Becoming God! “Controlling Human Ontology:” Ambitions of the “Secret-State Confederation”
TRANSCEND MEMBERS, 13 Jan 2020
Anthony J. Marsella, Ph.D. – TRANSCEND Media Service
“Man is born free, but he is everywhere in chains.”
— Jean Jacques Rousseau (28 Jun 1712 – 2 July 1778), Social Contract, 1762
Introduction:
9 Jan 2020 – This paper is an elaboration of my 5 Aug 2019 publication in Transcend Media Service, Omnipresent Surveillance. The prior publication was written to increase awareness and to provoke citizen activism action.
In the interim, however, I came to better understand the ambitious goal of the secretive “Confederation” (i.e., National Security State Cabals) of individual, government, corporate, financial, military, and media empires and monopolies, was more sinister and perilous than omnipresent surveillance.
I use the word “Confederation” because I do believe no single group, no single nation, and no single concern is capable of controlling and dominating humanity, nations, and the world.
Defining characteristics of sinister “Confederation” of individuals, groups, and organizations include:
- Knowing one another with varying levels of attachment,
- mutual organization memberships (e.g., political parties, religions, military alliances, treaties),
- attending gatherings and meetings (e.g., Bilderberg, Davos, Bohemian Grove), and
- sharing common goals (e.g., wealth accumulation, central banking model, financial investments, suppression of protests or critiques).
Use of a “Confederation” identity is, in my opinion, a more realistic description than a single mass group (e.g., totalitarian state); a “Confederation” it is a collection or assemblage of varying ties and mutual obligations. Ultimately, some within the “Confederation” may emerge as the dominant groups because of military and financial power.
Under the facade of popularized “State” names (e.g., National Security State, Shadow State, Secret State, Emergency State, Totalitarian State), replete with their code-name programs and projects (e.g., Project Epsilon, Project Blue Bird, Project Ultra-Gard, Project Prism), the intentional “Confederation” engages in mass surveillance and permanent archiving of individual, organization, nation data (e.g., Utah Center).
This information is subjected to mass date-base analyses for nefarious purposes: While mass data can be used to inform and determine government, military, corporate decisions, the ultimate goal of the “Confederation” is to master, control, and own “human ontology,” to “Becoming God!”
As I came to grasp the goals and consequences of this malevolent “Confederation, visible “immediate” events and forces (i.e., wars, economy, regime changes, poverty, destructive global events), with their immobilizing fears, anxieties, and uncertainties, were used, tolerated, promoted as part of a greater ambitious pursuit of control and domination of human ontology.
Fear levels, propaganda, and xenophobic policies facilitated the imposition of authoritarian control and domination. Through powerful strategies, policies, and tactics, involving developments in technology (e.g., AI, 3-D Printing, Genetic-Code alteration), a future of dictatorial and despotic control and dominance was assured.
The ultimate goal and purpose of “Confederation” control and dominance of mind and behavior is to and shape “human ontology” (i.e., nature) according to their needs and visions. It is the absolute power for “Becoming God;” omnipotent, omnificent, and praxeology; all powerful, all knowing, all controlling of thought and behavior! With the assumed power of God, human ontologies can become controlled, including the pursuit of life and death. Eternity becomes a vision.
“Becoming God!” All other policies, plans, strategies, tactics, actions are consumed within this megalomaniacal goal. “Becoming God,” or “God Like” has been the intent of dictatorial national, religious, cult, corporate, financial, and military leaders, all infatuated with their power over life and death. Now a possibility as homogenized cultures and societies yield to their intent.
Hebrew Biblical assertions in Genesis 1:27, states: “So God created man in his own image, in the image of God created he him; male and female created he them.” (KJV). An inviting belief! A provocative belief! A belief sanctioning the idea of a “Chosen People,” endlessly seeking to discover GOD’s nature within and without. The Torah, a study in beginnings; the Talmud, to be studied and lived. These compilations affirm God’s (g—d) existence, and the possibility of recovery, discovery, and a new nature of existence.
“And GOD said: Let us make man in our image, after our likeness. And let them have dominion over the fish of the sea, and over the fowl of the air, and over the cattle, and over all the earth, and over every creeping thing that creepeth upon the earth.” KJV.
A powerful brew of thought, appealing and inspiring different minds, especially those whose wealth, power, and position enables them to pursue and actualize horizons beyond those normally accepted and followed. Why not discover the GOD? Why not assume GOD’s roles and functions? Why not “Become GOD?”
An ultimate belief, untethered by realities of its pursuit and consequence. Religions and philosophical systems have long been content with individual spiritual quests. Imagine if we go beyond to actual control of GOD’s functions. Have we not pursued this possibility with the endless “mind control” successes of National Secret State projects and programs? “It can be done!”
Now, amid the heady spell of technological developments, and the visions of “Becoming God,” via unlimited technology opportunities and choices, age-old interpretations of these and their implications, has seized the minds of some men and women. Life and death under your control! Why accept the “nineties,” with its feeble “mind/behavior” technologies, when we can live forever as “superhumans” with technology’s help? New forms of life and non-life! It is exhilarating! It is exalting! Imagine eternity!
Who wrote the biblical words requiring, compelling, demanding their acceptance? GOD, priest, rabbi, scribe, prophet. It was by human hand. The rest is history! First were sounds; grunts, growls, murmurs! Then repeated sounds assumed meanings! Then sounds became words! Then words ordered life. Then words were inscribed on a medium, moving beyond the moment. Then inscribed words became holy, as they appealed to minds resisting doubt! Then powers sanctioned inscribed words as the required rules of their position. Then came groups, tribes, societies, religions, governance, empires, civilizations . . . unfolding across a million years. Today powerful vestiges of the past remain: Gobekli Tempe, Stonehenge, Mounds, Temples, Pyramids. God, Gods, Priests, Wisemen, Emperors, Saints, Man/Woman.
This then, is the purpose of this paper. To discuss and illuminate the puzzle and its pieces via discussion of seemingly disparate topics, which, in fact, constitute and support a coming evolution to “Becoming God.” Wealth, power, position facilitate this possibility. It may be impossible to halt this course, unless the world is destroyed by nuclear war (GOD’S Hand), and mere survival comes to dominate behavior. If this occurs, humanity must make it clear no more concentrations of wealth, power, and position. Only a new ethic of mutuality. Even then, I wonder if escape is possible from the human imagination of playing with “eternity,” of “Becoming God,” and controlling human ontology.
