Peace and War 2025: The Hot Chips and Cold Wars (Part 1)
TRANSCEND MEMBERS, 2 Jun 2025
Prof Hoosen Vawda – TRANSCEND Media Service
Please note that this publication is rated for general readership. Parental guidance is recommended for minors, who might wish to use this paper as a resource material.
*****************
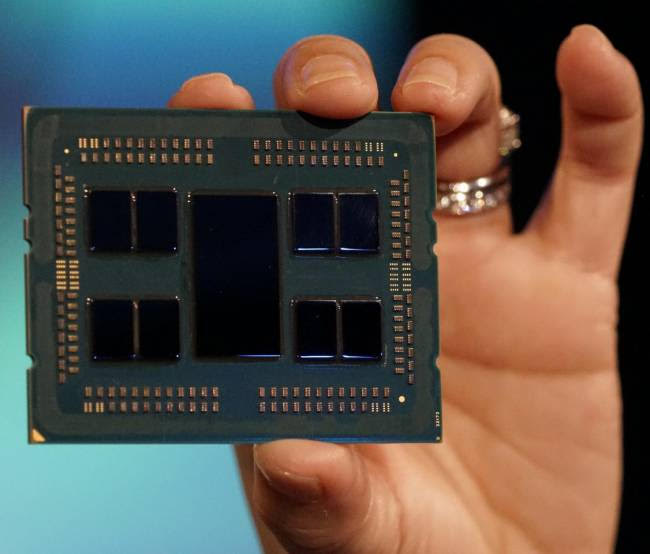
The Chip Is Gold, the Chip Is Power, the Chip Is the Future, and the Chip Is Nonedible: Who Has the Best Chip Controls the Universe [1]
Introduction
This publication, Part 1 in a two part series, examines and details the origins, precursor, types and uses of the semiconductor, commonly known as the computer chip..
Definition of a Chip
In the real world, there are two types of chips: Edible Chips, as a food item acquired from a fast-food outlet and Non-Edible Chips[2]
Definition of Non-edible CHIPS
Non-edible CHIPS refer to items that are not suitable or safe for consumption as food. These can be due to several factors, such as being toxic, harmful, or simply not designed to be consumed as food. The term “non-edible” is often used in contexts to describe objects, materials, or substances that should not be consumed by humans or animals. In the 21st Century, these electronic creations are called semiconductors.[3]
Origins and Precursors
The origins of non-edible CHIPS can be traced back to various historical developments in technology and materials. For example, the abacus, invented in the Middle East around 500 BC, was one of the earliest calculating devices. This simple calculator made from beads and wires laid the groundwork for the development of more complex machines. Over time, mechanical calculators like the Pascaline[4] and the Analytical Engine [5]were developed, eventually evolving and leading to the creation of modern computers the heart of which are chips of various types, performance and capacity to process information rapidly.
Relationship with Abacus
The abacus is indeed related to present-day CHIPS in the sense that it represents one of the earliest forms of calculating devices. The principle of making repeated calculations more quickly than the human brain is the same in both the abacus and modern computers. The abacus laid the foundation for the development of more advanced calculating machines, which eventually led to the creation of silicon chips used in today’s computers.
Definition of Computer Chip[6]
A computer chip, also known as an integrated circuit, is a small wafer of semiconductor material embedded with integrated circuitry. These chips comprise the processing and memory units of modern digital computers.
Composition and Function
Technically speaking, a computer chip is a piece of silicon with an electronic circuit embedded in it. It contains millions of microscopic electronic components called transistors that transmit data signals. These transistors are responsible for the chip’s ability to process and store information.
Significance in Modern Technology
Computer chips are essential components in modern technology. They are used in various devices, including computers, smartphones, and other electronic gadgets. The development of computer chips has significantly advanced the capabilities of electronic devices, making them more powerful and efficient.
Definition of Semiconductor
A semiconductor is a material with electrical conductivity between that of a conductor and an insulator. Its conductivity can be modified by adding impurities, a process known as doping. Semiconductors are essential in the manufacture of various electronic devices, including diodes, transistors, and integrated circuits
Definition of Full Conductor[7]
A full conductor, or simply a conductor, is a material that allows the flow of electrical current with minimal resistance. Conductors have high electrical conductivity, typically from 104104 to 106106 siemens per centimeter. Common examples of conductors include metals like copper and aluminum
Comparison between Semiconductor and Full Conductor
- Conductivity: Semiconductors have intermediate conductivity, while conductors have high conductivity.
Modification: The conductivity of semiconductors can be modified through doping, whereas the conductivity of conductors is generally fixed.
- Applications: Semiconductors are used in electronic devices for amplification, switching, and energy conversion. Conductors are used to transmit electrical power and signals.
Inventors of Computer Chips[8]
The invention of computer chips, also known as integrated circuits, is credited to two key individuals: Jack Kilby and Robert Noyce. In 1958, Jack Kilby of Texas Instruments created the first hybrid integrated circuit and received a U.S. patent for miniaturized electronic circuits in 1959. Around the same time, Robert Noyce of Fairchild Semiconductor developed the first monolithic integrated circuit, which used silicon-based technology.
First Prototypes
his initial prototype at Texas Instruments, while Robert Noyce’s work was conducted at Fairchild Semiconduct. These early prototypes laid the foundation for the modern computer chips we use today.
What is the most powerful computer chip today?
The world of computer chips is constantly evolving, with new advancements being made every year. As of 2025, the most powerful computer chip is the AMD EPYC 9965 ‘Turin’ processor”. It is a 192-core processor running on AMD’s Zen 5c architecture.
Key Features and Performance
- Core Count: 192 cores
- Base Clock Speed: 2.25 GHz
- Maximum Boost Clock Speed: Up to 3.7 GHz
- Architecture: Zen 5c
- Performance: It is designed to more than double the performance of the fifth-generation Intel Xeon Scalable CPU, the 64-core Platinum 8592+
The AMD Turin[9] stands out as the most powerful computer chip in 2025, offering unparalleled performance for data centers, AI workloads, and computational fluid dynamics. The term ” powerful computer chip” can be defined using various criteria, depending on the specific use case and performance metrics. Here are some of the key criteria used to determine the most powerful computer chip:
Performance Metrics
- Core Count: The number of cores in a chip is a significant factor. More cores generally mean better multitasking and parallel processing capabilities.
- Clock Speed: The base and boost clock speeds of a chip determine how fast it can process instructions. Higher clock speeds usually result in better performance.
- Transistor Count: The number of transistors on a chip can indicate its complexity and potential performance. More transistors typically mean more processing power.
