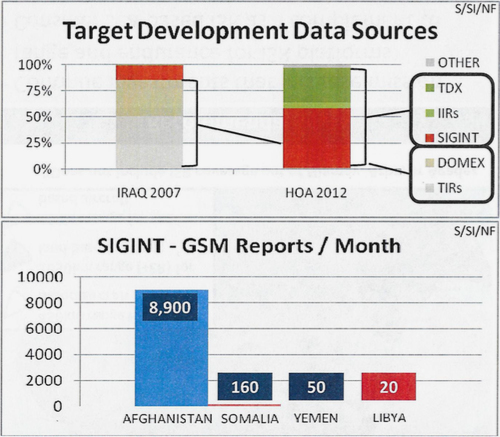
Cellphone data was critical for finding and identifying targets, yet a chart from a Pentagon study shows that the military had far less information in Yemen and Somalia than it was accustomed to having in Afghanistan.
DOMEX = Document and Media Exploitation; GSM = Global System for Mobile communication; HOA = Horn of Africa; IIRs = Intelligence Information Reports; SIGINT = Signals Intelligence; TIRs = Tactical Interrogation Reports.
Flynn told The Intercept there was “way too much reliance on technical aspects [of intelligence], like signals intelligence, or even just looking at somebody with unmanned aerial vehicles.”
“I could get on the telephone from somewhere in Somalia, and I know I’m a high-value target, and say in some coded language, ‘The wedding is about to occur in the next 24 hours,’” Flynn said. “That could put all of Europe and the United States on a high-level alert, and it may be just total bullshit. SIGINT is an easy system to fool and that’s why it has to be validated by other INTs — like HUMINT. You have to ensure that the person is actually there at that location because what you really intercepted was the phone.”
In addition to using SIGINT to identify and find new targets, the documents detail how military analysts also relied on such intelligence to make sure that they had the correct person in their sights and to estimate the harm to civilians before a strike. After locating a target, usually by his cellphone or other electronics, analysts would study video feeds from surveillance aircraft “to build near-certainty via identification of distinguishing physical characteristics.”
A British intelligence document on targeted killing in Afghanistan, which was among the Snowden files, describes a similar process of “monitoring a fixed location, and tracking any persons moving away from that location, and identifying if a similar pattern is experienced through SIGINT collect.” The document explains that “other visual indicators may be used to aid the establishment of [positive identification]” including “description of clothing” or “gait.” After a shot, according to the British document and case studies in the Pentagon’s ISR report, drones would hover to determine if their target had been hit, collecting video and evidence of whether the cellphone had been eliminated. (The British intelligence agency, GCHQ, declined to comment on the document.)
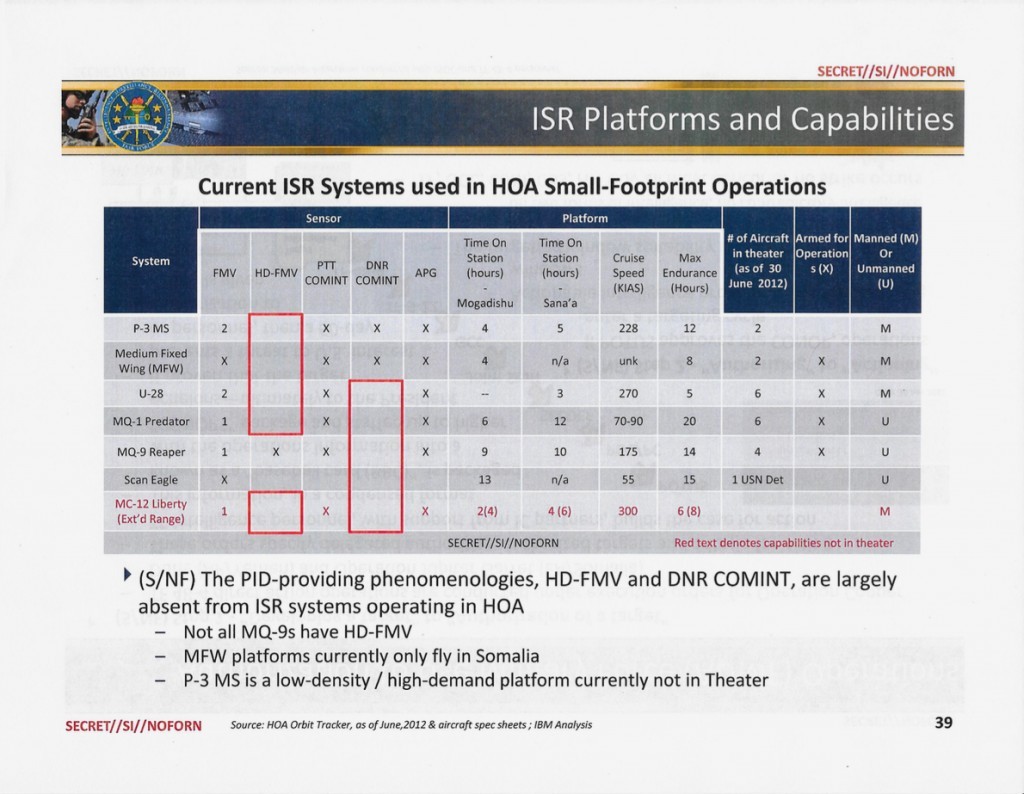
A chart comparing the surveillance capabilities of the various drones and aircraft flying over Yemen and Somalia in 2012.
APG = Aerial Precision Geolocation; DNR COMINT = Dial Network Recognition Communications Intelligence; ISR = Intelligence, Surveillance, and Reconnaissance; FMV = Full Motion Video; PTT COMINT = Push-to-Talk Communications Intelligence.