Organization of Paper:
It is my intention to weave together a collection of topical concerns into a logical and coherent discussion of the challenge humanity faces as growing control and domination via mass surveillance and archiving increase to untenable and permanent levels. The “Confederation’s” goal: to control human ontology and to create new beings exceeding imagination. Death could be conquered for a few.
The paper is divided into the following sections:
- Introduction
- Authoritarian Control Domination Rule;
- Governance: An “Old” Policy and Practice;
- National Security Abuses (Technologies, Sources, Behavior Control);
- Government Agencies and Offices Involved;
- Sources of Totalitarian Secret State Emergence;
- How Did We Get to This Point?
- What Can Citizens Do?
- Ontology: Changes in Human Nature;
- Concluding Thoughts.
Patience with the length of paper; it is essential because of the complexity and gravity of concerns. Even so, length is still inadequate to the task. Voluminous scholarship, exceeding my age and time, is required. It is, however, a start!’
What emerges amid the fog, smog, haze, and daze of visible and disguised events and forces, in the USA and World, driven by concentrations of wealth, power, and position among “oligarchic” control, emerges omnipresent surveillance, monitoring, and archiving of massive databases is the sinister agenda: tyrannical and totalitarian motivated individuals, groups, and organizations, seeking total control of human ontology via concentrations of wealth, power, and position by a “Confederation” of recognized and unknown forces.
Unless dramatic changes occur, human ontology will accede to maniacal demands for creating and controlling human ontology including chimera, cyborgs, humanoids, hybrids, robots, synths via the processes of Cloning, AI, Nanotechnology, Stem Cells, 3-D Printing, and other emerging technology processes. Imagine human life controlled by a limited number of people with a common goal of “Becoming God.” It is happening, now, before our eyes.
II. Authoritarian Control, Dominate, Rule: Course of Human History
Fictional accounts of compelling dystopian societies, including, Brave New World, 1984, The Handmaiden’s Tale, Fahrenheit 451, The Matrix, and scores of apocalyptic movies, are proving prescient.
Once confined to popular reading, entertainment, and college seminars, fictional accounts of dystopian societies have assumed a frightening reality as government, military, corporate, and private sectors, impose oppressive surveillance strategies, methods, techniques, and tactics on citizens. These impositions are destroying the last semblances of legal and moral individual “privacy,” freedoms, civil rights, and USA Constitution First and Fourth Amendment rights, especially those guaranteed by the Bill of Rights.
Citizen fears for personal safety and security are encouraged and promoted media collaborators with governments, military, and corporate beneficiaries of violence and war; a pervasive sense of peril, danger, and jeopardy is normal. This sense of fear sanctions and authorizes authoritarian national security sectors imposing egregious abuses of citizen rights and privileges with oppressive and punitive measures.
Playing upon Western nation fears of being overrun by invasions, occupation, and exploitation by international migrants, especially from Islamic, Sub-Saharan African, and Central American nations, European citizens in many countries have elected right-wing populist governments determined to implement draconian immigration and refugee policies, limiting or blocking immigration to selective groups and conditions.
USA President Donald Trump announced all “illegal” resident immigrants will be expelled from the USA beginning June 24, 2019, under the auspices of the United States Immigration and Customs Enforcement (ICE) by the Department of Homeland Security. President Trump considers illegal immigrants are a threat to national security as sources of violence, crime, disease, and competing cultural traditions.
A convincing “xenophobia” has found its way into minds and hearts of citizens and officials resulting in the emergence of widespread “hate” cultures: “We hate broccoli, rival schools, politicians, cats, coyotes, foreign countries. We accept gun violence. Our nation is under attack by dangerous foes seeking our demise and collapse!” This is the thematic effort of those seeking power, control, and domination of citizen masses: it is appeal to fear and “heroic” nationalism, using media and digital propaganda.
Condemnation of the violations of citizen privacy and rights, once guaranteed in the Fourth Amendment of the USA Constitution, is drawing urgent attention from legal and NGO sources, but with little legal consequence.
Government, police, military, and corporate and private agencies are supporting numerous laws and regulations legitimizing pervasive surveillance, monitoring, and storage of citizen information for potential prosecution.
III. Governance: An “Old” Policy and Practice
“Experience has shown that even under the best forms of government, those entrusted with power have in time, and by slow operations, perverted it into tyranny.”
— Thomas Jefferson (1743-1826), Preamble to a Bill for the More General Diffusion of Knowledge, Fall 1778, Papers 2: 526-527.
Control, domination, and rule of citizen thought, behavior, and identity by authorities and ruling classes is the story of human history; it is the logical outcome when States, Nations, Empires, and Colonial rulers, especially dictatorships royalty, assume disproportionate power.
Protests and rebellions are quelled by a variety of oppressive measures, including arrests, imprisonment, torture, as well as murder, beatings and crowd control tactics. Assassinations and disappearance of rebel leaders is common, as desperate authorities oppress contention.
Never before in history, have the vast means of citizen control, domination, and rule been as total and complete as now exists because of the uses and abuses of technology. Romantic notions of citizen heroes leading uprisings against abusive and corrupt governments and authorities are the stuff of past myths.
Tragically, continued use of effective media and digital propaganda have resulted in citizen widespread concurrence and acceptance of oppression and violation of Constitutional rights and privileges. A paradox! “Yes, oppress and control me; I need your protection in a dangerous world.” (“Escape from Freedom. . . Fromm”)
Governance is needed! This reality cannot be contested! Contestations of abuses of power, however, as manifested in the expansive Government-Congressional-Corporate-Military-Educational-Media Complex, is required and essential.
As national elections approach, why are no candidates willing to risk the tolls of exposing the situation? Where are accusations and prosecution of encroaching and visible oppressions? Who is speaking about the national and global situation and promising to address the problem? Candidates and individuals in power have failed to speak against the challenge, even as awareness of its destructive implications outweighs many concerns for other issues.
A challenge for citizens is the harsh reality “society” often hides, distorts, and represses concerns for freedom. Openness, transparency, participation, are required in a democracy. Past presidential candidates have won on a platform of these admirable goals, only to find upon election, they succumb to shadow powers, and conform to traditional agendas using war and violence to achieve unwarranted goals. Who controls the leaders? Hidden governments? Be silent! If you do, you will have a library glorifying your life and office tenure!