- Thermal Design Power (TDP): This measures the amount of heat a chip generates and needs to dissipate. Lower TDP values are preferable for energy efficiency.
Benchmarks
- Single-Threaded Performance: Benchmarks like Cinebench and Geekbench measure the performance of a single core. High single-threaded performance is crucial for tasks that rely on single-core efficiency
- Multi-Threaded Performance: Benchmarks that test multi-core performance, such as those used in productivity applications and rendering tasks, are essential for evaluating a chip’s ability to handle parallel workloads
- Integrated Graphics Performance: For chips with integrated GPUs, benchmarks that measure gaming and graphical performance are also considered
Use Cases: Peace and War
- Gaming: For gaming, chips with high single-threaded performance and strong integrated graphics are often considered the most powerful
- Workstations: For professional workstations, multi-threaded performance and high core counts are crucial for tasks like video editing, 3D rendering, and scientific simulations
- Servers: In server environments, energy efficiency, thermal performance, and multi-core capabilities are critical for handling large-scale data processing and cloud computing
These criteria collectively help define the most powerful computer chip, depending on the specific requirements and applications.
Computer Chips and links to Trade War[10]
Computer chips (semiconductors) are at the heart of modern trade wars due to their strategic importance in technology, military systems, and economic competitiveness. Here’s how they intersect with trade conflicts, illustrated with real-world examples:
- Chips as a Geopolitical Weapon
Why?
- Semiconductors power everything from smartphones to AI and missiles. Controlling their supply chain grants economic and military leverage.
- The U.S. and China are locked in a “Chip War” to dominate design, manufacturing, and access to advanced chips.
Example: U.S. vs. China Export Controls
- In 2025, the U.S. imposed 145% tariffs on Chinese chips and banned exports of advanced AI chips (e.g., Nvidia’s H100) to cripple China’s tech/military growth 36.
- China retaliated by restricting exports of gallium and germanium (critical for chipmaking), hurting U.S. defense contractors.
Outcome: A global scramble to secure chip supplies, with companies like TSMC building plants in the U.S. to avoid tariffs.
- Tariffs Disrupting Supply Chains
Why?
- Chips rely on a global supply chain: Designed in the U.S. (Nvidia)[11], made in Taiwan (TSMC[12], [13]), assembled in China, and used globally. Tariffs disrupt this flow.
Example: Gaming Consoles Hit by Tariffs
- In 2025, U.S. tariffs on Chinese-made electronics (e.g., PlayStation 5, Nintendo Switch) raised console prices by 30–40%
- Sony and Nintendo shifted production to Vietnam, but new U.S. tariffs (up to 46% on Vietnam) nullified the cost savings
Outcome: Higher consumer prices and supply chain chaos, with companies stockpiling chips preemptively 14.
- Subsidies and “Chip Nationalism”
Why?
- Countries are spending billions to onshore chip production, fearing over-reliance on rivals.
Examples:
- U.S. CHIPS Act: 52.7billiontoboostdomesticchipmaking,counteredbyChina’s52.7billiontoboostdomesticchipmaking,counteredbyChina’s150 billion subsidy for SMIC[14] (its top chipmaker).
- EU Chips Act: €43 billion to reduce dependence on U.S./Asian chips.
Outcome: A subsidies arms race, with TSMC (Taiwan) caught in the crossfire as it builds plants in the U.S., Japan, and Germany
- Tech Decoupling and “Silicon Blockades”
Why?
- The U.S. aims to cut China off from advanced chips (e.g., for AI/supercomputers), while China pushes self-sufficiency.
Example: Huawei’s Survival Tactics[15]
- After U.S. sanctions, Huawei developed its 7nm chips (via SMIC) despite export bans, using older tech to bypass restrictions.
- China now produces 60% of global surveillance chips (e.g., HiSilicon), reducing reliance on U.S. firms like Intel.
Outcome: A fragmented tech ecosystem, with Chinese chips powering domestic products but lagging in cutting-edge innovation .
- Secondary Effects: Shortages and Inflation
Why?
- Trade wars create bottlenecks. In 2025, chip lead times hit 4+ months, and prices rose 18% due to tariffs and hoarding.
Example: Auto Industry Crisis
- U.S. tariffs on Chinese/Mexican auto parts (25%) disrupted car production, echoing the 2021 chip shortage.
- Ford and GM warned of $1,000+ price hikes per vehicle.
Outcome: Higher costs for consumers and stalled tech adoption (e.g., AI, EVs).
Key Takeaways
- Chips = Power: Control over semiconductors translates to economic/military dominance.
- Tariffs Reshape Supply Chains: Companies flee China but face new trade barriers (e.g., Vietnam tariffs).
- Subsidies Fuel Rivalry: The U.S., EU, and China are spending trillions to “win” the chip war.
- Tech Decoupling is Accelerating: Separate U.S. and Chinese tech ecosystems are emerging.
For additional reference please see: CEPA on the “Chips War” [16] Deloitte’s 2025 Semiconductor Outlook [17]
Final Thought: The chip trade war is a high-stakes game of “musical chairs”,nations and firms are scrambling to secure their place before the music stops.
Classification of ABACUS [18]
The abacus is not classified as a computer chip. While both the abacus and computer chips are used for calculations, they are fundamentally different in their design and function. The abacus is a manual calculating tool made from beads and wires, used for performing arithmetic operations. On the other hand, a computer chip is an electronic device that processes and stores data using integrated circuits and transistors.
First Record of ABACUS
The earliest record of the abacus dates back to ancient Babylon around 300 BC It was initially a board or slab on which a Babylonian spread sand to trace letters for general writing purposes. Over time, it evolved into a board marked with lines and equipped with counters for numerical values
Discovery of ABACUS
The exact individual who discovered the abacus is not known. However, it is believed to have originated in Babylon and was later used in various ancient civilizations, including Egypt, Greece, and Rome. Greek historian Herodotus mentioned the use of the abacus in Ancient Egypt
History of computers – from the Abacus to the iPhone – Is Abacus a Computer?[19]
Introduction
The word “abacus” has a rich history and its etymology can be traced back to ancient languages.
Etymology
The term “abacus” dates back to at least 1387 AD when it was borrowed into Middle English from Latin. The Latin word “abacus” itself is derived from the ancient Greek word “ἄβαξ” (abax), which means “counting table” or “board for drawing” The Greek term “abax” is believed to have originated from a Semitic source, such as the Phoenician or Hebrew word “abaq,” which means “dust” This is because the earliest abacuses were boards covered with dust or sand on which mathematical equations or calculations could be traced and erased
Summary
The word “abacus” has evolved over centuries, originating from ancient Greek and Semitic languages, and has been used to describe a counting tool that has been essential in various cultures for performing arithmetic operations.
