Surveillance Techniques: How Your Data Becomes Our Data
WHISTLEBLOWING - SURVEILLANCE, 28 Dec 2015
Domestic Surveillance Directorate – TRANSCEND Media Service
In 2001, NSA published the secret “Transition 2001” report defining our strategy for the 21st century. No longer could we simply access analog communications using conventional means, the new digital world of globally-networked encrypted communications required a dramatic change to our surveillance strategy: NSA would need to “live on the network”.
We’ve turned our nation’s Internet and telecommunications companies into collection partners by installing filters in their facilities, serving them with secret court orders, building back doors into their software and acquiring keys to break their encryption.
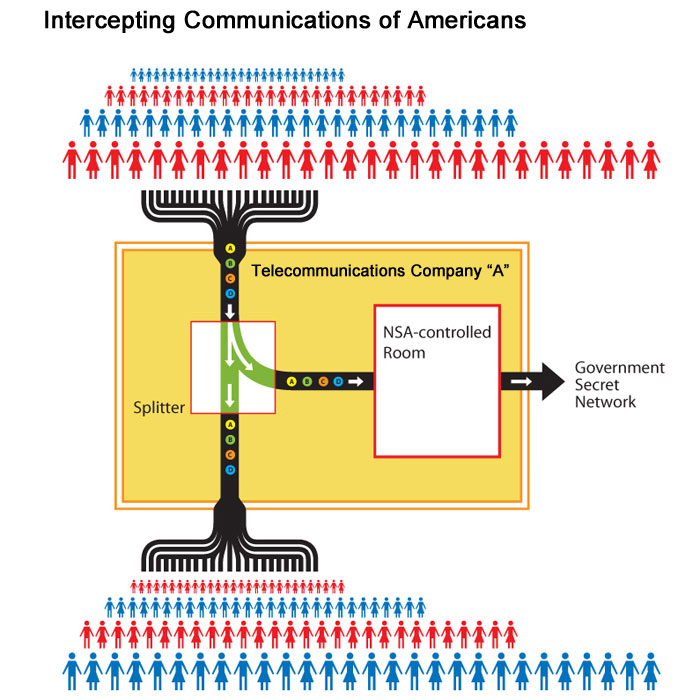
Our Domestic Intercept Stations
NSA technicians have installed intercept stations at key junction points, or switches, throughout the country. These switches are located in large windowless buildings owned by the major telecommunication companies and control the domestic internet traffic flow across the nation. A fiber optic splitter is placed on the incoming communication lines and routes the traffic to an NSA intercept station for processing.
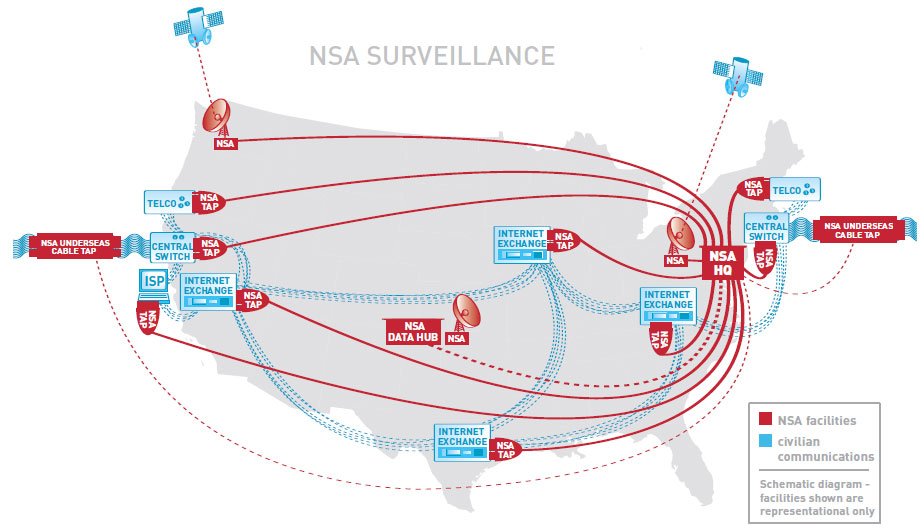
View a sample route that internet data traverses from a home in Toronto to the San Francisco Art Institute passing through several NSA intercept stations.
More information about this map
Bulk Collection of U.S. Citizens’ Phone Records
In the past, we used our close partnership with the FBI to collect bulk telephone records on an ongoing basis using a Top Secret order from the Foreign Intelligence Surveillance Court (FISA). The metadata we collected from this program gave us information about what communications you sent and received, who you talked to, where you were when you talked to them, the lengths of your conversations, and what kind of device you were using.
In mid-2015, Congress passed the USA Freedom Act sadly ending this valuable bulk collection program for the time being.
The PRISM Program: Our #1 Source of Raw Intelligence
DISCLAIMER: The statements, views and opinions expressed in pieces republished here are solely those of the authors and do not necessarily represent those of TMS. In accordance with title 17 U.S.C. section 107, this material is distributed without profit to those who have expressed a prior interest in receiving the included information for research and educational purposes. TMS has no affiliation whatsoever with the originator of this article nor is TMS endorsed or sponsored by the originator. “GO TO ORIGINAL” links are provided as a convenience to our readers and allow for verification of authenticity. However, as originating pages are often updated by their originating host sites, the versions posted may not match the versions our readers view when clicking the “GO TO ORIGINAL” links. This site contains copyrighted material the use of which has not always been specifically authorized by the copyright owner. We are making such material available in our efforts to advance understanding of environmental, political, human rights, economic, democracy, scientific, and social justice issues, etc. We believe this constitutes a ‘fair use’ of any such copyrighted material as provided for in section 107 of the US Copyright Law. In accordance with Title 17 U.S.C. Section 107, the material on this site is distributed without profit to those who have expressed a prior interest in receiving the included information for research and educational purposes. For more information go to: http://www.law.cornell.edu/uscode/17/107.shtml. If you wish to use copyrighted material from this site for purposes of your own that go beyond ‘fair use’, you must obtain permission from the copyright owner.
Read more
Click here to go to the current weekly digest or pick another article:
WHISTLEBLOWING - SURVEILLANCE:

 Larger version of map
Larger version of map