In the USA, most citizens never imagined government would “betray” citizens given the protections of the USA Constitution. Today, however, surveys indicate less than 10% of USA citizens trust the government, and often see the government as biased in favor of special interests via lobbyists.
“National Security State,” “Secret State” and “Shadow State” groups of powerful and positioned individuals assumed power and control, betraying their oaths and loyalty in favor of personal agendas keeping them in power. Much of the “Secret State” individuals are ensconced in Justice Department offices and agencies (i.e., CIA, FBI, DHS, FISA Courts, NSA). Crimes and abuses of these groups continue to unfold daily revealing a tragic story of corruption, collusion, cronyism, conspiracy, complicity, and crime. Learn the “C” words, they control your life!
When societal institutions breakdown and collapse under pressures of corruption, cronyism, special interests, and inadequate funding, citizens are bereft of resources for protection and security. In an open and democratic society, transparency, social responsibility, and voting are keys to citizen awareness and empowerment. What happens, however, when these too are lost to political interests? Voter registrations are cut, gerrymandering occurs, voting machines are stacked and hacked, and propaganda thrives.
Tragically, many “secret state” societies around the world have already destroyed or denied citizen rights, enabling groups with special interests and concerns to exist, and to exact their toll in a coordinated manner – the “Confederation” lives. Under these circumstances, citizen wellbeing and welfare yield to special interests and the advancement of control in favor of mega-groups pursuing their own interests. Citizens are no longer players; when they attempt to act against control, they are promptly subdued as “Enemies of the State.”
Citizens look to government to protect them, but corrupt governments are too closely linked and connected to secret and known “power” groups, to offer citizen protection. In the process, citizens lose trust in governments and societal institutions; this raises the threshold for both protests and repression. A conundrum! What is at hand?
Within the context of institution collapse, and the rise of special interest and concerns, citizens become identified with certain groups at the cost of a society’s democratic identity and membership. They seek the comfort and security of identity with fringe elements offering simple solutions and ready identification of obvious enemies among minorities, immigrants, and radical revolution members. Heroes, calling for change, become victims, of their own protests and hopes.
IV. National Security Abuses and Excesses
“There is no greater tyranny than that which is perpetrated under the shield of the law and in the name of justice.”
— Baron de Montesquieu (1689-1755) The Spirit of Laws, 1748
This Section Provides:
- A reasonably comprehensive list of technologies used for gathering information on all There are certainly other top secret technologies in use;
- A list of information sought for monitoring and storage in government Fusion Centers and private vaults, including those of foreign nations;
- A list of behavior control and abuse methods related to technologies and information.
Materials and items in the three lists often overlap with one another. All materials and items are in the public domain.
- Technologies:
- Bill-Board Photography and Monitoring of Automobile Drivers
- Airport Body Scans (Gizmodo writes):
Within the next year or two, the U.S. Department of Homeland Security will instantly know everything about your body, clothes, and luggage with a new laser-based molecular scanner fired from 164 feet (50 meters) away. From traces of drugs or gun powder on your clothes to what you had for breakfast to the adrenaline level in your body—agents will be able to get any information they want without even touching you. And without you knowing it. (Gizmodo, July 10, 2012).
- Brain Wave (EEG) Readers
- Bugs (intrusive car, phone)
- Bugs (intrusive computer)
- Collaboration between massive corporations (e.g., Amazon, Face Book, Google) and government agencies (Algorithms for sharing information)
- Drones (Use to photograph, monitor house odors, disable equipment)
- Facial Recognition
- Finger Prints, Hand Prints, Footprints
- Genetic DNA sampling
- House-Air Sampling (Drones)
- Monitoring, copying, and retaining all phone, email, texting communications:
- Source number
- Target number
- Time of communication,
- Date of communication,
- Precise location of source and target numbers,
- Record conversation,
- Permanent archive data in Fusion Centers
- Neuroimaging Technologies (e.g., CAT, PET, EMR, SPECT, X-Ray)
Medical imaging information gathered via CAT scans, nuclear magnetic resonance, SPECT, and other methods reveal the distinct and unique pattern of electromagnetic radiation (EMR) from your various organs. Everyone has a distinct pattern, and knowing that pattern makes one vulnerable to specific controls using low radio wave frequencies and other invasive technology methods. This is especially a source for abuse using brain information.
- Radio-Frequency Identification Inserts (RFID)
- Satellite Monitoring
- Vision Data
Vision data is an example of control. Consider the simple and habitual act of going for a vision examination. As is well known, each person’s eyes have a unique and distinct display and can be sued for flawless identification. Vision identification is more accurate than fingerprints. Thus, when you stare into optometric equipment to determine both your visual equation and your eyes disease, a permanent record is photographed and maintained.
The ubiquitous camera at many traffic intersections has already recorded your face and upper body for security reasons. If you wear sunglasses, efforts will be made to affirm your visual identification.
- Sources of Information:
- Brain Wave (EEG) Readers
- Catholic Confessional (Bugging & Taping)
- Medical Information (EKG, Blood Tests)
- Face-Book Data
- Fake Photos and Videos
- False Accusations, requiring Court and Legal Responses
- Finger Print Data Base
- Foreign Nation Surveillance (e.g., USA, UK, China, Russia, Israel)
- Garbage Analysis
- Google, Amazon, Facebook Monitoring
- License Plates Readers on Streets and Highways
- Neighbor & Friends as Informants (Project Infra-Gard)
- Photographs
- Political Ideology Organization Surveillance (e.g., AIPAC, Anti-Defamation League, Southern Poverty Legal Fund, Anti-Boycott, White and/or Black, Latino, Islamic Extremists and Radical Groups)
- Private Investigators (Elude Laws. PI can be ruthless and relentless in acquiring data; bugging cars and phones, planting rumors, calling police)
- Project INFRA GARD, FBI, 1997, Cleveland, Ohio, (Recruitment of Stores, Malls, Professions, etc. to report on targets. This similar to the STASI policy in East Germany, in which everyone became a target and an informer. There was a justified national paranoia.
Project Infra-Guard expands FBI data-gathering system. Numerous sources of information regarding individuals or groups are now available to local, national and foreign security groups via:
(1) shopping expenditures,
(2) restaurant preferences and expenses,
(3) hair stylists & barber conversations,
(4) grocery purchases,
(5) gasoline purchases,
(6) automobile information,
(7) travel information,
(8) hotel records,
(9) publishers, and
(10) medical/mental health services. Yes, what you say to your physician and/or therapist is grist for the mill we have created.