Use Cases: War and “Kill Chips”
Can National Producers Embed “Kill Chips” to Sabotage Products in Adverse Conditions?
The idea of a “kill chip”—a hidden mechanism that allows a manufacturer to remotely disable or degrade a product—is not purely science fiction. While no confirmed cases exist of such chips being deployed in commercial products, the technology, motives, and risks make it a plausible (though extreme) tactic in trade wars or geopolitical conflicts.
- Technical Feasibility: How “Kill Chips” Could Work
- Hardware-Based Kill Switches
- Embedded Microcontrollers: A secondary chip could be designed to receive a signal (via Wi-Fi, Bluetooth, or cellular) and trigger a failure (e.g., overheating, voltage spike).
- Firmware Backdoors: Pre-installed malware in a device’s firmware could execute a “self-destruct” command if activated.
- Time-Based Degradation: Some chips already have planned obsolescence features (e.g., slowing down after a set period). A more aggressive version could render hardware unusable.
Example:
- In 2018, reports surfaced that Chinese-made surveillance chips (used in U.S. military equipment) had hidden backdoors for remote access. While not a “kill switch,” the risk was similar .
- Software-Based Sabotage
- OTA (Over-the-Air) Updates: Companies like Tesla can push software updates that disable features or reduce performance.
- DRM Lockouts: Some printers and industrial machines already refuse to function if they detect “unauthorized” parts.
Example:
- Russia’s Kamaz trucks (used in Ukraine) reportedly had French-made engine control units (ECUs) that could be remotely disabled. After sanctions, Russia had to replace them with domestic chips .
- Geopolitical Precedents & Motivations
- Why Would a Country Do This?
- Economic Warfare:
- If a nation (e.g., China) dominates a critical supply chain (e.g., chips, EVs, drones), it could threaten to disable exports during a trade war.
- Example: If China controlled 90% of global EV batteries, it could theoretically brick them if the U.S. imposed extreme sanctions.
- Military Sabotage:
- State-sponsored kill chips could disable enemy weapons, drones, or communication systems in wartime.
- Example: The U.S. has reportedly tested cyberweapons to disable North Korean missile systems mid-flight .
- Coercive Diplomacy:
- A “kill switch” could be used to force compliance in negotiations (e.g., “Lift sanctions, or we disable your infrastructure”).
- Real-World Parallels
- Stuxnet (2010): A U.S.-Israeli cyberweapon physically destroyed Iranian nuclear centrifuges by overloading them.
- Huawei Backdoor Fears (2019): The U.S. banned Huawei over concerns its 5G equipment could be remotely controlled by Beijing.
- Risks & Countermeasures
- Why It is Rare (So Far)
- Blowback Risk:
- If a kill switch were exposed, global buyers would boycott the offending country’s products.
- Example: After the SolarWinds hack, Russian software faced global distrust.
- Legal Consequences:
- Sabotaging commercial products could trigger WTO disputes, sanctions, or even war crimes charges.
- Detection & Mitigation:
- Reverse engineering (e.g., by Apple, Tesla, or defense contractors) can uncover hidden kill mechanisms.
- Countries like the U.S. now scan imported chips for malware at Customs .
- How Nations Protect Themselves
- Onshoring Critical Tech: The U.S. CHIPS Act ($52B) and EU Chips Act (€43B) aim to reduce reliance on foreign semiconductors.
- Air-Gapped Systems: Military and infrastructure networks avoid internet-connected chips.
- Open-Source Hardware: Some governments mandate transparent chip designs to prevent backdoors.
- Future Outlook: A New Era of “Hardware Wars”?
- China’s Dominance in Legacy Chips: If it controls 60% of global chip production, could it embed kill switches in industrial machinery?
- AI-Enabled Sabotage: Future chips with AI could autonomously decide to fail if geopolitical conditions change.
- Counter-Kill Switch Tech: Firms like Lockheed Martin are developing “self-healing” electronics to resist sabotage.
Conclusion
While no confirmed “kill chips” have been deployed in trade wars yet, the technology exists, and the geopolitical incentives are growing. Nations are already preparing for this scenario by:
✔ Localizing chip production (e.g., TSMC in Arizona)
✔ Scanning imports for malware
✔ Developing cyber-resilient hardware
Final Thought: The line between trade war and cyberwar is blurring—future conflicts may be fought not just with tariffs, but with silicon sabotage.
Case Studies: How “Kill Chips” Could Sabotage EVs, Civilian Planes, and Drones
The concept of embedded sabotage mechanisms in critical technologies is a growing concern, especially in industries dominated by geopolitical rivals. Below are detailed scenarios for electric vehicles (EVs), civilian aircraft, and drones (both surveillance and military), analyzing feasibility, real-world precedents, and potential countermeasures.
- Electric Vehicles (EVs): Battery & Software Sabotage
Why EVs Are Vulnerable
- Battery Dependence: China controls 70%+ of global lithium-ion battery production.
- Connected Systems: Most EVs rely on OTA (Over-the-Air) updates for performance tuning.
Possible Sabotage Methods
| Method | How It Works | Real-World Precedent |
| Battery Performance Throttling | Remote command reduces range or disables charging. | Tesla’s “Battery Gate” (2019) slowed older cars via software. |
| Thermal Runaway Trigger | Malicious firmware causes batteries to overheat, risking fires. | LG Chem batteries in Chevy Bolts were recalled for fire risks (2021). |
| Geofencing Lockout | EVs refuse to operate in certain regions (e.g., during sanctions). | Russian Kamaz trucks had French ECUs that failed post-sanctions. |
Potential Impact
- Economic Warfare: If China dominates EV supply chains, it could disable exports during a trade war.
- Consumer Panic: A single incident (e.g., mass battery failures) could collapse trust in foreign EVs.
Countermeasures
✔ Localized battery production (e.g., U.S. Inflation Reduction Act subsidies).
✔ Open-source firmware audits to detect backdoors.
- Civilian Aircraft: Hidden Kill Switches in Avionics
Why Planes Are at Risk
- Global Supply Chains: Boeing/Airbus rely on foreign-made chips and composites.
- Critical Software: Modern planes use fly-by-wire systems controlled by code.