Yet according to the ISR study, the military faced “critical shortfalls of capabilities” in the technologies enabling that kind of precise surveillance and post-strike assessment. At the time of the study, only some of the Reaper drones had high-definition video, and most of the aircraft over the region lacked the ability to collect “dial number recognition” data.
The study cites these shortcomings as an explanation for the low rate of successful strikes against the targets on the military’s kill list in Yemen and Somalia, especially in comparison with Iraq and Afghanistan. It presents the failings primarily as an issue of efficiency, with little mention of the possible consequence of bad intelligence leading to killing the wrong people.
______________________________
Additional reporting: Jeremy Scahill
Contact the authors:
Cora Currier – cora.currier@theintercept.com
Peter Maass – peter.maass@theintercept.com
Go to Original – theintercept.com
DISCLAIMER: The statements, views and opinions expressed in pieces republished here are solely those of the authors and do not necessarily represent those of TMS. In accordance with title 17 U.S.C. section 107, this material is distributed without profit to those who have expressed a prior interest in receiving the included information for research and educational purposes. TMS has no affiliation whatsoever with the originator of this article nor is TMS endorsed or sponsored by the originator. “GO TO ORIGINAL” links are provided as a convenience to our readers and allow for verification of authenticity. However, as originating pages are often updated by their originating host sites, the versions posted may not match the versions our readers view when clicking the “GO TO ORIGINAL” links. This site contains copyrighted material the use of which has not always been specifically authorized by the copyright owner. We are making such material available in our efforts to advance understanding of environmental, political, human rights, economic, democracy, scientific, and social justice issues, etc. We believe this constitutes a ‘fair use’ of any such copyrighted material as provided for in section 107 of the US Copyright Law. In accordance with Title 17 U.S.C. Section 107, the material on this site is distributed without profit to those who have expressed a prior interest in receiving the included information for research and educational purposes. For more information go to: http://www.law.cornell.edu/uscode/17/107.shtml. If you wish to use copyrighted material from this site for purposes of your own that go beyond ‘fair use’, you must obtain permission from the copyright owner.