- Pupillometry (Eye parameters)
- Radio Frequency Identification Device (RFID)
- Records Acquisition: HIPAA, Medical, School
- Records: Family history, pedigree, family tree mapping
- Smart and Interactive TV’s
- Smart Medicines (Track Use)
- Smart Meters (Utility Usage)
- Store Security Officials (While you shop, photos are taken, your preferred products identified, your shopping behavior; recall FBI Project Infra-Gard.
- Sting-Ray Computer EMAIL Monitor: (Obtains your email from a close distance. Illegal but uses by authorities, foreign nations, and suspicious neighbors)
- Subliminal Perception on TV and EMR messages (Can also be used for behavior control)
- Television Program Monitoring
- Use of consultants, collaborators, cooperatives, cronies, informants, plants, shils, and other forms of collusion to gather info, and to assess or create risk for investigation and persecution/prosecution (East German STASI).
- Use of Law (e.g., Section 215 of Patriot Act authorizes FBI to interview friends, family, professionals, and to swear all parties to silence)
- Video Records
- Window Vibration Decoding of Conversations
- Wire Taps (Proximal and Distal)
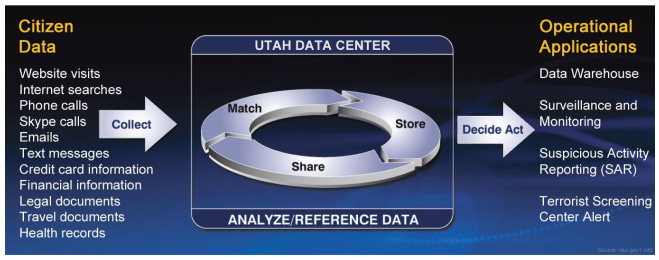
This image displays the functions of the massive UTAH DATA CENTER. As the image indicates, citizen data is gathered and saved in permanent storage. The storage capacity is in beyond our comprehension. Access: http://nsa.gov1.info.
- Behavior Control and Harassment Methods
- Annoyance Phone Calls
- Baiting (Monitoring open purses, money on floor, wheel-chair elderly, flirtations to facilitate arrest)
- Behavior Control (Manchurian Candidate)
- Control of Brain Waves
- Develop and Foster Hostility for Certain Groups (e.g., Target Muslims, African-American Protest Groups, Drug Cartels)
- Develop “Pseudo” Face Book, Twitter, and Other Social Network Members to Entrap Individuals or Groups
- Drugs: Depression, Mania, Confusion (LSD), Dulling, Stoned, Amnesia
- Defamation of Character
- Entrapments (Use of Authority Promises of Reduced Prosecution)
- FISA COURT Abuses. Designating critics of government or political candidates as warranting FISA COURT listing as terrorist, criminal, or spy.
- Harassment: Planting False Evidence to Facilitate Arrest
- Harassment, Abuse, Prosecution of Whistleblowers
- Hypnosis
- Identification Implants
- Infiltration of List Servs, Media Services, Groups
- Informants (Use of Prior Offense People to Entrap)
- Microwave Stun Gun (Proximate & Distance)
- Rumor Planting and Monitoring: Plant rumors with friends, neighbors
- Use of paid private investigators to stalk and harass individuals
- Use of citizens as research subjects (injections, drugs, sprays) without consent (hundreds of examples by government agencies)
- Use of Toxins (Spraying)
- Use of spoiled or toxic foods when shopping. Exchanging similar foods in shopping carts with toxic foods.
- Voice Recognition (Monitoring, samples and recreating offensive messages)
Data from mass-surveillance technology methods and techniques are distributed to DHS/NSA State Fusion Centers, and a Computer System named AQUAINT, standing for “Advanced Question Answering for Intelligence.”
V. What Government Agencies and Organizations Are Involved?
According to Wikipedia (2019):
The United States Intelligence Community (IC) is a federation of 17 separate United States government intelligence agencies, that work separately and together to conduct intelligence activities to support the foreign policy and national security of the United States.
Member organizations of the IC include intelligence agencies, military intelligence, and civilian intelligence and analysis offices within federal executive departments. The IC is overseen by the Office of the Director of National Intelligence (ODNI) making up the seventeen-member Intelligence Community, which itself is headed by the Director of National Intelligence (DNI), who reports to the President of the United States.[1][2]
The IC is headed by the Director of National Intelligence (DNI), whose statutory leadership is exercised through the Office of the Director of National Intelligence (ODNI). The other 16 members of the IC are:[9]
There are an extensive number of “Intelligence” gathering and utilization organizations, involving hundreds of thousands of employees and an unknown, but obviously considerable, amount of money.
All of this in the name of domestic and national security. There are numerous issues regarding duplication, competition, communication, hierarchies, strengths and weaknesses, costs, among these known groups. There is reason to believe there are also unknown groups which function independently.
There is irony and paradox here! The approved protectors and guardians impose constraints and abuses on citizens in the name of national security, however, in doing so, they impose control, domination, and rule constraints.
This is a bewildering anomaly, and one from which there may never be an escape given the secrecy and depth of penetration of governance and private surveillance groups. Can we really expect military intelligence to give up its roles, methods, and ties to weapons manufacturers like Lockheed Martin, Boeing, BAE Systems, Raytheon, Northrop Grumman, United Technologies, General Dynamics. Trillions are spent for the perpetuation of a war industry. Some, with no concern for the consequences, claim “employment” is the arbiter. It must be asked whether other “employment” options should be pursued as war industries become entrenched.
There are powerful connections among Silicon Valley corporations, military weapons manufacturers, and the Defense Department. They support one another in a “silent” conspiracy of financial relations and ties. Numerous retired military officials and officers go to work for Silicon Valley and weapon industry corporations as consultants and executives. The fix is on! Will this system harvest what it sows? Military capitalism lives.
The Government-Congressional-Corporate-Military-Educational-Media Complex lives, at least for now; too many people and agencies on the take, too few lack essential conscience! Too many are “Wolves of Wall Street,” waiting for opportunities to purse their interests. If a dollar is to be made, seize the moment. Worry about morality later. Money is the arbiter for life in military capitalism and neo-liberal capitalism.