Possible Sabotage Methods
| Method | How It Works | Real-World Precedent |
| Firmware Backdoor | Malicious code disables engines mid-flight when triggered. | Stuxnet (2010) physically destroyed Iranian centrifuges. |
| GPS Spoofing | Fake coordinates cause navigation failures. | China has tested GPS spoofing near Taiwan (2023). |
| Component Degradation | Substandard parts (e.g., turbine blades) fail prematurely. | FAA banned some Chinese-made aircraft parts (2022). |
Potential Impact
- Airline Groundings: A single incident could ground entire fleets (like the 737 MAX crisis).
- Geopolitical Leverage: A state could threaten to disable rival airlines during conflicts.
Countermeasures
✔ Dual-supplier policies (e.g., Boeing diversifying away from Chinese composites).
✔ Air-gapped maintenance systems to prevent remote hacking.
- Drones: Surveillance & Military Sabotage
Why Drones Are Prime Targets
- Dual-Use Tech: Civilian drones (DJI) share components with military models.
- Remote Control: Most rely on proprietary software vulnerable to kill commands.
Possible Sabotage Methods
| Type | Sabotage Method | Real-World Precedent |
| Surveillance Drones (e.g., DJI) | “Geofencing” blocks operation in conflict zones. | DJI drones already restrict flight near airports/military sites. |
| Military Drones | Firmware update disables guidance systems mid-mission. | Ukraine repurposed DJI drones with hacked firmware. |
| Swarm Drones | Kill command causes swarm to self-destruct or attack friendly forces. | Iran spoofed U.S. drone GPS (2011), forcing a crash. |
Potential Impact
- Battlefield Disruptions: Imagine 1,000 drones failing simultaneously during a Taiwan invasion.
- Corporate Espionage: A hacked industrial drone could leak sensitive site data (e.g., oil refineries).
Countermeasures
✔ Military-grade encryption (e.g., U.S. banning DJI drones for govt use).
✔ “Dumb” drones (manual controls only, no OTA updates).
- The Bigger Picture: Are Kill Chips Already in Use?
While no overt cases exist, circumstantial evidence suggests covert testing:
- Huawei 5G Backdoor Fears: U.S. claims Chinese telecom gear could be remotely disabled.
- Russia’s Kamaz Trucks: French ECUs failed post-sanctions, forcing manual replacements.
- Stuxnet: Proves states will weaponize firmware when stakes are high.
Future Threats
- AI-Enabled Sabotage: Chips could autonomously decide to fail based on news feeds (e.g., “If China invades Taiwan, disable all exports”).
- Supply Chain Attacks: A single compromised chip factory could infect millions of devices.
Conclusion: Preparing for Silicon Sabotage
| Industry | Greatest Risk | Best Defense |
| EVs | Battery/software kill switches | Localized production |
| Aircraft | Firmware backdoors | Air-gapped systems |
| Drones | Remote deactivation | Open-source firmware |
Final Thought: The next trade war may not just raise prices—it could brick entire industries overnight. Nations are already reacting:
- U.S. CHIPS Act ($52B to onshore semiconductors).
- EU’s Critical Raw Materials Act (reducing reliance on Chinese batteries).
- India’s Drone Policy (banning Chinese components).
It is to be noted that intensive cybersecurity, as well as physical security, measures are implemented by Boeing and Airbus as well as Chinese civilian aircraft manufacturer with reference to safeguarding
- Intellectual Property of these companies
- Spyware, Kill Switches safeguarding and Malware protection
- Analysing avionic equipment for Kill Switches
- How can these malactions be diagnosed and prevented?
How Military Aircraft Manufacturers Can Prevent Chip Sabotage in Third-Party Components
Military aircraft manufacturers (e.g., Lockheed Martin, Boeing, Dassault, Sukhoi) rely on global supply chains for critical components, including semiconductors. However, foreign-made chips could contain hidden kill switches, backdoors, or malware designed to sabotage aircraft in a conflict. Here’s how defense firms mitigate these risks:
- Supply Chain Vetting & “Trusted Foundries”
- Strict Supplier Certification
- US DoD’s “Trusted Foundry” Program: Only approved fabs (e.g., Intel, GlobalFoundries) supply chips for sensitive defence systems.
- NATO/EU “Cyber Resilience” Standards: Suppliers must prove no foreign state influence (e.g., banning Chinese-owned SMIC).
- Component Traceability
- Blockchain Tracking: Some firms use blockchain to log each chip’s origin, testing, and installation.
- X-Ray & Decapsulation: Suspect chips are physically inspected for tampering.
Example:
- The F-35’s Turkish ejection seat crisis (2019) led to a full audit of all foreign-supplied components.
- Secure Chip Design & Redundancy
- Custom ASICs (No Off-the-Shelf Chips)
- Military jets use radiation-hardened, proprietary chips (e.g., BAE Systems’ RH-series) instead of commercial CPUs.
- FPGAs (Field-Programmable Gate Arrays) can be reconfigured to disable suspicious circuits.
- “Dumb” Backup Systems
- Critical systems (e.g., flight controls) have non-digital backups (hydraulic/mechanical overrides).
- Example: The F-16’s analog flight control still works if digital systems fail.
- Firmware & Software Safeguards
- Air-Gapped Updates
- No OTA (over-the-air) updates—firmware is manually installed via secure terminals.
- Example: F-22 Raptor software is updated only in shielded hangars.
- Checksum & Cryptographic Signing
- All firmware must pass SHA-256/512 hash verification before installation.
- Example: Eurofighter Typhoon uses NATO-certified crypto modules.
- “Self-Destruct” If Tampered
- Some military chips erase their firmware if unauthorized access is detected.
- Testing & Counter-Sabotage Measures
- “Red Team” Hacking
- Ethical hackers simulate attacks (e.g., triggering fake kill commands) to find vulnerabilities.
- EMP & Radiation Testing
- Chips are bombarded with electromagnetic pulses (EMP) to ensure they don’t fail catastrophically.
- “Golden Unit” Comparison
- A reference chip (kept in a vault) is compared to new batches for discrepancies.
- Legal & Geopolitical Strategies
- “No Chinese Components” Clauses
- Contracts ban suppliers from using Chinese-made chips, even in subcomponents.
- Onshoring Critical Production
- U.S. CHIPS Act funds Intel/TSMC fabs in Arizona to reduce reliance on Asia.
- EU’s Chips Act subsidizes STMicroelectronics for local production.
- Export Controls
- ITAR (Intl. Traffic in Arms Regs): Stops adversaries from buying sensitive tech.
Real-World Failures & Lessons
| Incident | What Went Wrong | Fix Implemented |
| Russian Su-35s with French Chips (2022) | Sanctions disabled navigation systems. | Switched to domestic chips. |
| Chinese-made chips in U.S. drones (2018) | Suspected backdoors found. | Pentagon banned DJI drones. |
| F-35 Turkish parts ban (2019) | Geopolitical risk from Ankara. | Replaced with U.S./UK suppliers. |
Conclusion: The Future of Anti-Sabotage Chips
- AI-Enhanced Detection: Machine learning scans chip designs for hidden kill logic.