VI. Foundations of the National Security State (Secret State, Shadow State)
“We do it to protect you!” “Or nation and the world,” they claim, “are in danger from those who seek our destruction.” Thus, we “must” use the full extent of our national powers and our available technologies to engage in universal surveillance, monitoring, and archiving of information.
It is ironic! To preserve national security, we must become the National Security State, and deprive you of all your rights and privileges. Doesn’t this make our nation a “terrorist state?” Our presidents and leaders’ “failures” gave impetus to the National Security State. The National Security State becomes part of a global “Confederation” of concentrated wealth, power, and position.
Sources of the rise, dominance, and control of the national security state can be identified. There are a number of sources, and it is important to consider them as reciprocal. The sources include:
Collaboration and Cooperation of Biased and Compromised Media, which is, arguably, the most important societal check and balance against the abuses, violations, and identification of government and private criminal actions;
Development of Vast Complex of “Escape” Clauses within our executive, judicial, and congressional systems permitting individuals to lie, distort, misrepresent, and speak with impunity without fear of prosecution. In brief, a privileged and oligarchic “group” is “free” to engage in illegal actions without accountability, transparency, or risk;
Economic Forces: Monopolies, Federal Reserve System, National Central Banks, Dollar Global Currency via Bank of International Settlements in Switzerland;
Military Arms Manufacturing and Military Capitalism (e.g. Lockheed Martin, Boeing, Raytheon, others);
Empowered Individuals: Presidents Harry Truman, Eisenhower, Bush(s), Barack Hussein Obama, Donald Trump; David Ben-Gurion, Benjamin Netanyahu; Great Britain, Vladimir Putin;
Global Challenges: Climate Change, Energy, Water, Population Growth, Criminal States, Unstable States, Migration, Refugees;
Hard Technologies: Computers, Nano-Technology, AI, DARPA Creations (e.g., HAARP), Sensors, Robotics, Drones, Military Weaponry, IPhone;
Institutional Creation: National Security Act-1947, Central Intelligence Agency, National Security Agency, Foreign Intelligence Services (e.g., GHQC, KGB, Mossad, Nakan);
Institutional Failures: Violation of Separation of Powers, Failed Democracy; Legal Enforcement: Patriot Act, Department of Homeland Security, Militarization of Police;
Lust for Power, Wealth, Position and the Domination and Control accompanying these impulses. Selfish motives from troubled minds.
Nation Conflict: USA-USSR, USA-China, USA-North Korea, Colonial Collapse, Israel-Palestine, India-Pakistan;
Oligarchy: Location and Control of Power within a small group of individuals (oligarchy) who by stained temperament, disposition, position, and financial interests seek to increase, sustain, and protect USA state terrorism policies, actions, and organizational structures;
Organized Projects/Programs: e.g., Project Prism, Project Echelon, Project Minerva, Project Artichoke, Project Bluebird;
Political Ideological Conflicts: Democracy-Communism, Democracy-Dictators, Rich-Poor, Colonial-Sovereign, Democracy-Hypocracy;
Political/Ideological Beliefs: Exceptionalism, White-Man’s Burden, Project for a New-American Century (PNAC), Militarism; Capitalism;
Soft Technologies: Game Theory, Computational Modeling, Algorithms, Behavior Control, Brain Mapping, Social Media;
Suppression and condemnation of protests, including harassment, persecution, and prosecution of those speaking out against the National Security State;
Technological developments (e.g., Big Data) permit mass surveillance, monitoring, and archiving of all information on citizens;
Use of Congressional Acts and Secret Agreements to justify and protect abuses including The Patriot Act, The Department of Homeland Security and Fusion Center authorizations, the Foreign Intelligence Surveillance Act (FISA), and Authorization to Use Military Force (AUMF);
World War II and Others: USA Domination, Cold-War Hysteria, Korea War, Vietnam War, Iraq War, Afghanistan War, Endless Wars.
Marc Slavo (2019), points out the nefarious security cooperatives among countries with mass surveillance systems. He writes:
Many countries have surveillance systems, but the countries in the Five Eyes, Nine Eyes, and 14 Eyes alliances, work together to share data on a massive scale, according to a report by Cloud Wards.
Innocent people are spied on every day. The Five Eyes, Nine Eyes, and 14 Eyes groups are big players in the global surveillance game. Each country involved can carry out surveillance in particular regions and share it with others in the alliance.
The Five Eyes are the U.S., UK, Canada, Australia, and New Zealand. The Five Eyes alliance, also known as FVEY, was founded on Aug. 14, 1941, and can be traced back to the WWII period. During the second world war, the exchange of intelligence information between the UK and the U.S. was important, and the partnership continued afterward.
The Nine Eyes alliance consists of the Five Eyes countries, plus Denmark, France, the Netherlands and Norway. Though there is evidence the Nine Eyes and 14 Eyes exist, little is known about what they can and can’t do.
The 14 Eyes alliance is made up of the Nine Eyes countries, plus Germany, Belgium, Italy, Spain and Sweden. It’s an extension of the Five Eyes and Nine Eyes alliances, but its actual name is SIGINT Seniors Europe. Cloud Wards
“Legal” authorizations serve to increase control, and to limit and restrain citizen rights and privileges needed to question and to protest.
A recent CIA sponsored Bill, Intelligence Authorization Act” (SB: 3153; HB 3194) garnering Congressional support would criminalize whistle blowers and reporters. Imagine, citizens are to be criminalized and punished for engaging in citizen expected responsibilities of complaint.
Daniel Schuman (July 25, 2019), policy director of DEMAND PROGRESS, writes:
“House Intelligence Committee Chair expansion of the Intelligence Identities Protection Act beyond all reason will effectively muzzle reporting on torture, mass surveillance, and other crimes against the American people — all at the request of the CIA.”
Dagny Taggart (2019), a pseudonym for a seasoned reporter fearful of retaliation, based on Pew Survey, results, writes:
“Americans Don’t Trust the Govt, the Media, or Each Other: Fading Trust is “Sign of Cultural Sickness and National Decline.”
Is this any wonder? Years of corruption, cronyism, and crime by government, private corporations, military, and other societal institutions make “trust” a foolish and unwarranted action. This is nothing new!
In the Seventeenth Century, Thomas Hobbes’ (1588-1678), proposed the idea of a Leviathan (1651), an oppressive master/monster over lives to quell brutalities of life imposed upon the people of the day. Hobbes described a world envisioned giving rise to the need for totalitarian control:
“Leviathan”
. . . there is no place for Industry, because the fruit thereof is uncertain: and consequently no Culture of the Earth, no Navigation, nor use of the commodities that may be imported by Sea; no commodius (commodious) Building; no Instruments of moving and removing such things as require force, no knowledge of the face of the Earth; no account of Time; no Arts; no Letters; no Society; and which is worst of all, continual feare, and danger of violent death; and the life of man, solitary, poore, nasty, brutish, and short (Thomas Hobbes, Leviathan, 1651).
VII: How Did We Come to This Point?
There are a number of classic sources for understanding how we came to this point of of abuse: Priest & Arkin, 2011; PBS Frontline Documentary: The United States of Secrets: Parts I and II); The Emergency State: America’s Pursuit of Absolute Security at All Costs” (David Unger, 2012; “The Short American Century: A Post Mortem” (Andrew Bacevich , 2012; The Power Elite ( CW Mills, 2000), The Watchers ( Shane Harris, 2010); Police State USA (Chumley, 2014; Battlefield America (John Whitehead, 2017). Scores of others deserve mention and response.
Answers to this question are complex, and involve historical, economic and sociopolitical, and moral explorations. Perhaps, however, there is something to be studied and known about the very individuals who developed and administered this mass surveillance and behavior control system.
In the end, these people had choices, and chose . . . Who are they? What are their names? Should photos be posted?
Volumes addressing this topic include Blue Bird: Deliberate Creation of Multiple Personalities (Colin Ross,2000); A Question of Torture: CIA Interrogation, From the Cold War to The War on Terror. (Alfred W. McCoy, 2006); A Nation Betrayed: Cold War Experiments Performed on Our Children and Other Innocent People (Carol Rutz, 2001); The Manchurian Candidate (Condon, R., 2003); Mind Control Information and Facts (Peers Want To Know).
Revelations of the national and international mass surveillance, monitoring, and archiving complex are overwhelming in implication and consequence. Claims of disbelief can no longer be dismissed. Events have been unfolding for decades even as USA citizens continue daily life activities, and honoring government leaders who betrayed the Constitution.
As the mass surveillance system becomes better known, what opinions will citizen have of their government, nation, morality.
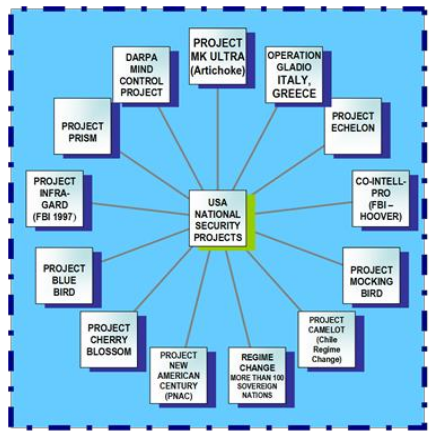
Figure 2 displays examples of the many government projects and programs designed under the auspices of national security. Each of these projects and programs have required and implemented constraints on citizen freedoms under the guise of security. Whose security?
In my opinion, McMaken (2019), provides a thorough summary of the rise of the National Security State and its connection to a “Confederation” seeking absolute control. What emerges is the tragic reality, both chance and choice, have shaped this “Leviathan.”
Family names (e.g., Rockefeller, Bush, Carnegie, Rothchild) re-appear again and again in discussions of those advocating a “new world order, as do institutions including the Pilgrim Society, Moses Institute, Vatican, Royalty, and corporations (e.g., Amazon, Google, Apple). The unraveling remains a complex and perhaps, dangerous, task. Billionaires exert power because of their wealth (e.g., Bezos, Gates, Zuckerberg, Buffet, Adelson, Icahn, Soros).
Figure 2: USA National Security Projects and Programs
VIII. What Can Citizens Do?
There have been many suggestions regarding a needed response to the growing totalitarian national security state of the United States. Responses have come from around the world, and many names are now familiar (e.g., Noam Chomsky, Mairead McGuire, Amy Goodman, Johan Galtung, Richard Falk, John Whitehead, Chris Hedges). Protests will arise and be oppressed, participants will be brutalized, imprisoned, and subjected to torture; there are, however, other options for building a more enduring and effective response:
Informed: Become informed and educated about the scope and sources of the national security state threats to privacy and behavior control. This can only be done by reading credible sources, reading beyond popular media, and questioning sources with specific hidden agendas (i.e., corporate, military).
This will require learning across different sectors and disciplines. A single profession or discipline is inadequate to understand the complexities of our challenges.
Multisectoral, multidisciplinary, multicultural, multinational learning is required. Multiplicity is essential! We must move beyond confines of disciplines, sectors, and nations.
Activism: Become as active as your circumstances permit in peaceful protests that may include opinion writing, letter writing, petition signing, phone calls to elected representatives, and joining discussion groups via the internet or in real time. Become as active as your circumstances permit with regards to supporting alternative information sources (e.g., Transcend Medial Service, Truthout, Guardian), and with supporting pathways to prosecution for those violating Constitutional and civil rights.
Non-Violence: Become committed to non-violence and nonkilling, as viable pathways for bringing about change. This may well make change a slow and arduous process, and it may never be completely successful. Yet, the course of violence, insurgency, and revolt can only lead to destruction and death, as we are witnessing in the United States and around the world.
Table 1 offers a summary of some of the steps and processes required if the National Security State and its connection to the “Confederation” are to be neutralized and eliminated in favor of a citizen-based democracy and peace culture. While many changes are needed, Table 2 lists possibilities. A more complete list is available in Marsella (2013).
Table 1: Brief List of Actions for Neutralizing “Confederation” of National Security State Power and Control
- Build museums, monuments, holidays, and tributes to peace. Stop glorification of war;
- Call a Constitutional Convention to address and correct abuses and offenses;
- Choose and support non-violence and nonkilling beliefs and actions across varying religions and life philosophies;
- Circulate UDHR (Universal Declaration of Human Rights) to all schools and governments as an accepted and legal guide;
- Condemn and prosecute apartheid in USA and across the world. Fences eliminate possibilities for cooperation and interaction;
- Develop alternatives to Military Capitalism as a dominate economy for expenditures and employment;
- Develop Department of Peace as a standing cabinet office, separate from Departments of State or Defense.