- Quantum Encryption: Unhackable firmware signing (DARPA is testing this).
- 3D-Printed Chips On-Demand: Print trusted chips in secure facilities.
Military aircraft makers cannot eliminate third-party risks entirely—but through design, testing, and supply chain control, they reduce sabotage chances to near zero. Special security measures are in place to minimize, but not completely eliminate breaches in the manufacturing processes of specific military aircraft (e.g., F-35, Su-57) and their chip security? These measures are not made public and form part of the cyber security division of these companies.
Can In-House Sabotage Occur in Chip Manufacturing Plants?
Insider sabotage is a real threat in semiconductor manufacturing, especially in facilities producing chips for military, aerospace, or critical infrastructure. Bank clients experience with a cloned Visa card (likely due to a compromised payment terminal or skimming device) is a small-scale example, similar risks exist in chip fabs, but with far greater consequences.
- How Employees Could Sabotage Chip Production
- Physical Tampering
- Defective Masking: A malicious engineer could tweak photolithography masks to introduce microscopic flaws in chips.
- Contamination: Introducing impurities (e.g., dust, chemicals) into cleanrooms to cause chip failures.
- “Kill Switch Chip” Implants: Adding hidden circuits that activate under specific conditions (e.g., a signal, date, or voltage trigger).
Real-World Example:
- 2008 Taiwan DRAM Sabotage: A disgruntled engineer at ProMOS (a DRAM manufacturer) allegedly altered equipment settings, causing $50M in losses.
- Firmware/Software Sabotage
- Backdoored Firmware: An insider could insert malicious code into chip firmware (e.g., disabling a drone’s guidance system).
- Test Manipulation: Skipping or falsifying quality tests to let defective chips slip through.
Example:
- Stuxnet (2010): While not insider sabotage, it proved firmware attacks can physically destroy hardware.
- Intellectual Property Theft
- Stealing Designs: Employees could leak chip blueprints to foreign adversaries (e.g., China’s SMIC accused of IP theft from TSMC).
- Reverse Engineering: Taking proprietary chip designs to a competitor.
Example:
- 2019 TSMC vs. SMIC Lawsuit: A former TSMC engineer took secrets to China’s SMIC, leading to a $200M settlement.
- Why Chip Fabs Are Vulnerable to Insider Threats
- High Expertise Needed: Only a few engineers understand chip manufacturing, making oversight difficult.
- Global Workforce: Employees from rival nations (e.g., China, Russia) may have divided loyalties.
- Complex Supply Chains: Hard to track if a single worker tampers with a batch.
- How Companies Prevent Insider Sabotage
- Strict Personnel Vetting
- Background Checks: Extreme scrutiny for employees handling sensitive tech (e.g., TSMC’s 6-month vetting for R&D staff).
- Citizenship Restrictions: Some U.S. fabs (e.g., Intel’s Ohio plant) limit foreign nationals in critical roles.
- Surveillance & Access Control
- AI Monitoring: Cameras track unusual behavior (e.g., someone accessing restricted areas at odd hours).
- Air-Gapped Networks: No USB drives or internet access in secure zones.
- Redundancy & Verification
- Golden Samples: A “reference chip” is compared to production batches for discrepancies.
- Multi-Person Authentication: Critical steps require two engineers to approve.
- Legal Deterrents
- NDAs & Non-Compete Clauses: Heavy penalties for leaks (e.g., 10+ years in prison for stealing trade secrets).
- Whistleblower Rewards: Incentives for reporting suspicious activity.
- Real-World Cases of Chip Industry Sabotage
| Incident | What Happened | Outcome |
| Samsung Fab Sabotage (2014) | Worker allegedly damaged equipment, costing $1M. | Fired + blacklisted. |
| UMC vs. Micron (2018) | Employees stole DRAM tech for China. | UMC fined $60M. |
| Chinese Spy at Apple (2018) | Employee tried stealing self-driving car secrets. | Arrested by FBI. |
- Could a civilian Visa Credit Card Incident Happen in a Chip Fab?
- Yes, but scaled up:
- Visa bank cards are cloned via physical/digital skimming (a low-tech attack).
- In a chip fab, a rogue insider could alter millions of chips with a single tweak.
- Difference:
- Banks detect fraud via AI and refund victims.
- A sabotaged military chip could fail mid-combat, causing deaths.
Conclusion: Insider Threats Are a Silent War
While companies invest heavily in security, determined insiders (disgruntled employees, spies, or coerced workers) remain a risk.
The best defenses are:
✔ Extreme vetting (like TSMC’s 6-month background checks).
✔ Air-gapped production lines (no external connections).
✔ AI-powered anomaly detection (catches sabotage early).
Final Thought: Just as the bank improved security after clients’ cards’ were cloned, chip fabs must evolve constantly to stay ahead of saboteurs, inhouse.
How Insider Sabotage in Chip Manufacturing Ties into Trade Wars
The risk of insider sabotage in semiconductor fabs is not just a corporate security issue—it’s a geopolitical weapon in modern trade wars. Here’s how it connects:
- Trade Wars Create Incentives for Sabotage[20]
- Retaliation Against Sanctions
- If Country A bans chips from Country B (e.g., U.S. blacklisting SMIC), Country B may coerce or recruit insiders to sabotage rival fabs.
- Example: A Chinese engineer at TSMC could deliberately weaken chips destined for U.S. fighter jets.
- Economic Espionage
- Trade wars accelerate IP theft to bypass R&D costs.
- Example: China’s “Made in China 2025” relies partly on stolen semiconductor tech.
- Supply Chain Attacks
- A single compromised worker can taint entire shipments, forcing reliance on domestic suppliers.
- Example: If Intel’s Malaysia plant had a saboteur, the U.S. might push to reshore production.
- Real-World Trade War Links
| Incident | Trade War Connection | Impact |
| Huawei’s Alleged Backdoors (2019) | U.S. banned Huawei, fearing sabotage. | Global telecoms dropped Chinese 5G gear. |
| SMIC’s Stolen TSMC Tech (2019) | China needed advanced chips amid U.S. sanctions. | SMIC accelerated 7nm production illegally. |
| Russian Microchip Shortage (2022) | Sanctions forced Russia to use counterfeit chips in missiles. | High failure rates in Ukraine war. |
- How Nations Counter Insider Threats
- Export Controls & Blacklists
- U.S. Entity List: Bans firms like SMIC from American tech, reducing sabotage risks.