- Development Peace Universities and Peace as an academic major;
- End “Citizen United” as a source of corporate election influence, control, and dominance;
- Forgive international loans and student loans;
- Limit monopolies: e.g., Big Ag, Big Pharm, Big Health, Big Transportation, Big Education, Big Military, etc. Monopolies concentrate power and control;
- Limit Presidential terms of office to six years, and Congressional terms of office to eight years. End the seniority system of power which enables congressional members to remain powerful for years;
- Prosecute members of Government offices (Justice, CIA, FBI) who have engaged in criminal betrayal of Constitution;
- Reform FISA Court Act (Foreign Intelligence Surveillance Act);
- Restore balance of power across executive, congressional, and justice sectors;
- Restrict Central Banking Model of financial control over nations’ debt;
- Support the USA Peace Memorial Foundation;
- Teach Peace Across the Curriculum in schools and colleges;
- Understand pressing global challenges as reciprocal, rather than independent and isolated. For example, Climate Change is a function and determinant of other natural and Anthropogenic problems
- Vote and Fight Voter Fraud
IX. Ontology: Changes in Human Nature
In the face of massive socio-political, economic, and moral issues, there remains a pressing challenge regarding advances in technology which promise to alter current view of human ontology.
Ontology’s “truths” can never be static because of human evolution. As time passes, and ions separate millennia, era’s, centuries, and the present, the lessons of history become obvious. Truths of one time period or “era” become recognized by limitations in knowledge present in theological systems, political systems, and socio-cultural systems. It is a time of liberation from existing views, and expansion of what we know and how we know.
Human ontology has always been a varied view, as efforts to explore and seal human-animal possibilities. Today, there is a new reality based on technology and in the control of National Security State forces.
Humanity needs to grasp dramatic and profound accommodation and compromise to new forms of existence, human nature (ontology), and life will be required. There will be a conflict between developing uniformity/homogenization in cultures and societies, asserting diversity/variation (Marsella, 2014).
Ontological models related to free-choice, spirituality, and religious/theological models, especially regarding to the nature of morality are being challenged by developments in information processing, artificial intelligence, genetics, subatomic quantum, and astrophysical/cosmic models.
There will be fundamental challenges to views of human ontology. Of special note is technological survival of the fittest may be confined to those possessing the wealth, power, and position to exploit and to utilize resources for personal privilege and control (e.g., bio-technologies involving mass population cloning, use of bio-mechanical parts, storage of embryos and gametes, and inter-planetary colonization) (Marsella, 2016).
Ontology Implications: Emerging Mechanisms and Procedures for Technological Changes
- Artificial intelligence (AI);
- Analytics (information processing methods and procedures capable of informing the state or status of an object, including humans, even as great distances);
- Algorithms (Ordered chain of decision processes to resolve a problem);
- Brain-Internet Interface Implanted;
- Commercial Patents (Knowledge restrictions and protections);
- Mass Data Bases;
- Mathematical Procedures (Predictive models, computational models, sorting and classifying algorithms, exploring);
- New Materials and Substance Creations;
- Nanotechnology (Existing capacity within ICT industries to reduce the size of information-communication technologies to miniscule sizes; this permits building of complex systems. A nano is 10 -9 in size. Nano-technologies enable development of complex systems simultaneously capable of processing and holding vast amounts of content);
- Robotic Humanoids: (How about spare organs?);
- Sensors (Materials capable of informing the status or state of an object, and thus enabling feedback to a control system);
- Reconstructive Surgeries;
- Storage: Enormous storage capacities for information and data (units of terabytes, yotabytes, endlessbytes, or larger, not mega or gigabytes). It all started with a “bit” (0.1);
- Three-D Printing.
Mary Shelley’s classic 19th century book, Frankenstein, loomed as a prophetic recognition of the unlimited possibilities of humans crossing known thresholds in the creation of alternative human forms and processes. Mary Shelley, like many others, saw the unfolding of industries and technologies, along with a human impulse to push the limits of imagination and creation. What could be imagined (e.g., flying), could be pursued with unknown and untold consequences! A new day is upon us! The issue is who will control these powerful technologies?
X. Concluding Thoughts
Attention! We are living in a dysfunctional surveillance state, akin to those written in fictional novels and shown in science fiction movies. Do not dismiss this harsh reality! There is no privacy! Mass surveillance technologies, including satellite spy systems linked to ground surveillance systems, gather, monitor, and archive data on every person and organization. As the System is proud to claim: “We know more about you, than you know about yourself.”
While this mass surveillance reality may be accepted passively, amid a felt sense of helplessness to contest this “Leviathan,” its acceptance compels recognition of evolutionary changes in epistemology, ontology, and praxeology. Past comforts and conveniences from religions and political belief systems are deceptions, serving to calm fearful minds.
Advent of Artificial Intelligence (AI) technologies resulting in major changes in robotics, forewarns human life is not sacred. Robots, capable of assuming many human tasks and responsibilities without protests, complaints, or risks, will replace humans. Perhaps new species of human-robot interfaces will emerge amid the massive data bases, permitting specific human beings to be duplicated and interfaced with robotic qualities and potential.
New ontologies of human nature are upon us. There never was a single human ontology, but rather a spectrum of ontologies defined by culture, place, and situation. Biblical notions of God making man in his image failed to grasp God’s image as “nature,” now capable of creating evolutionary species connecting humanity with AI technological capabilities and potential.
The human and life form cycle of “survival, adaptation, adjustment, becoming, and evolving,” is present, and always has been occurring, blind to human understanding and aspirations. Certainly, amidst decline and destruction of planet Earth by connections across (1) climate change, (2) air-land-ocean pollution, (3) noise-vision-taste pollution, (4) poverty-malnutrition-toxicity, (5) violence-aggression-war, (6) greed-inequality-capitalism, and (7) nuclear-plastics-garbage waste, a new milieu has developed, prompting “elite” to consider “Becoming God.”
A Personal Note . . .
I love the United States of America. My country has offered me, and hundreds of millions of others, opportunities that could not be imagined or considered in any other nation. It is because I love the United States of America, however, and because I am grateful for its Constitution and its history of righting wrongs, and challenging injustices, I have been compelled to write this commentary.
While some may disagree with what I have said, and the passion with which I write, they must not silence the voices of those who seek to promote our heritage and our rights by questioning the abuses occurring. A common method used to dismiss a commentary is by using the term “conspiratorial.” Yet another is by asking the commentator to defend each of their comments. So be it! We are required as citizens to question, to inquire, to analyze, and to reach conclusions
If the United States of America is a democracy, (and it is not a “working democracy,” as former President Jimmy Carter and scores of others note), then the broad spectrum of projects that constitute the history and context of the National Security State abuses need to be identified, and to be reported to the citizenry for public action. Some policies and actions may well be accepted, but they should never be hidden, especially when their acronymic-named projects define our identity as a nation, people, as an ideal and aspiration for the people of the world.
Omnipresent surveillance, monitoring, and archiving represent an anticipatory policy, tactic, strategy for human evolutionary decline as villainous minds, driven by wealth, power, and position seek total control and domination; their goal: “Becoming God!”
Life forms at all levels are at risk!
***
Selected References:
Bacevich, A. (2012). The short American century: A post-mortem. Cambridge, MA: Harvard University Press.
Chumley, C. (2014). Police State USA: How Orwell’s nightmare is becoming our reality. NY: WND.
Condon, R. (2003). The Manchurian Candidate NY: Jove Books, 1959/2003
Ceneys-Tunney, A. (July 12, 2012) Rousseau shows us there is a way to break the chains from within. The Guardian, London, UK.
Harris, S. (2010). The watchers: The rise of America’s surveillance state. NY: Penguin Group.
Hedges, C. (2015). A Nation of Snitches – Nation of Change.
http://www.nation of chan.org/2015/11/-nation-of-snitches/mass privat (July 25, 2019) https://www.activistpost.com/2019/07/the-cias-intelligence-authorization-act- would-criminalize-whistleblowers-and-reporters.html
Hedges, C., & Sacco, J. (2012). Days of destruction, days of revolt. NY: Nation Books
Marsella, A.J. (2014) The Epic Ideological Struggle of our time: Multiculturalism versus Homogenization. https://www.transcend.org/the-epic-ideological-struggle-of-our-global- era- multiculturalism-versus-homogenization/
Marsella, A.J. (2016). Relinquishing human identity: Unfolding evolutionary changes via bio-metric technologies. Pp. 23-33. Gatherings: A collection of writing genre. Alpharetta, Georgia: Mountain Arbor Press (ISBN: 978-1-63183-023-5)
McCoy, A. (2006). A Question of Torture: CIA Interrogation: From the Cold War to the War on Terror. NY: Metropolitan Books/Holt.
McMaken, R. (2019) The Deep State: The Headless Fourth Branch of Government. http://www.lewrockwell.com/the-deep-state-the-headless-fourth- branch-of-government/
Mills, C. W. (2000). The Power Elite. NY: Oxford University Press
Priest, D., & Arkin, W. (2011). Top secret America: The rise of the new American Security State. NY: Little Brown.
Ross, Colin (2000). Blue Bird: Deliberate creation of multiple personalities. NY: Manitou Publications.
Rutz, C. (2001). A Nation Betrayed: Cold War Experiments Performed on Our Children and Other Innocent People. NY: Fidelity Publishing
Silver, T. (2015). Lifting the veil: An Investigative History of the United States Pathocracy. NY: Want to know.info
Slavo, M. (July 31, 2019). Satellites Have Already Started Watching Your Every Movement. file://C:/Users/Tony/Desktop/Satellites%20Have%20Already%20St arted%20Watching%20Your%20Every%20Movement.html
Taggart, D. (2019). Americans Don’t Trust the Govt, the Media, or Each Other: Fading Trust is “Sign of Cultural Sickness and National Decline. ” file:///C:/Users/Tony/Desktop/Americans%20Don%E2%80%99t% 20Trust%20the%20Govt,%20the%20Media,%20or%20Each%20Oth er%20Fading%20Trust%20is%20%E2%80%9CSign%20of%20Cultu ral%20Sickness%20and%20National%20Decline%E2%80%9D.html
Unger, D. (2012). The emergency state: America’s pursuit of absolute security at all costs. NY: Penguin Press.
Want to Know.info (website) Mind Control Information and Facts.
Peers. 1607 Francisco Street. Berkeley, California. 94703
***
Endnote 1:
The term “omnipresent surveillance” is taken from John W. Whitehead’s recent article, “The Omnipresent Surveillance State: Orwell’s 1984 is No Longer Fiction.” Information Clearing House. June 11, 2019. See also Rutherford Institute, Virginia, USA
__________________________________________
 Anthony J. Marsella, Ph.D., a member of the TRANSCEND Network for Peace Development Environment, is a past president of Psychologists for Social Responsibility, Emeritus Professor of psychology at the University of Hawaii’s Manoa Campus in Honolulu, Hawaii, and past director of the World Health Organization Psychiatric Research Center in Honolulu. He is known internationally as a pioneer figure in the study of culture and psychopathology who challenged the ethnocentrism and racial biases of many assumptions, theories, and practices in psychology and psychiatry. In more recent years, he has been writing and lecturing on peace and social justice. He has published 21 books and more than 300 articles, tech reports, and popular commentaries. His TMS articles may be accessed HERE and he can be reached at marsella@hawaii.edu.
Anthony J. Marsella, Ph.D., a member of the TRANSCEND Network for Peace Development Environment, is a past president of Psychologists for Social Responsibility, Emeritus Professor of psychology at the University of Hawaii’s Manoa Campus in Honolulu, Hawaii, and past director of the World Health Organization Psychiatric Research Center in Honolulu. He is known internationally as a pioneer figure in the study of culture and psychopathology who challenged the ethnocentrism and racial biases of many assumptions, theories, and practices in psychology and psychiatry. In more recent years, he has been writing and lecturing on peace and social justice. He has published 21 books and more than 300 articles, tech reports, and popular commentaries. His TMS articles may be accessed HERE and he can be reached at marsella@hawaii.edu.
Tags: Conspiracy Theories, World
This article originally appeared on Transcend Media Service (TMS) on 13 Jan 2020.
Anticopyright: Editorials and articles originated on TMS may be freely reprinted, disseminated, translated and used as background material, provided an acknowledgement and link to the source, TMS: Becoming God! “Controlling Human Ontology:” Ambitions of the “Secret-State Confederation”, is included. Thank you.
If you enjoyed this article, please donate to TMS to join the growing list of TMS Supporters.

This work is licensed under a CC BY-NC 4.0 License.