- EU’s Chips Act: Funds local fabs to avoid reliance on adversarial suppliers.
- “Trusted Foundry” Programs
- Only vetted fabs (e.g., Intel, GlobalFoundries) can make chips for defense.
- Worker Surveillance
- China: Mandates loyalty checks for tech employees.
- U.S.: Restricts foreign nationals in sensitive fabs.
- The Future: Trade Wars = Silicon Spy Games
- AI-Driven Sabotage Detection: Fabs will use AI to spot suspicious behavior.
- Chip Passports: Blockchain tracks each component’s origin.
- Onshoring Arms Race: U.S./EU/China spend billions to control their own fabs.
Bottom Line: Insider sabotage is now a trade war tactic—nations must secure chips like they secure borders.
Countries Leading in Semiconductor Manufacturing (2025)
The global semiconductor industry is dominated by a few key nations, with Taiwan, South Korea, the U.S., China, and Japan accounting for the majority of production. Below is a breakdown of the top chip-manufacturing countries, along with insights into South Africa’s emerging role.
- Top Semiconductor Manufacturing Countries
| Rank | Country | Key Players | Market Share (2025) | Notable Fact |
| 1 | Taiwan | TSMC, UMC | ~50% of global output | TSMC alone makes 50% of the world’s advanced chips (≤3nm). |
| 2 | South Korea | Samsung, SK Hynix | ~17% (Foundry + Memory) | Leads in DRAM/NAND flash memory. |
| 3 | United States | Intel, Micron, GlobalFoundries | ~12% (but 46% in sales) | CHIPS Act aims to triple U.S. production by 2032. |
| 4 | China | SMIC, Huawei’s HiSilicon | ~9% (growing to 25% by 2030) | Heavy investment in self-sufficiency. |
| 5 | Japan | Tokyo Electron, Renesas, Sony | ~4% (Advanced nodes) | Dominates semiconductor materials (50% global supply). |
| 6 | Germany | Infineon, Bosch | ~3% (Automotive chips) | Key in power semiconductors. |
| 7 | Netherlands | ASML (Lithography machines), NXP | ~2% (Equipment focus) | ASML is the sole maker of EUV lithography machines. |
| 8 | Israel | Tower Semiconductor (Intel-owned) | ~1% (Specialized fabs) | Strong in analog & RF chips. |
| 9 | Malaysia | Infineon, Osram | ~1% (Packaging & testing) | Major backend production hub. |
| 10 | Singapore | GlobalFoundries, Micron | ~1% (Mature nodes) | Key for legacy chip production. |
Other Notable Regions:
- India – Expanding with Tata Group’s new fabs.
- France/Italy – STMicroelectronics leads in automotive chips.
- Kenya – New U.S. partnership to build Africa’s first major fab 13.
- South Africa’s Semiconductor Industry
While South Africa is not yet a major chip producer, it is taking steps to enter the semiconductor value chain:
- Current Landscape
- No large-scale fabs, but several electronics distributors & design firms:
- Infineon Davitron (power management ICs).
- Vepac Electronics (power supplies, sensors).
- ChipLab (education & chip design training).
- Future Prospects
- First Chip Plant Plans – A partnership between OAO Investments and ChipLab aims to establish Africa’s first semiconductor fab, focusing on:
- Training local engineers (60% women target).
- Producing legacy chips (28nm+) for IoT, automotive.
- U.S.-Kenya Semiconductor Deal – Could spur regional growth, with South Africa benefiting from spillover investments.
- Critical Minerals – South Africa has reserves of gallium, germanium, and rare earths needed for chipmaking.
- Challenges
- Lack of existing infrastructure (no advanced fabs).
- Dependence on imports for high-end chips.
- Global competition from established players like TSMC/Samsung.
- Key Takeaways
✅ Taiwan, South Korea, and the U.S. dominate chipmaking.
✅ China is rapidly catching up, aiming for 25% global output by 2030.
✅ South Africa is in early stages, but initiatives like ChipLab could position it as a future niche player.
✅ Africa’s first major fab may emerge in Kenya, with ripple effects for South Africa.
For further reading, the following are recommended:
Types of non-edible semiconductor chip categories that power modern technology, excluding the crispy potato snack variety:
- By Function (Core Types)
| Category | Purpose | Examples | Key Players |
| Logic Chips | Process instructions (CPU/GPU/AI) | Intel Core i9, Nvidia H100 GPU | Intel, AMD, Nvidia, Apple |
| Memory Chips | Store data (volatile/non-volatile) | Samsung DRAM, Micron NAND Flash | Samsung, SK Hynix, Micron |
| Analog Chips | Process real-world signals (sound/power) | Texas Instruments power management ICs | TI, Analog Devices, Infineon |
| RF/Wireless Chips | Enable communications (5G/Wi-Fi/Bluetooth) | Qualcomm Snapdragon, Broadcom Wi-Fi | Qualcomm, Broadcom, MediaTek |
| Sensor Chips | Detect environmental inputs | Bosch MEMS accelerometers, Sony CMOS | Bosch, Sony, STMicro |
- By Manufacturing Node (Size)
| Node (nm) | Use Case | Leader | Example Products |
| ≤3nm | Cutting-edge AI/Phones | TSMC | Apple A18 Pro, Nvidia B100 |
| 7-14nm | Mid-range processors | Samsung | AMD Ryzen, Google Tensor |
| 28-90nm | Automotive/IoT | SMIC | Tesla FSD chips, ESP32 MCUs |
| >90nm | Power/legacy systems | Infineon | Industrial motor controllers |
- By Specialization (Niche Applications)
| Type | Unique Role | Example |
| ASICs | Custom-designed for one task (e.g., Bitcoin mining) | Bitmain Antminer chips |
| FPGAs | Reconfigurable circuits (military/AI) | Xilinx FPGAs in F-35 jets |
| SoCs | All-in-one chips (phone/tablet brains) | Qualcomm Snapdragon, Apple M-series |
| Optical Chips | Light-based computing (future AI) | Ayar Labs’ photonic processors |
| Quantum Chips | Next-gen encryption/computing | IBM Quantum Heron |
- By Material (Beyond Silicon)
| Material | Advantage | Applications |
| GaN (Gallium Nitride) | Faster switching, less heat | 5G base stations, EV chargers |
| SiC (Silicon Carbide) | High-voltage endurance | Tesla powertrains, solar inverters |
| Graphene (Experimental) | Ultra-fast electrons | Future flexible electronics |
South Africa’s Emerging Role
While not yet a chip manufacturer, South Africa is focusing on:
- Legacy chip design (28nm+ for IoT)
- Critical minerals (gallium/germanium for GaN/SiC chips)
- Chip packaging (potential niche via partnerships)
The Bottom Line
The Bottom Line is that there is an ongoing global tension, with reference to CHIPS. The “cold chip war” is a covert peace disruption. It is not just about making the minutest transistors, capable of storing and processing the maximum terabytes of information, in the quickest possible time. It is about controlling specialized categories (e.g., AI logic chips vs. automotive power chips). South Africa could carve out a role in mature-node analog/power chips leveraging local minerals, of which it has an abundant supply on both underground, in local mines, as well as the possible presence of most valuable, Rare-Earth Elements [21]in the numerous old mine dumps, scattered throughout the Province of Gauteng and elsewhere. The technology was unavailable at the time when gold, diamonds and other minerals were discovered, but today, the technology and expertise is at hand and it only needs government coordination, locally available expertise and finance to exploit these, much needed, globally valuable resources. South Africa does have rare earth minerals. According to the U.S. Geological Survey, South Africa contains 23 rare earth-bearing minerals. These are most sought-after entities in the chip manufacturing industry and are primarily found in mineral-rich regions such as the Bushveld Complex and Steenkampskraal in the Western Cape[22], which is one of the richest thorium and rare earth deposits globally. South Africa is one of the most mineral-rich countries in the world. A list of key minerals found in the country are:
- Gold
- Platinum Group Metals (PGMs) – platinum, palladium, rhodium, etc.
- Diamonds
- Coal
- Chromium
- Manganese
- Iron Ore
- Copper
- Uranium
- Zirconium
- Vanadium
- Titanium
- Silver
- Beryllium
- Limestone
- Ilmenite, Rutile, and Zircon (heavy minerals)
South Africa has over 70 types of minerals with proven reserves.
Gold was first discovered in 1871 in Barberton, Mpumalanga. However, the major gold rush began in 1886 when George Harrison discovered gold on the Witwatersrand Reef near present-day Johannesburg. This discovery led to the founding of Johannesburg and transformed South Africa into the world’s largest gold producer for much of the 20th century.[23]
Diamonds were first discovered in 1867 near the Orange River, close to Hopetown in the Northern Cape.[24] The most famous early find was the Eureka Diamond[25], It originally weighed 21.25 carats (4.250 g), and was later cut to a 10.73-carat (2.146 g) cushion-shaped brilliant, which is currently on display at the Mine Museum in Kimberley. followed by the discovery of the Star of South Africa in 1869. These discoveries led to the establishment of Kimberley, which became the epicentre of the diamond rush and the birthplace of the modern diamond industry. Diamonds are used in the Diamond Chips, as they are virtually indestructible and durable. This technology was prompted by the Fukushima Nuclear Disaster.

An old Gold Mine Dump in Johannesburg, Gauteng, South Africa, which is reworked for REEs, using modern technology. Note the Johannesburg City CBD Skyline with high rise skyscrapers, including the 50 storey Carlton Centre.
Photo Credit : Wikimedia Commons
What is in the Old Mine Dumps[26]?
There is growing interest and evidence suggesting that old mine dumps in Johannesburg, particularly those from the Witwatersrand goldfields, may contain rare earth elements (REEs) along with other valuable minerals. The legacy gold mine dumps around Johannesburg, remnants of over a century of gold mining contain:
- Residual gold (still being reprocessed in some areas)
- Uranium
- Heavy metals (like lead, arsenic, and cadmium)
- Rare Earth Elements (REEs) – recent studies and exploratory projects have identified the potential presence of REEs in the tailings and slimes dams
Why Are REEs There?
During early gold extraction (especially pre-1950s), the technology was not advanced enough to extract all valuable elements. As a result:
- REEs and other trace elements were discarded with the tailings.
- These dumps now represent a secondary source of critical minerals, especially as global demand for REEs increases for use in electronics, green energy, and defence technologies.
Environmental and Economic Implications
- Environmental: These dumps are a source of acid mine drainage, dust pollution, and heavy metal contamination.
- Economic: Reprocessing them could be economically viable and environmentally beneficial if done responsibly.

The Hyperchip: How Intel makes chips from raw earth sand to integrated circuits.
Photo credit: Wikimedia commons
References:
[1] Author’s personal quote May 2025
[2] https://www.linkedin.com/pulse/non-edible-chips-wafers-vidya-shah
[3] semiconductors pdf – Search
[4] the pascaline calculator – Search
[5] https://en.wikipedia.org/wiki/Analytical_Engine
[6] https://www.bing.com/search?q=Definition%20of%20Full%20Conductor&qs=n&form=QBRE&sp=-1&lq=0&pq=definition%20of%20full%20conductor&sc=5-28&sk=&cvid=098580D135D140DBA701DD15FEA41888efinition of Computer Chip – Search
[7] https://www.bing.com/search?q=Definition%20of%20Full%20Conductor&qs=n&form=QBRE&sp=-1&lq=0&pq=definition%20of%20full%20conductor&sc=5-28&sk=&cvid=098580D135D140DBA701DD15FEA41888
[8] Inventors of Computer Chips – Search
[9] AMD EPYC 9965 Specs | TechPowerUp CPU Database
[10] TRANSCEND MEDIA SERVICE » Global Peace Disruption: The Trump Trade Wars 2025
[11] https://www.bing.com/ck/a?!&&p=487190f1e480f0af88d6a7bf2a8d16dfb1db0f69accd8f203e7c0734df5023cfJmltdHM9MTc0ODA0NDgwMA&ptn=3&ver=2&hsh=4&fclid=0c3c9d6e-714f-6e96-05f4-88d2706c6f48&psq=Designed+in+the+U.S.+(Nvidia)&u=a1aHR0cHM6Ly9hcG5ld3MuY29tL2FydGljbGUvbnZpZGlhLWFpLWFydGlmaWNpYWwtaW50ZWxsaWdlbmNlLXRhcmlmZnMtZGNmNDgxMTJjZTk4YTdiNjFiZmQzMjE1NzM1OWNlMmY&ntb=1
[12] https://www.bing.com/ck/a?!&&p=0d28070d8ac7bdda0c18dd862d6ec4a351af4d2caedec976a4c85f1306875a4dJmltdHM9MTc0ODA0NDgwMA&ptn=3&ver=2&hsh=4&fclid=0c3c9d6e-714f-6e96-05f4-88d2706c6f48&u=a1L25ld3Mvc2VhcmNoP3E9VFNNQytBbmQrVHJ1bXArVHJhZGUrV2FycyZxcHZ0PVRTTUMrYW5kK3RydW1wK3RyYWRlK3dhcnMmRk9STT1FV1JF&ntb=1
[13] https://www.bing.com/ck/a?!&&p=81352f32de0fdc19bff17f450de8840e1518076099478a56825c915eeb3ec138JmltdHM9MTc0ODA0NDgwMA&ptn=3&ver=2&hsh=4&fclid=0c3c9d6e-714f-6e96-05f4-88d2706c6f48&psq=TSMC+and+trump+trade+wars&u=a1aHR0cHM6Ly93d3cubW9uZXljb250cm9sLmNvbS93b3JsZC90c21jLWhpdHMtYmFjay1hdC11cy13YXJucy10YXJpZmZzLWNvdWxkLWRlcmFpbC0xNjUtYmlsbGlvbi1hcml6b25hLWludmVzdG1lbnQtYXJ0aWNsZS0xMzA0NDM2MS5odG1s&ntb=1
[14] https://www.bing.com/ck/a?!&&p=10cf798abd7d2ad2e0a6d38008b3bd4073e2491321d552f985459c81c6c42facJmltdHM9MTc0ODA0NDgwMA&ptn=3&ver=2&hsh=4&fclid=0c3c9d6e-714f-6e96-05f4-88d2706c6f48&psq=Act%3a+52.7billiontoboostdomesticchipmaking%2ccounteredbyChina%e2%80%99s52.7billiontoboostdomesticchipmaking%2ccounteredbyChina%e2%80%99s150+billion+subsidy+for+SMIC+&u=a1aHR0cHM6Ly9wZXJraW5zY29pZS5jb20vaW5zaWdodHMvdXBkYXRlL2NoaXBzLWFjdC1hbGxvY2F0ZXMtNTItYmlsbGlvbi1zdWJzaWRpZXMtcmV2aXRhbGl6ZS1zZW1pY29uZHVjdG9yLW1hbnVmYWN0dXJpbmc&ntb=1
[15] https://ecipe.org/publications/how-huawei-weathered-the-storm-resilience-market-conditions-or-failed-sanctions/
[16] https://www.bing.com/ck/a?!&&p=5510616d2a783237dcbb1a17068051dd8998fda9426931b5afb2251376b25e46JmltdHM9MTc0ODA0NDgwMA&ptn=3&ver=2&hsh=4&fclid=0c3c9d6e-714f-6e96-05f4-88d2706c6f48&psq=CEPA+on+the+%22Chips+War%22+&u=a1aHR0cHM6Ly9jZXBhLm9yZy9jb21tZW50YXJ5L3BhcnQtZml2ZS1jaGlwcy13YXItMjAyNS8&ntb=1
[17] https://www.bing.com/ck/a?!&&p=adb7298cb774288dd6621892a88ecab09f9aa1d89dcbdab8a5b81168603736feJmltdHM9MTc0ODA0NDgwMA&ptn=3&ver=2&hsh=4&fclid=0c3c9d6e-714f-6e96-05f4-88d2706c6f48&psq=Deloitte%e2%80%99s+2025+Semiconductor+Outlook+&u=a1aHR0cHM6Ly93d3cyLmRlbG9pdHRlLmNvbS91cy9lbi9pbnNpZ2h0cy9pbmR1c3RyeS90ZWNobm9sb2d5L3RlY2hub2xvZ3ktbWVkaWEtdGVsZWNvbS1vdXRsb29rcy9zZW1pY29uZHVjdG9yLWluZHVzdHJ5LW91dGxvb2suaHRtbA&ntb=1
[19] https://www.bing.com/search?q=History%20of%20computers%20-%20from%20the%20Abacus%20to%20the%20iPhone%20–%20Is%20Abacus%20a%20Computer%3F&qs=n&form=QBRE&sp=-1&lq=0&pq=history%20of%20computers%20-%20from%20the%20abacus%20to%20the%20iphone%20–%20is%20abacus%20a%20computer%3F&sc=0-76&sk=&cvid=8C856811790F4A38A6E19BD57E3126C4
[20] https://www.bing.com/search?q=Trade+Wars+Create+Incentives+for+Sabotage&cvid=ef8ca44deb3f4b22af5cd12f095863ad&gs_lcrp=EgRlZGdlKgYIABBFGDkyBggAEEUYOTIICAEQ6QcY_FXSAQkyMTcyNGowajSoAgCwAgA&FORM=ANAB01&PC=U531
[21] TRANSCEND MEDIA SERVICE » Rare Earth Elements: Enter the Dragon-A New Player in the Field of Global Peace Disruptions
[22] Geology of the PGE Deposits in the Bushveld Complex, South Africa | Geology for Investors
[23] The Barberton Gold Rush, Mpumalanga, South Africa
[24] List of Diamond Mines in South Africa – Wiki South Africa
[25] Eureka Diamond – Wikipedia
[26] mine dumps in south africa – Search
______________________________________________
 Professor G. Hoosen M. Vawda (Bsc; MBChB; PhD.Wits) is a member of the TRANSCEND Network for Peace Development Environment.
Professor G. Hoosen M. Vawda (Bsc; MBChB; PhD.Wits) is a member of the TRANSCEND Network for Peace Development Environment.
Director: Glastonbury Medical Research Centre; Community Health and Indigent Programme Services; Body Donor Foundation SA.
Principal Investigator: Multinational Clinical Trials
Consultant: Medical and General Research Ethics; Internal Medicine and Clinical Psychiatry:UKZN, Nelson R. Mandela School of Medicine
Executive Member: Inter Religious Council KZN SA
Public Liaison: Medical Misadventures
Activism: Justice for All
Email: vawda@ukzn.ac.za
Tags: Artificial Intelligence AI, Cold War, Peace, Warfare
This article originally appeared on Transcend Media Service (TMS) on 2 Jun 2025.
Anticopyright: Editorials and articles originated on TMS may be freely reprinted, disseminated, translated and used as background material, provided an acknowledgement and link to the source, TMS: Peace and War 2025: The Hot Chips and Cold Wars (Part 1), is included. Thank you.
If you enjoyed this article, please donate to TMS to join the growing list of TMS Supporters.

This work is licensed under a CC BY-NC 4.0 License.
Join the discussion!
We welcome debate and dissent, but personal — ad hominem — attacks (on authors, other users or any individual), abuse and defamatory language will not be tolerated. Nor will we tolerate attempts to deliberately disrupt discussions. We aim to maintain an inviting space to focus on intelligent interactions and debates.